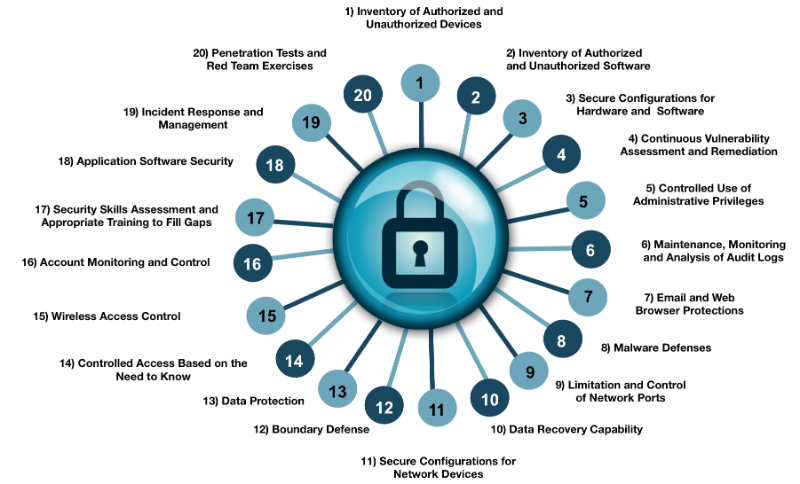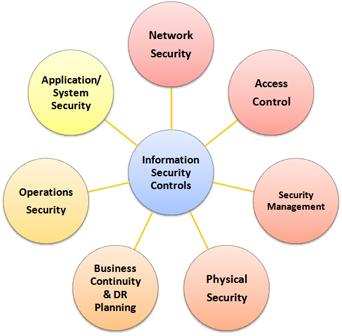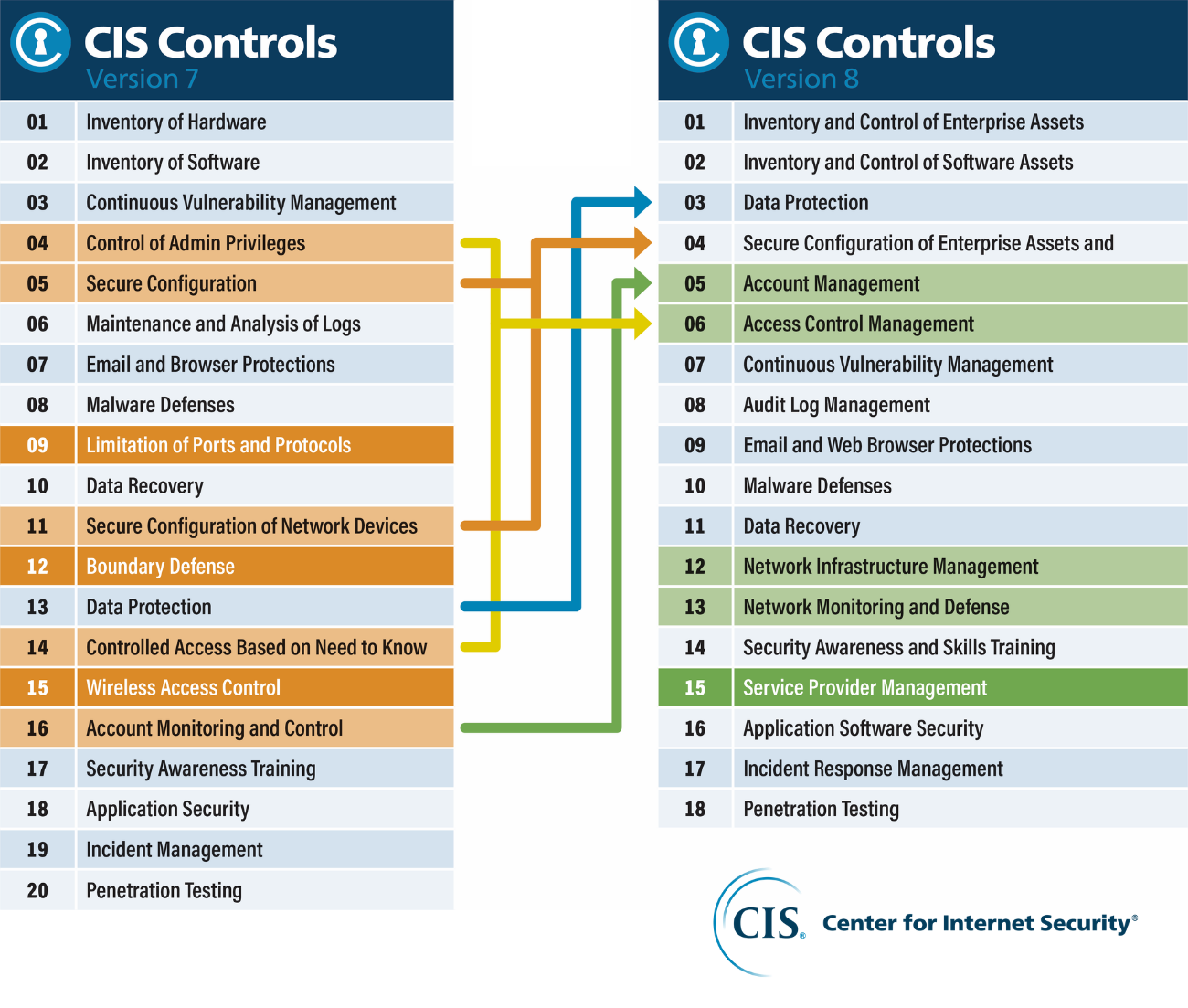
Home protection. Surveillance service. Devices for house security. Access control system, security control solutions, security management concept. Pinkish coral bluevector isolated illustration Stock-Vektorgrafik | Adobe Stock

Computer Applications for Security, Control and System Engineering (kartoniertes Buch) | Buchhandlung am Markt