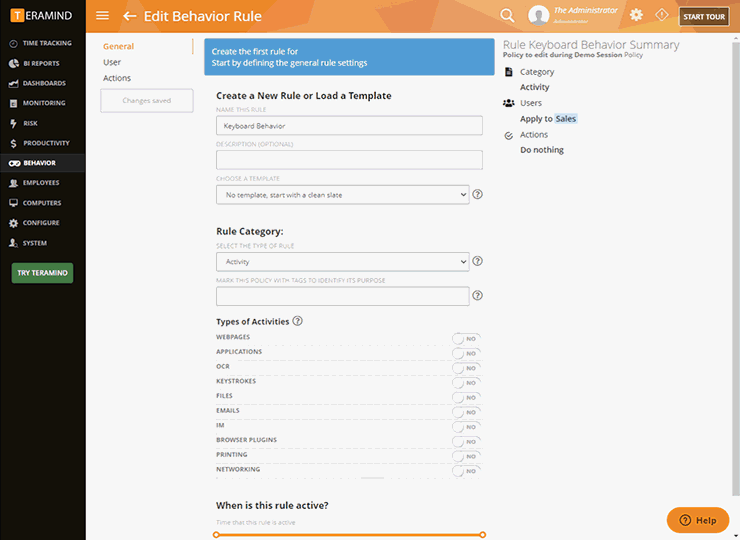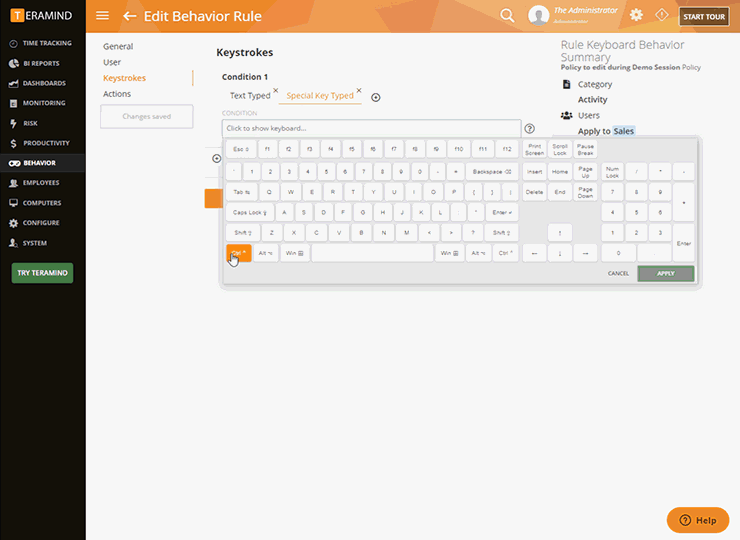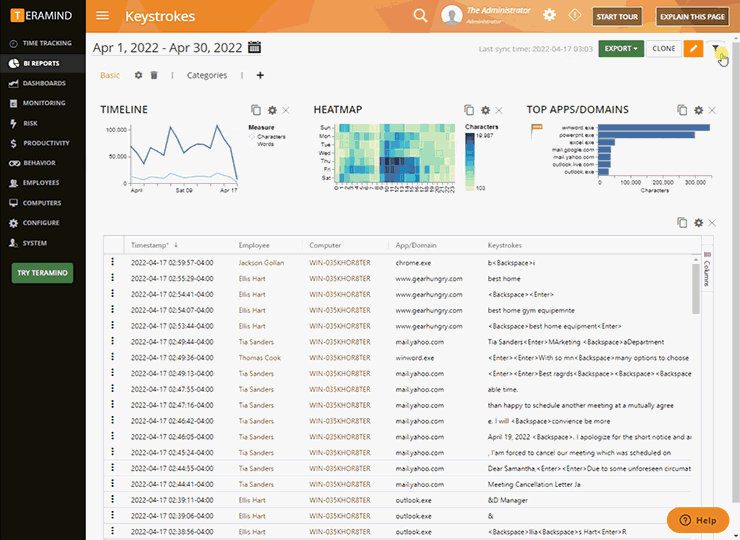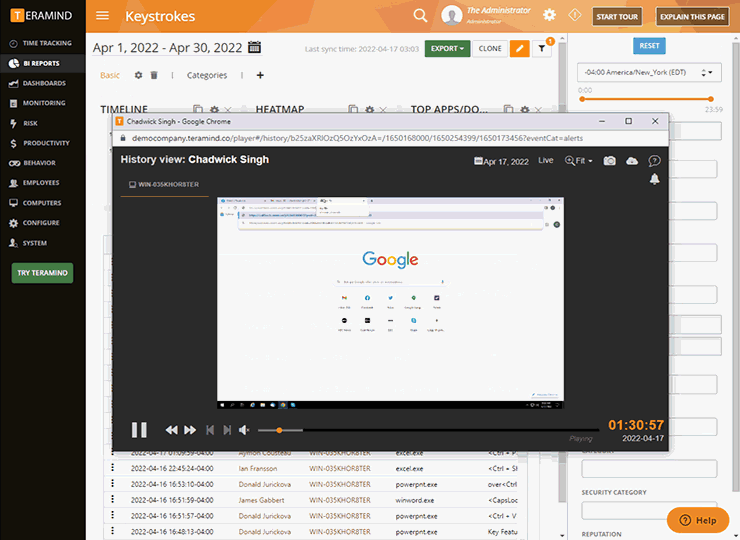
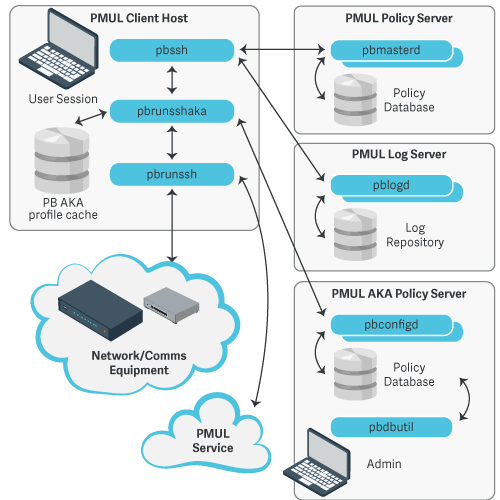
Using Keystroke Authentication Typing Errors Pattern as Non-Repudiation in Computing Forensics | Semantic Scholar
Your Eyes Tell You Have Used This Password Before": Identifying Password Reuse from Gaze and Keystroke Dynamics

Simulating a keystroke in Win32 (C or C++) using SendInput | ad hocumentation • n. fast documentation of ideas and solutions.

Keystroke dynamics‐based user authentication service for cloud computing - Abo‐alian - 2016 - Concurrency and Computation: Practice and Experience - Wiley Online Library

A Wrapper-Based Classification Approach for Personal Identification through Keystroke Dynamics Using Soft Computing Techniques: Security & Forensics Book Chapter | IGI Global

PDF) An investigation into keystroke latency metrics as an indicator of programming performance | Amela Karahasanovic - Academia.edu

Keystroke Dynamic Authentication Using Combined MHR (Mean of Horner's Rules) and Standard Deviation | Kinetik: Game Technology, Information System, Computer Network, Computing, Electronics, and Control

PDF) Implementation Of Long Short-Term Memory (LSTM) For User Authentication Based On Keystroke Dynamics | Sherzod Turaev - Academia.edu

Using Keystroke Authentication Typing Errors Pattern as Non-Repudiation in Computing Forensics | Semantic Scholar