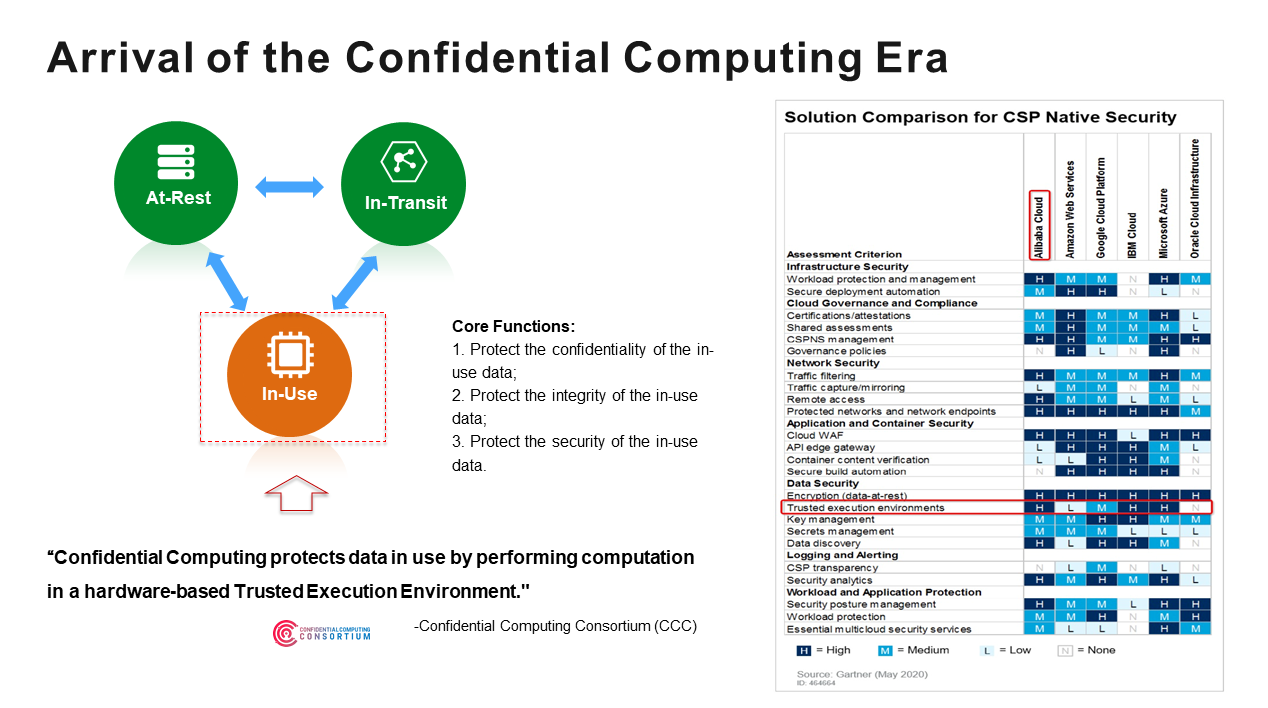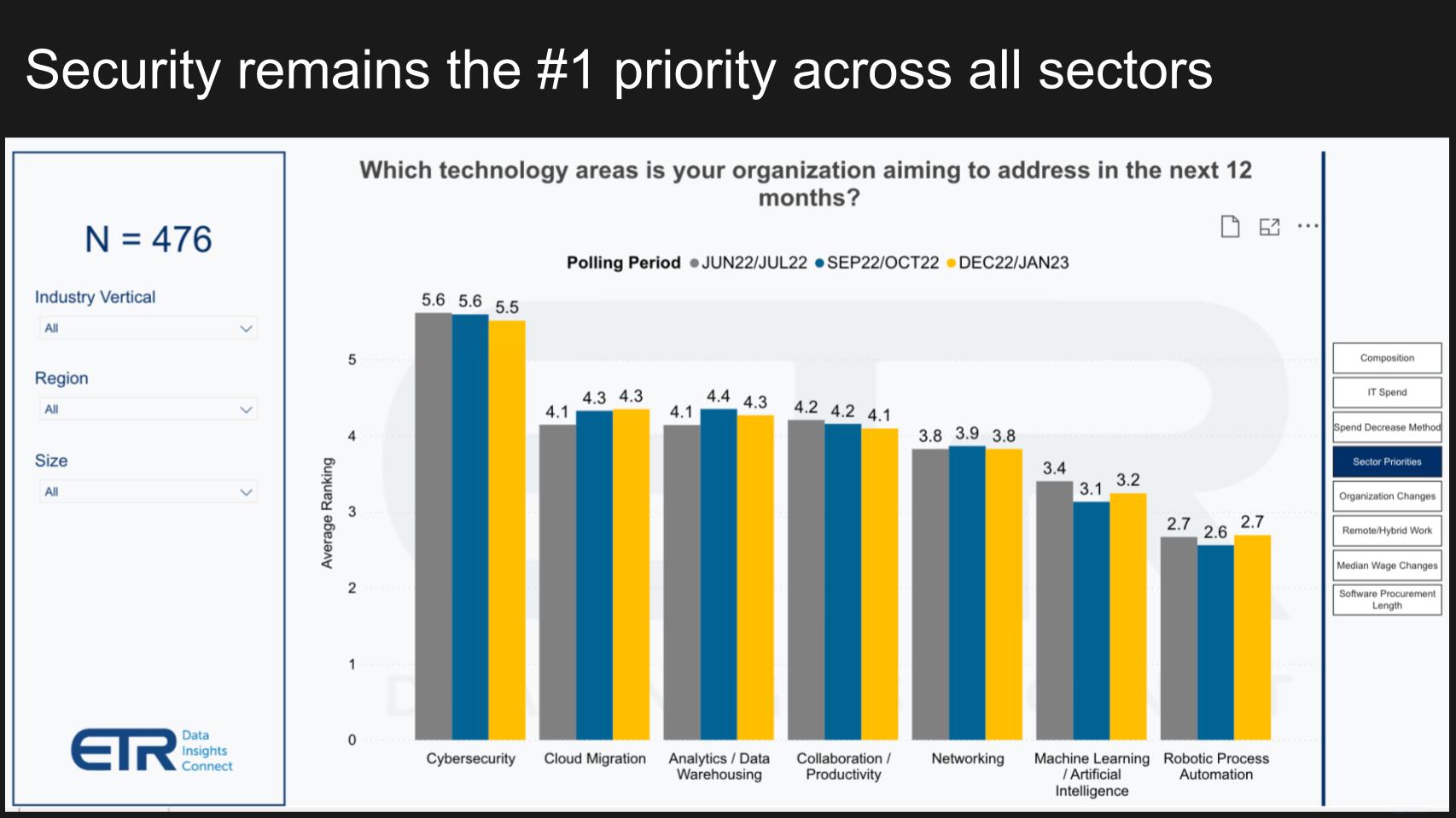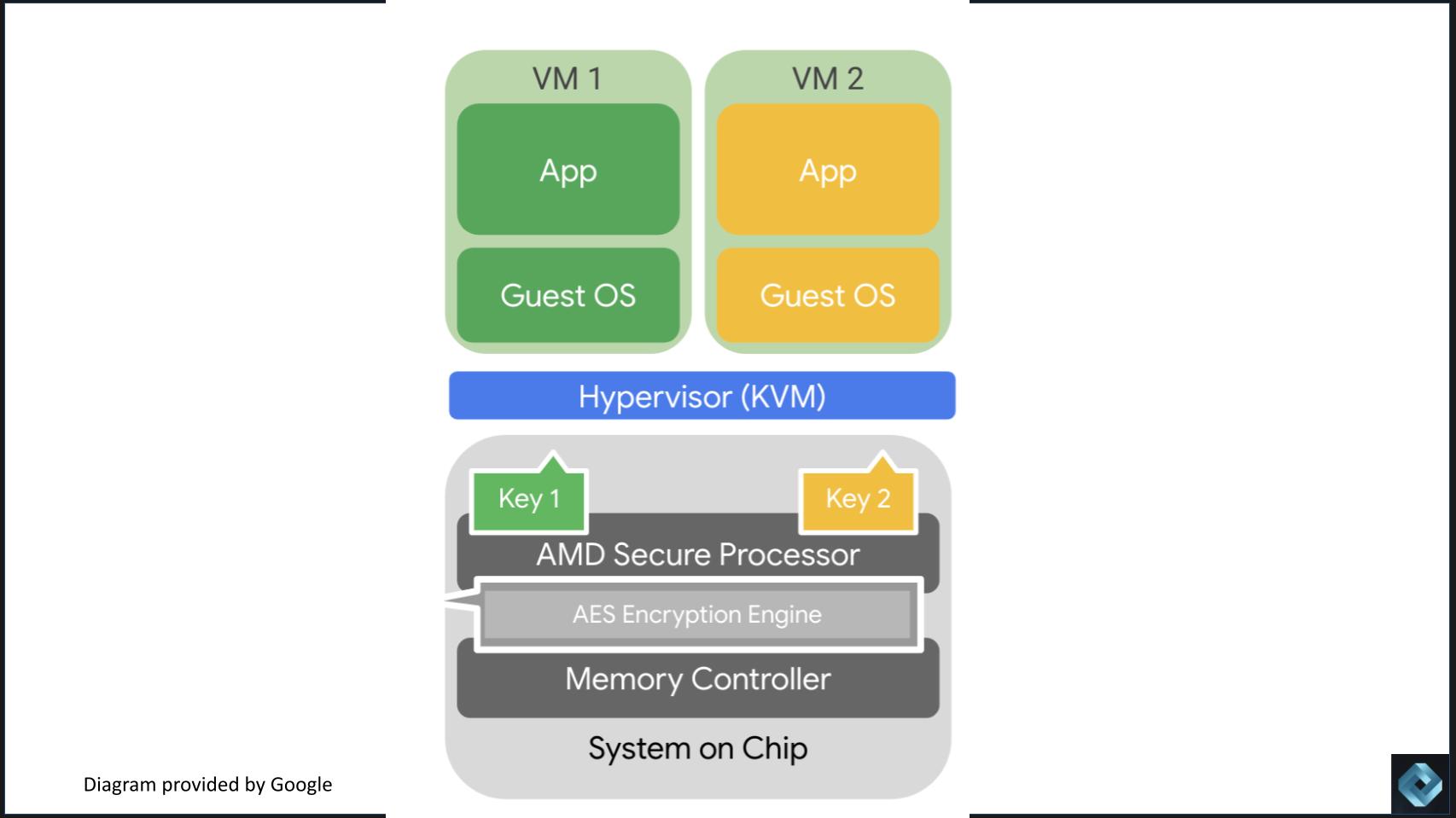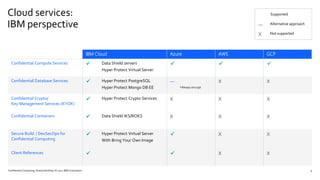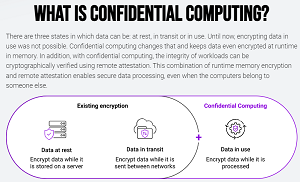
Confidential Computing' Specialist Open Sources Runtime-Encrypted Kubernetes -- Virtualization Review

18. Sovereignty Part 2/4 - Encryption to power data sovereignty on Google Cloud (Demo GCP EKM + KAJ and Confidential computing) | nikhilpurwant.com
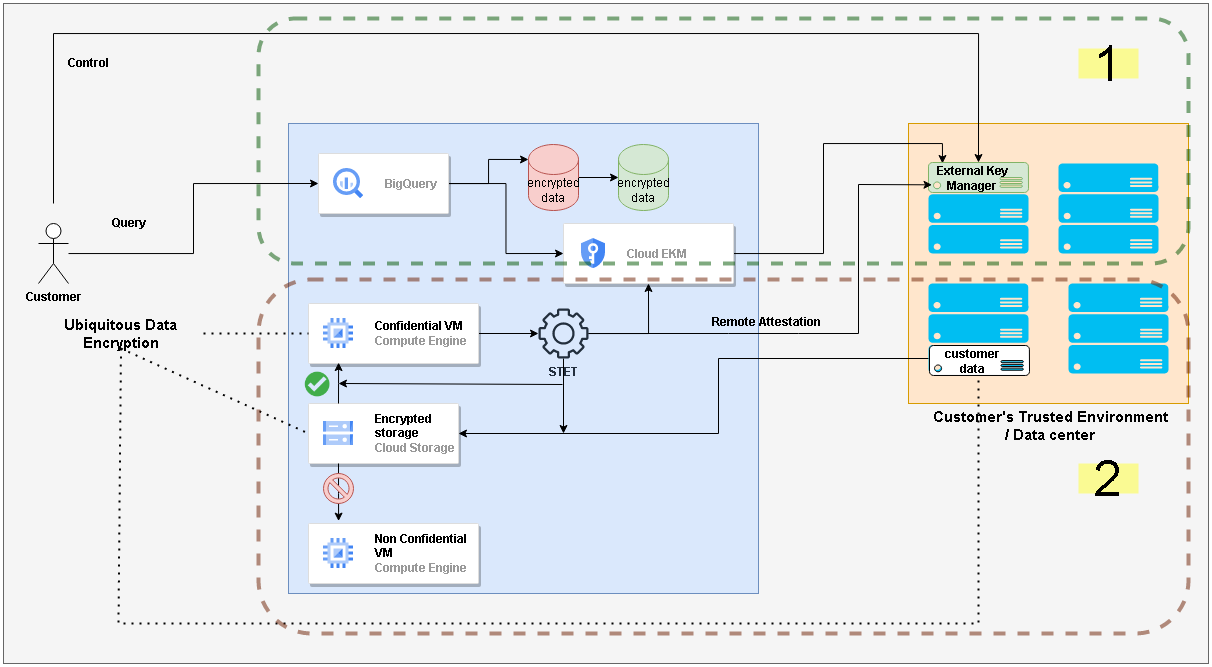
20. Sovereignty Part 4/4 - Setting up sovereignty demo on GCP - Google cloud EKM + Confidential Computing + Ubiquitous Data Encryption/UDE + Thales CKM | nikhilpurwant.com