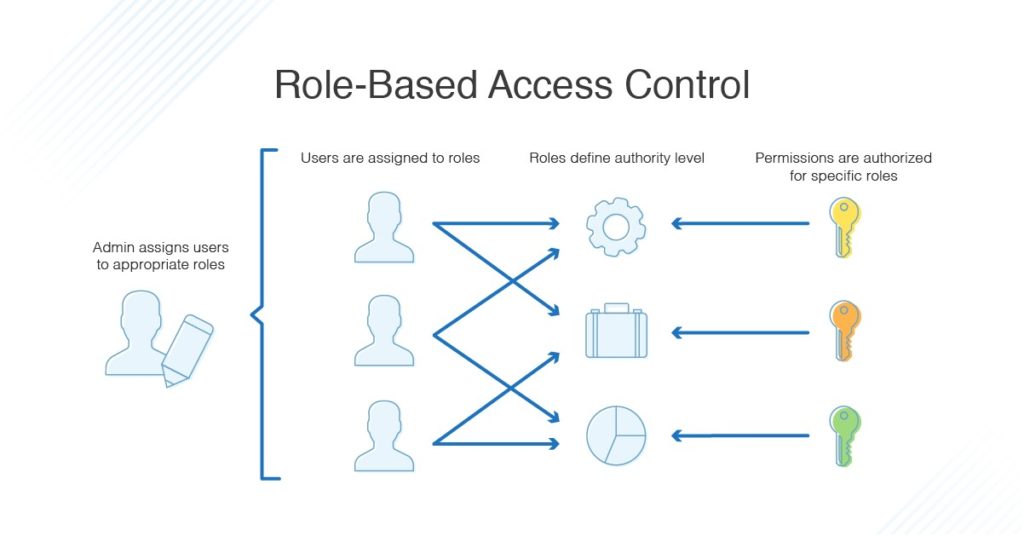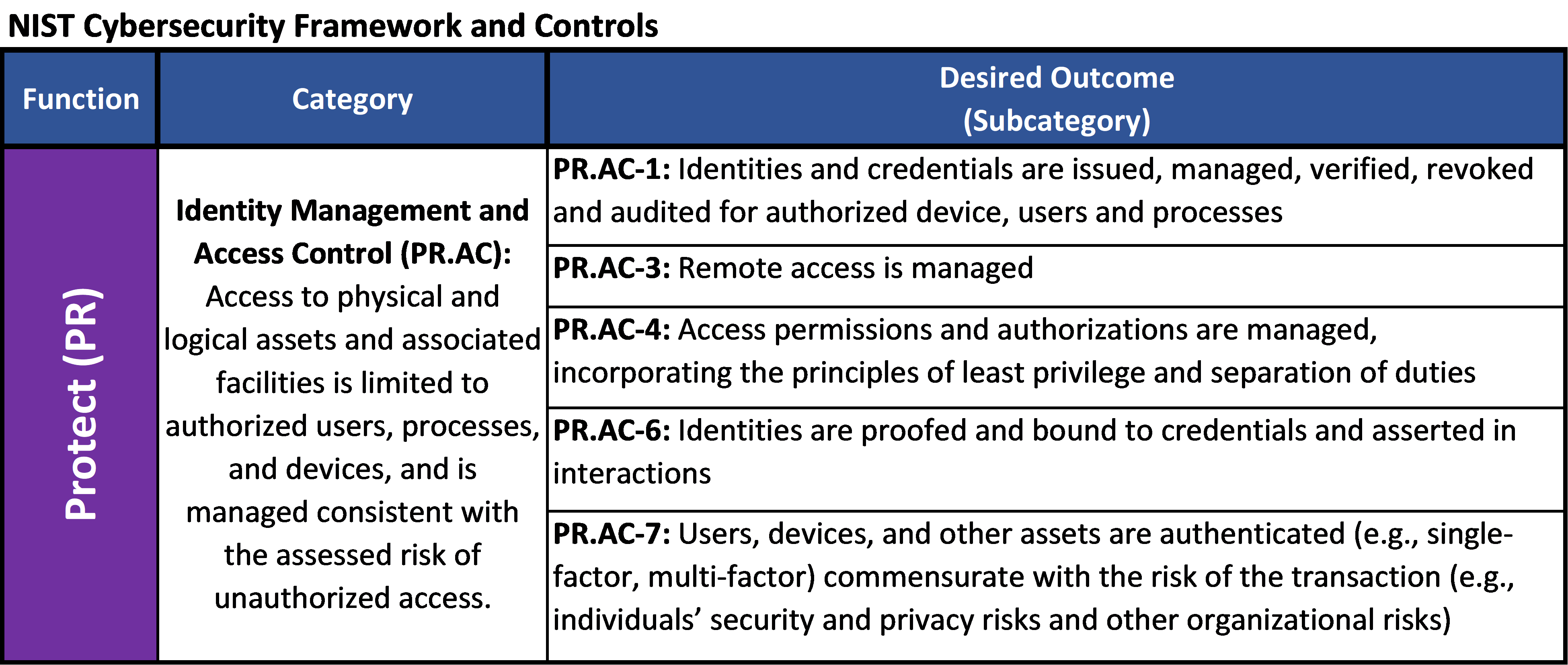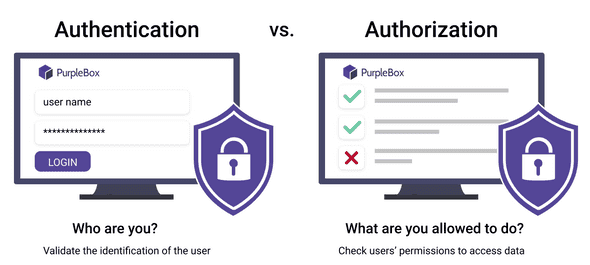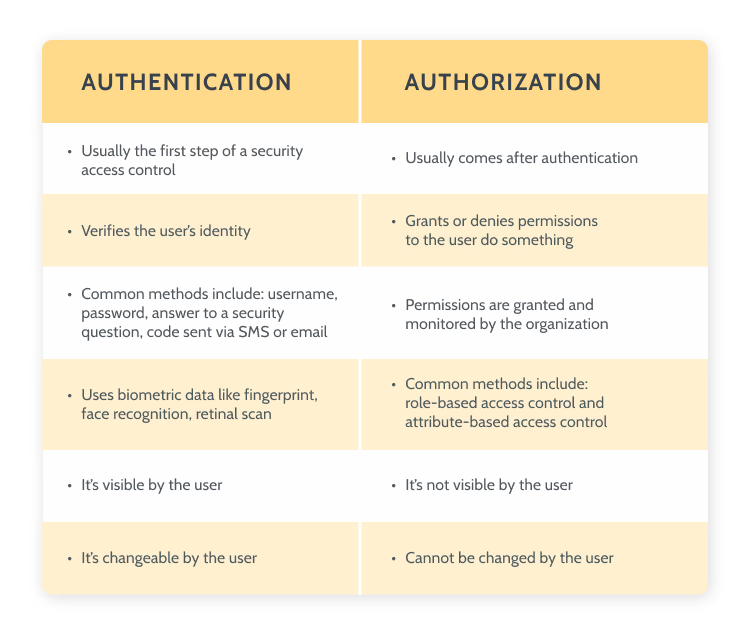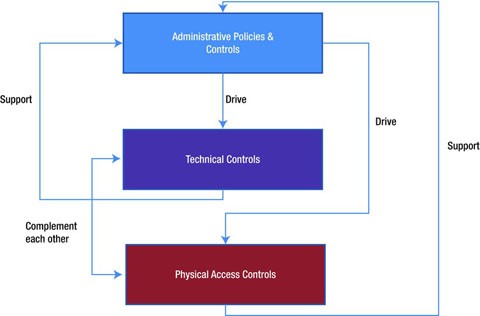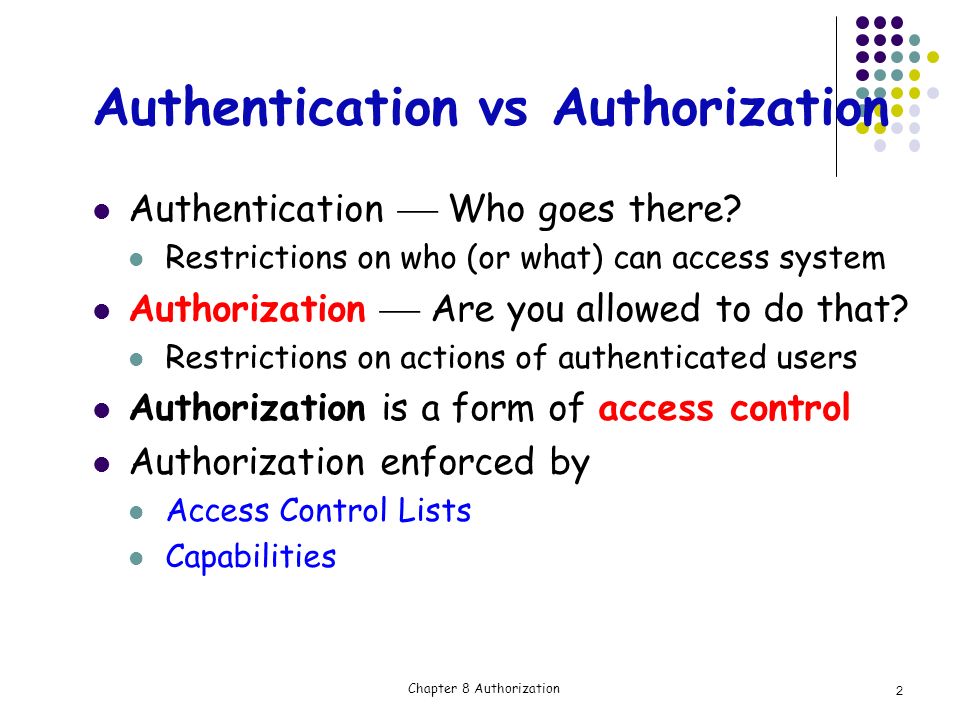
Chapter 8 Authorization Access control matrix Multilevel Security Multilateral security Covert channel Inference control CAPTCHA Firewalls IDS. - ppt download

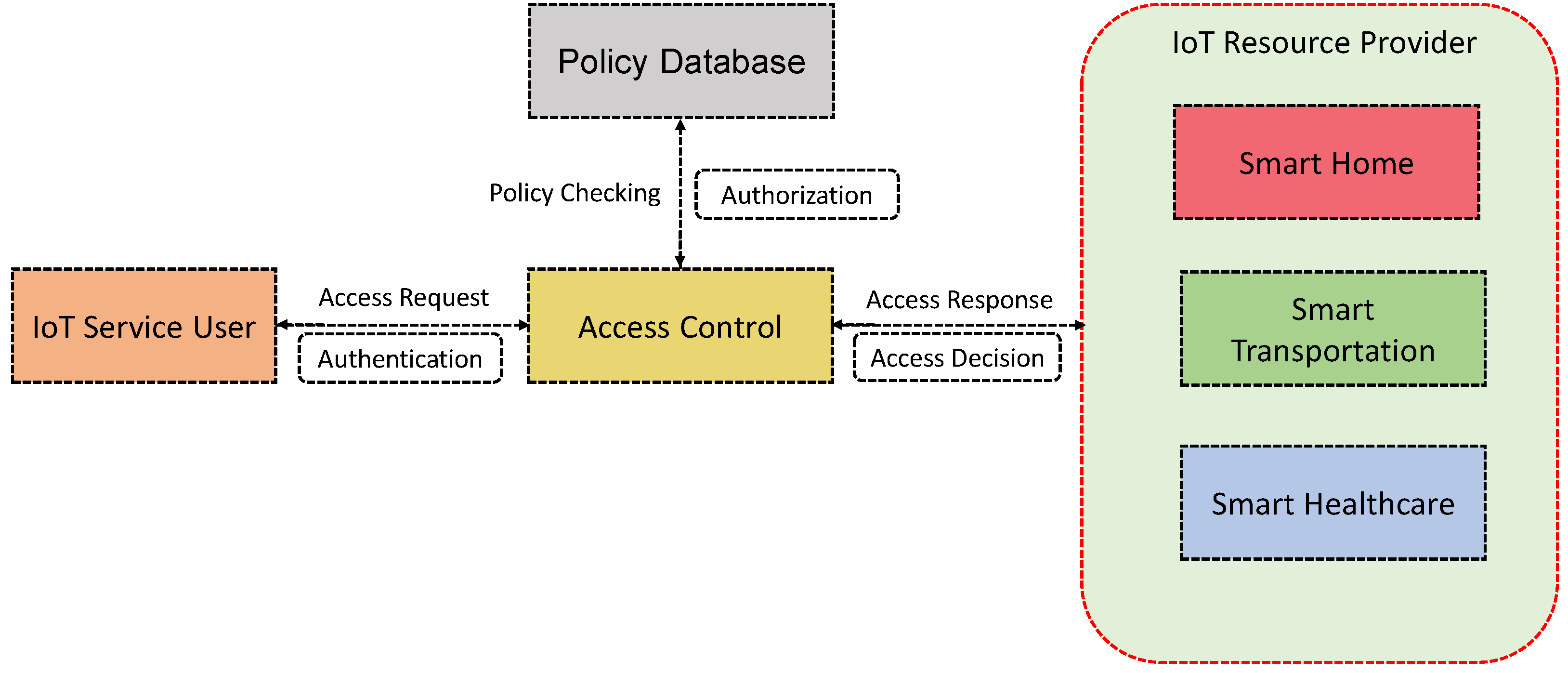
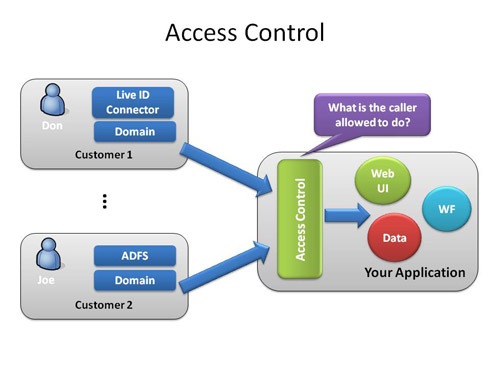
Identification, authentication and authorization in the proposed LBAC. | Download Scientific Diagram