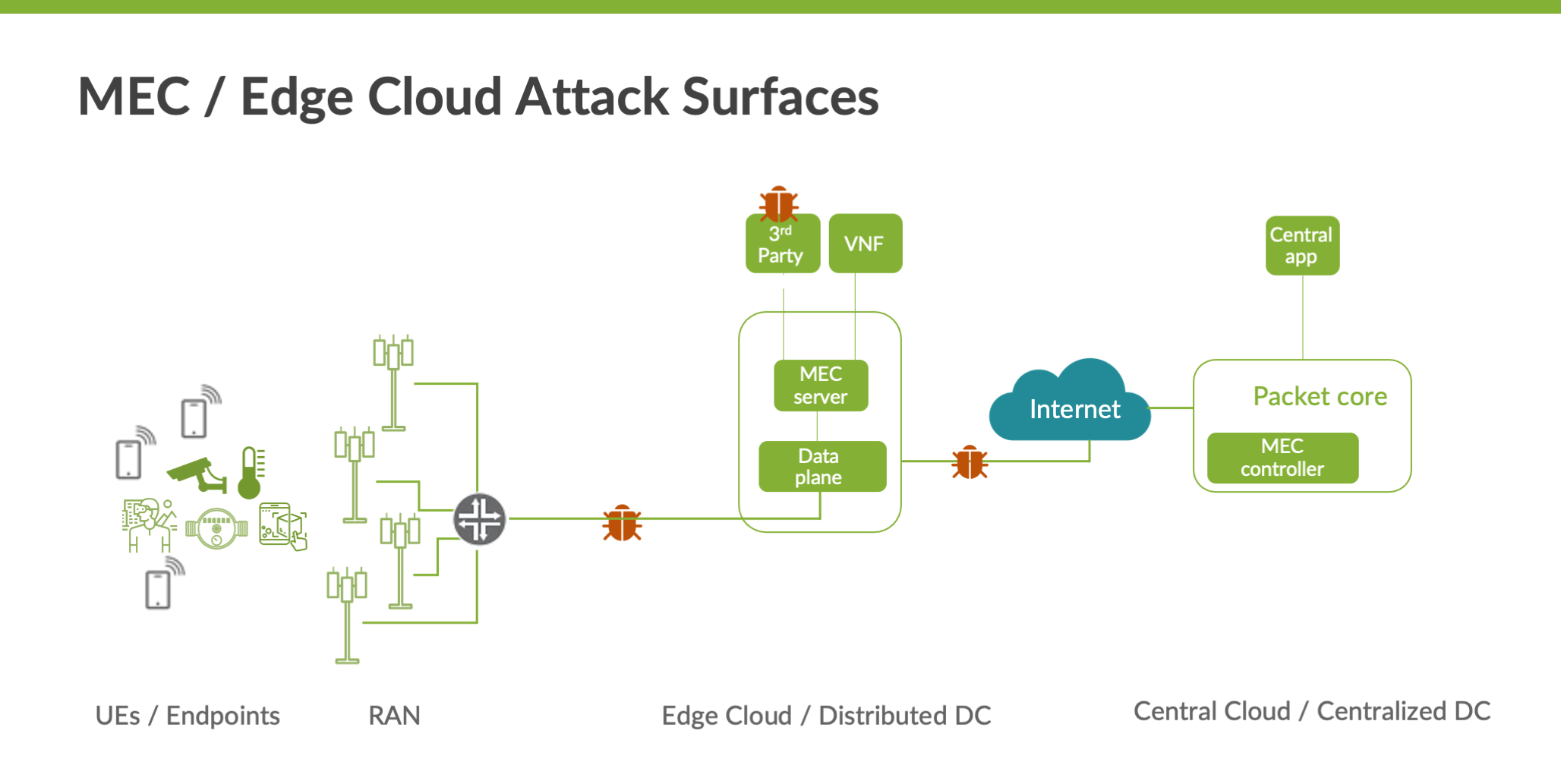
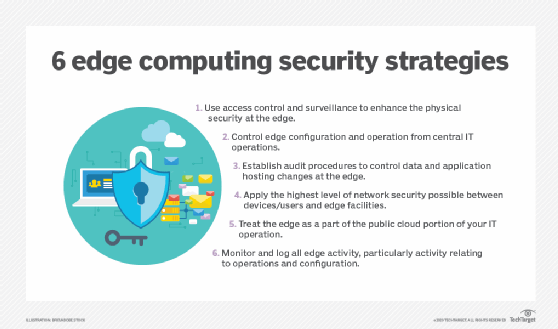
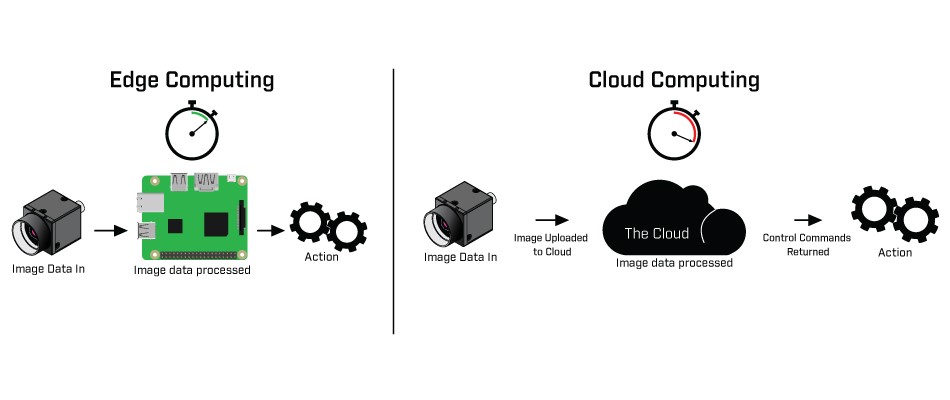
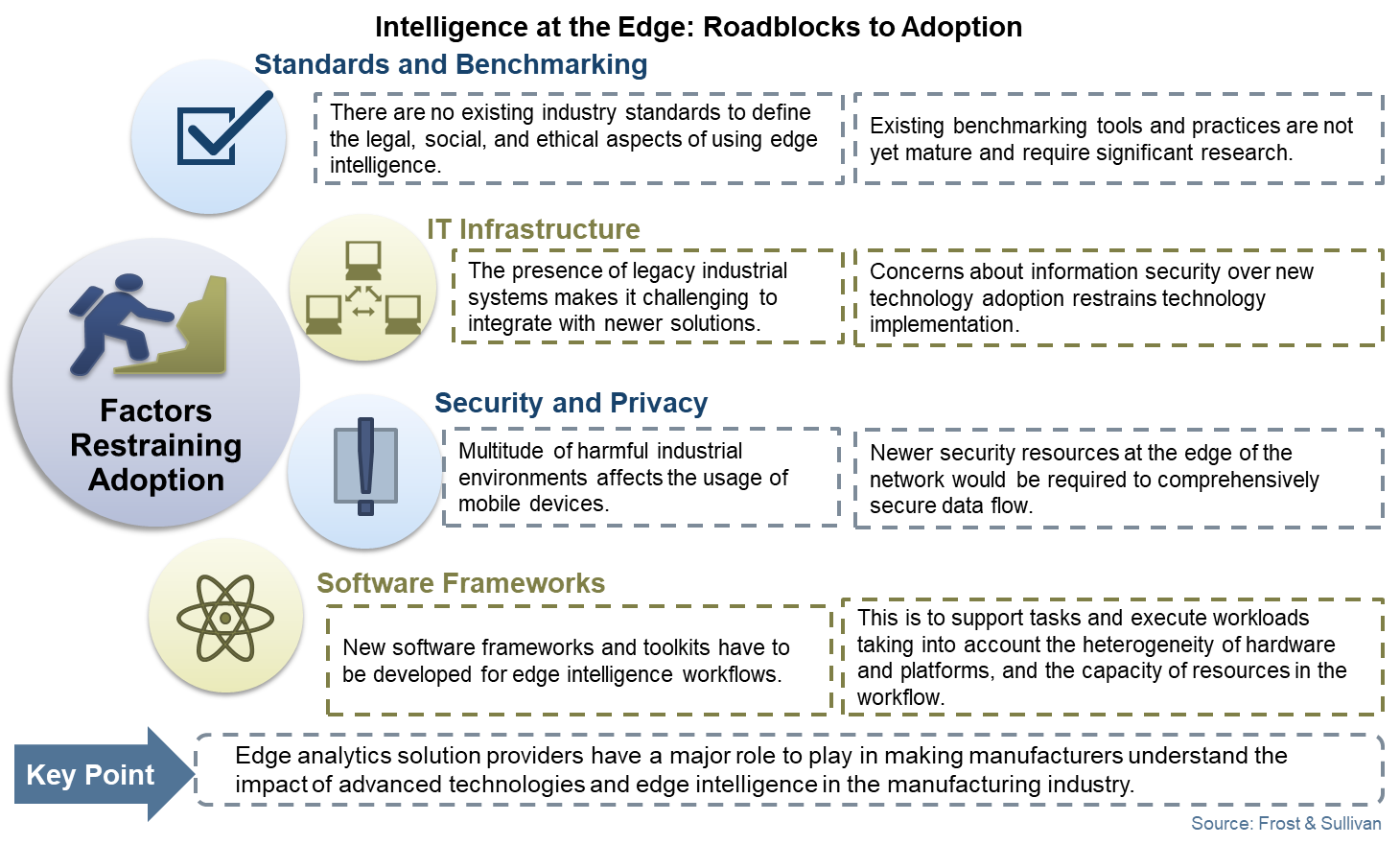
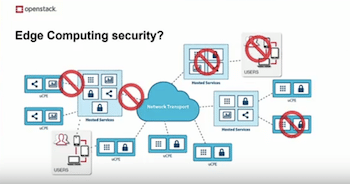
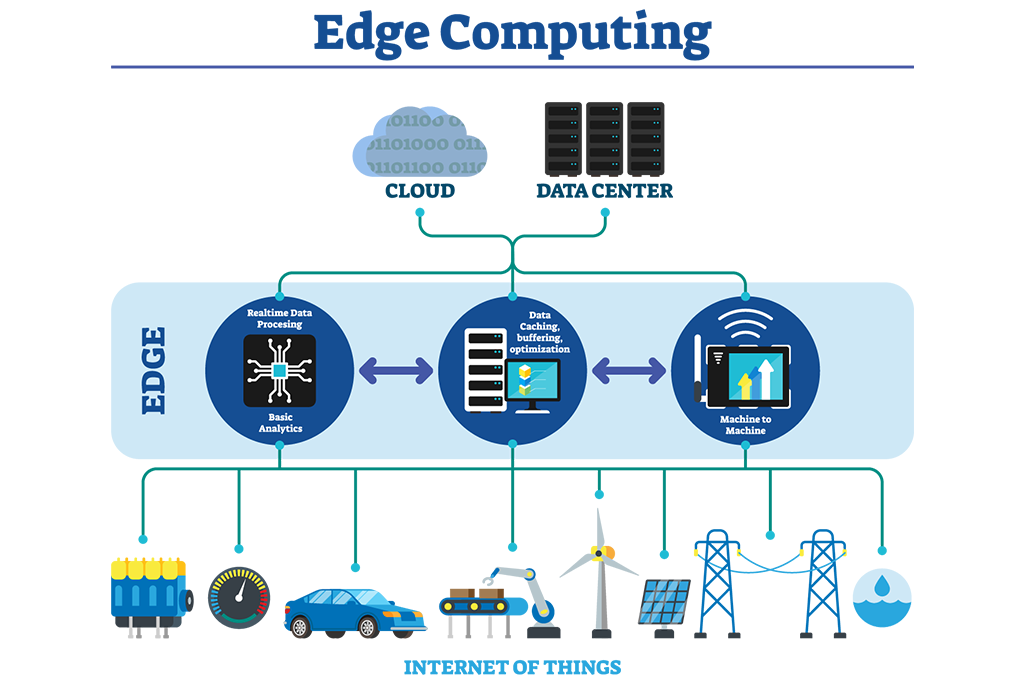
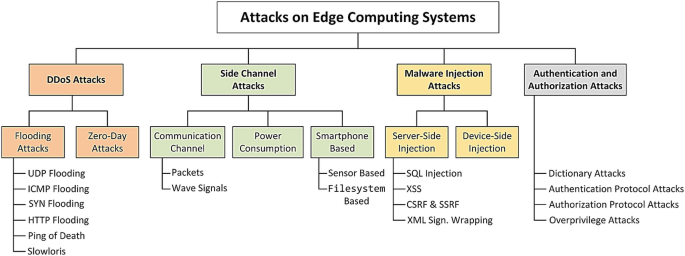
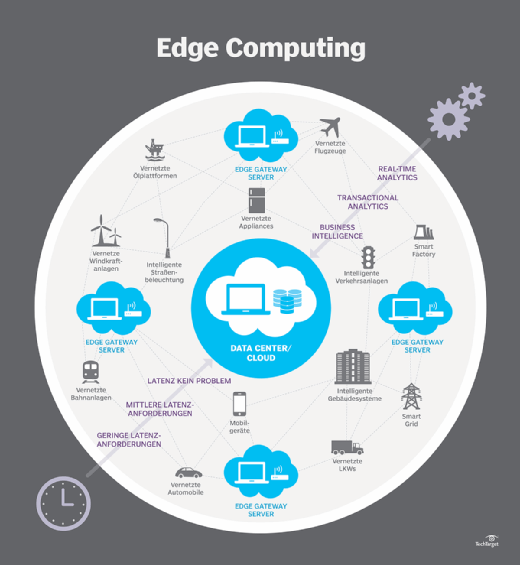
AT&T details edge computing and the security risks that you should be concerned about | TechRepublic
Edge Computing and IoT: Systems, Management and Security (kartoniertes Buch) | Buchhandlung Schöningh

Fog/Edge Computing For Security, Privacy, and Applications (kartoniertes Buch) | Guten Morgen Buchladen GmbH