
Broken Security Lock On Computer Keyboard - Vulnerability Issue In Computing Stock Photo, Picture And Royalty Free Image. Image 28577809.
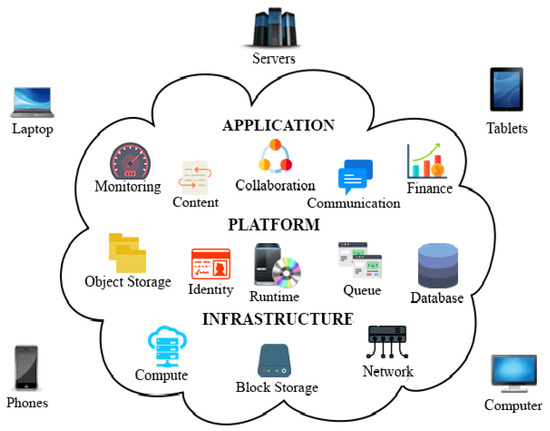
Electronics | Free Full-Text | A Survey on Modern Cloud Computing Security over Smart City Networks: Threats, Vulnerabilities, Consequences, Countermeasures, and Challenges

Guide to Vulnerability Analysis for Computer Networks and Systems (gebundenes Buch) | Tegeler Bücherstube GmbH
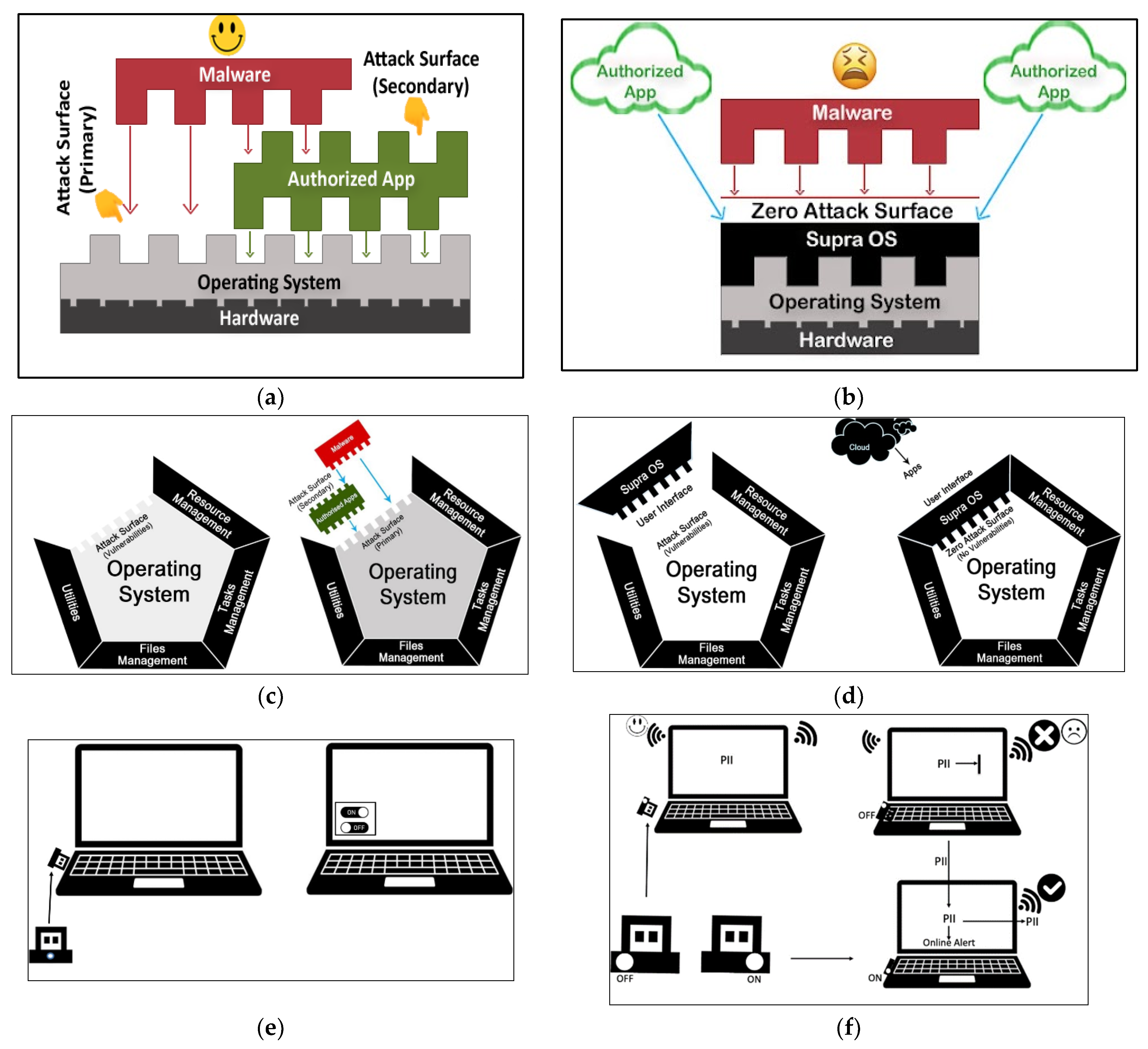
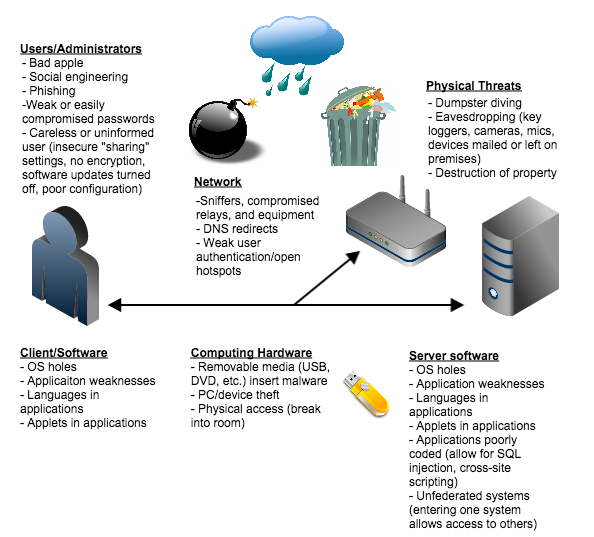
![PDF] Seven Deadly Threats and Vulnerabilities in Cloud Computing | Semantic Scholar PDF] Seven Deadly Threats and Vulnerabilities in Cloud Computing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b5d5225ca66760be413d819f257e8ac618827970/1-Figure1-1.png)















%20(1)%20(1)%20(1)%20(1).png)
![8 Vulnerable Software Apps Exposing Your Computer to Cyber Attacks [Infographic] 8 Vulnerable Software Apps Exposing Your Computer to Cyber Attacks [Infographic]](https://heimdalsecurity.com/blog/wp-content/uploads/70-percent-of-attacks-target-a-vulnerability-on-your-computer-heimdal-security.png)

