Digital inclusion RGB color icons set. Cloud computing. Machine learning. Encrypted data storage. Manage focus. Isolated vector illustrations. Simple filled line drawings collection. Editable stroke Stock-Vektorgrafik | Adobe Stock
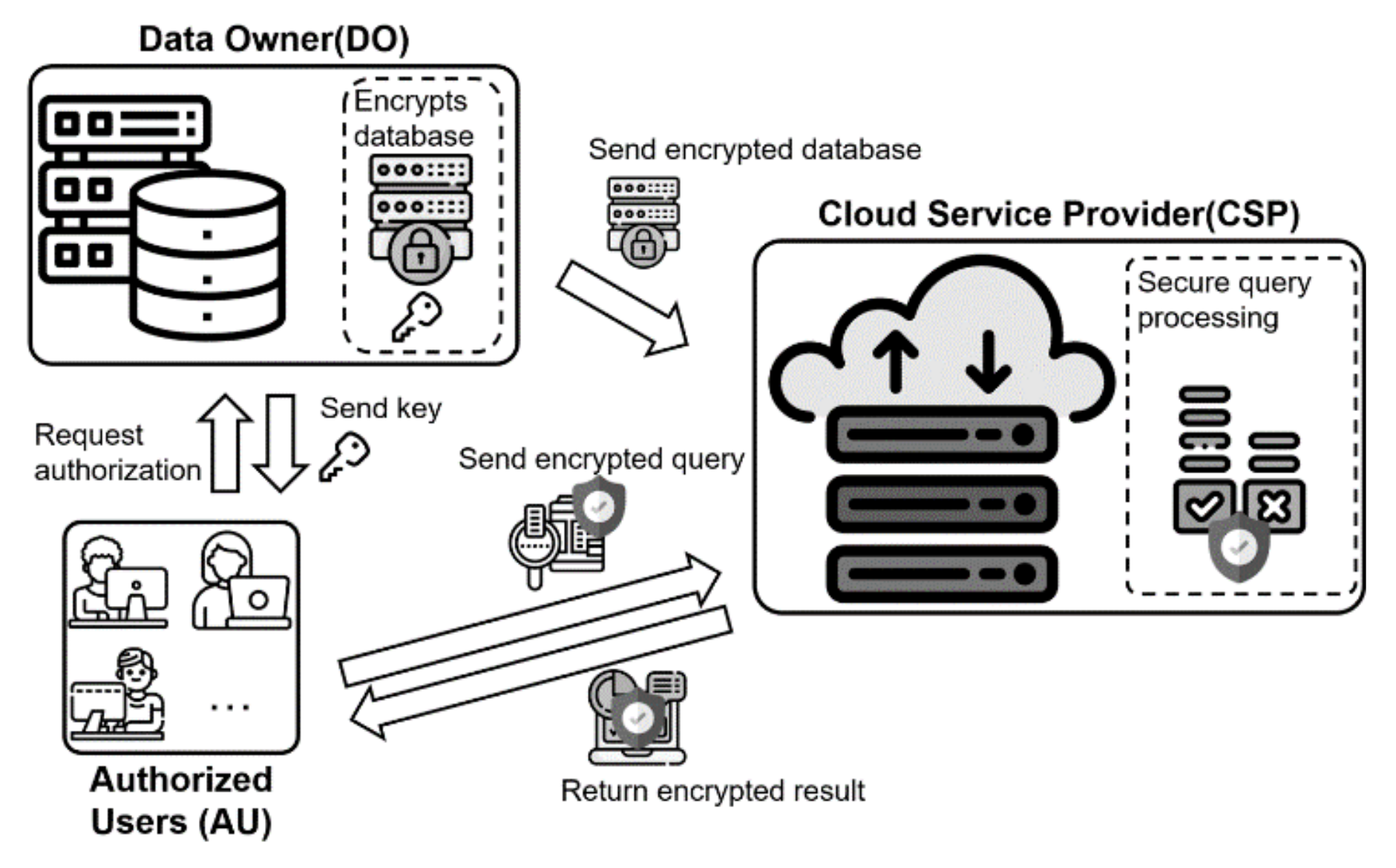
Electronics | Free Full-Text | Privacy-Preserving Top-k Query Processing Algorithms Using Efficient Secure Protocols over Encrypted Database in Cloud Computing Environment

Is homomorphic encryption ready to deliver confidential cloud computing to enterprises? | TechRepublic