Tongue based endpoint control of the assistive robotic arm by E2. a... | Download Scientific Diagram

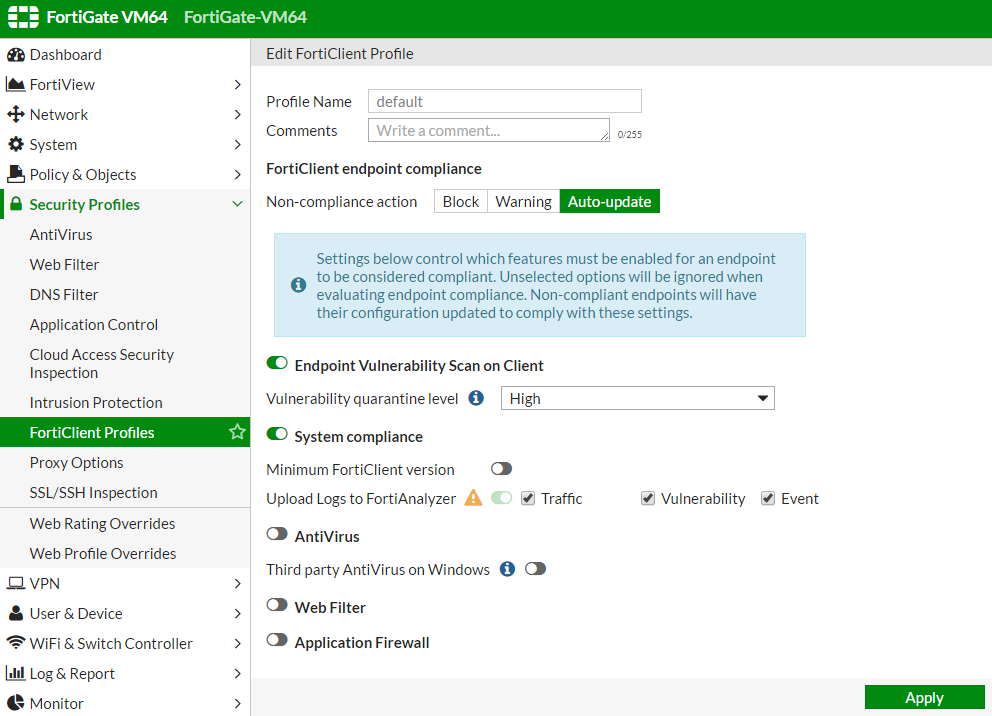
Fortinet FortiClient SSO License for FortiAuthenticator FortiAuthenticator FortiClient SSO Mobility Agent License for 10,000 FortiClient connections does not includee FortiClient Endpoint Control License for FortiGate FCC-FAC10K-LIC

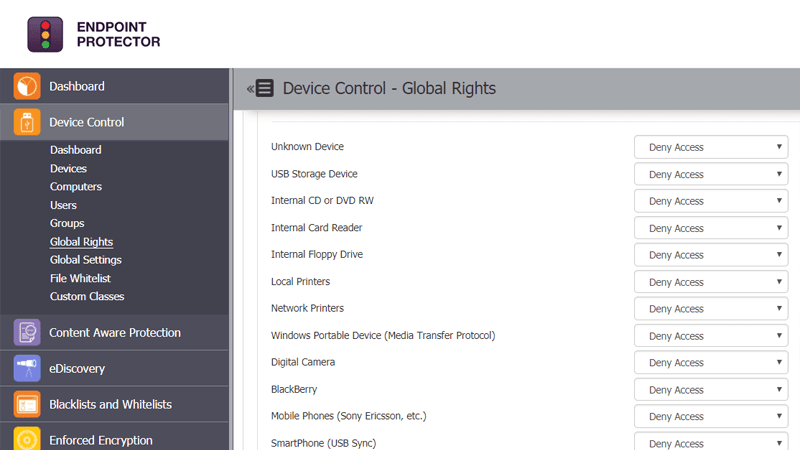
![KB7260] Add and modify Device control rules using ESET endpoint products (9.x–10.x) KB7260] Add and modify Device control rules using ESET endpoint products (9.x–10.x)](https://support.eset.com/storage/IMAGES/en/1563_KB7260/KB7260Fig1-1c.png)