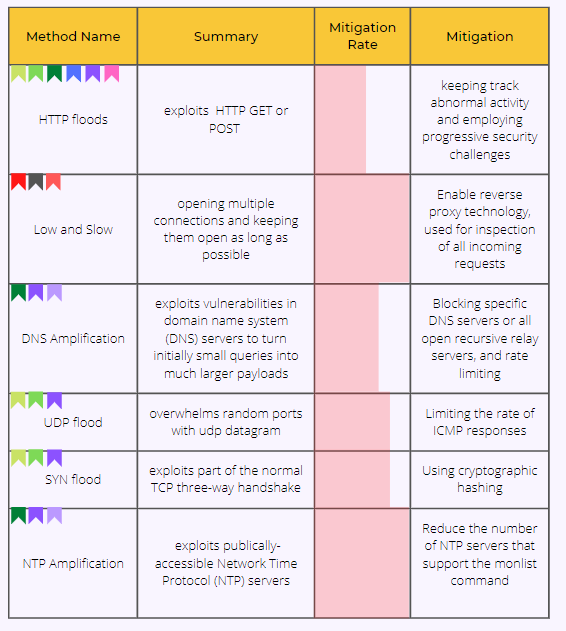
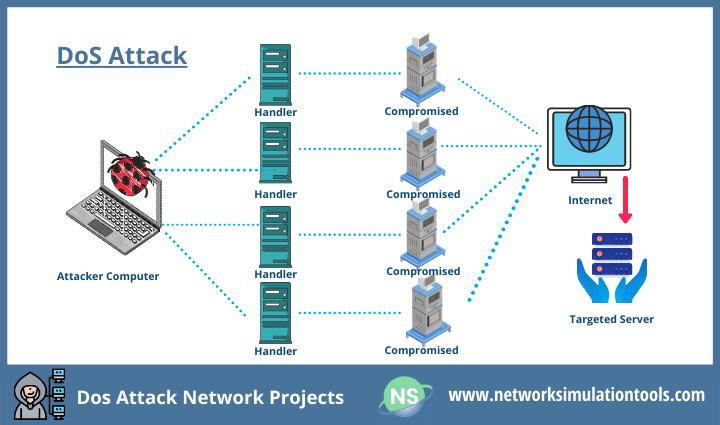
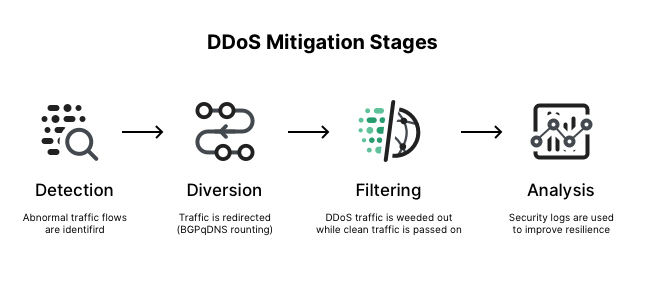
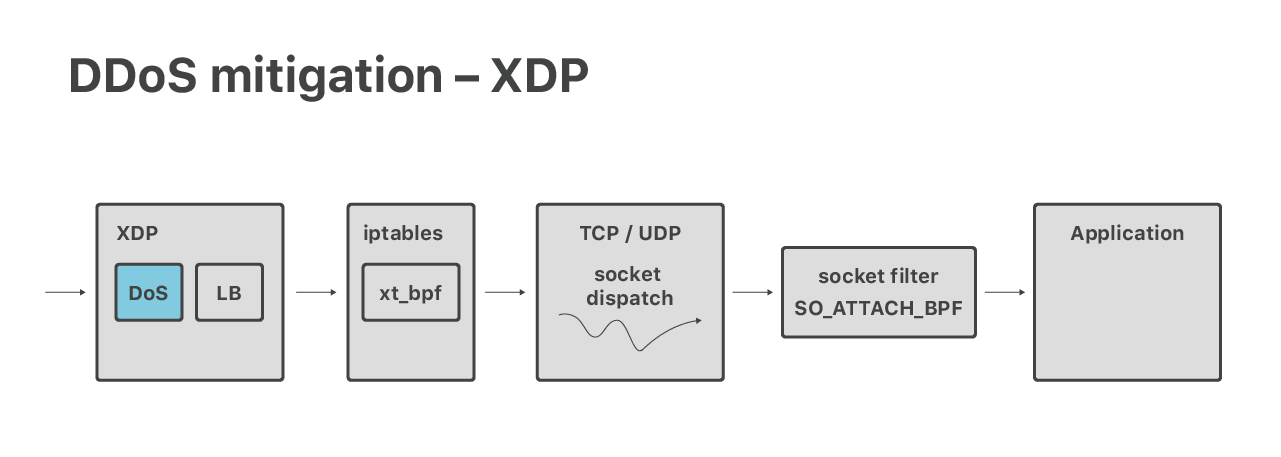
A survey on DoS/DDoS mitigation techniques in SDNs: Classification, comparison, solutions, testing tools and datasets - ScienceDirect

An Investigation into the Detection and Mitigation of Denial of Service DoS Attacks Buch versandkostenfrei bei Weltbild.de bestellen
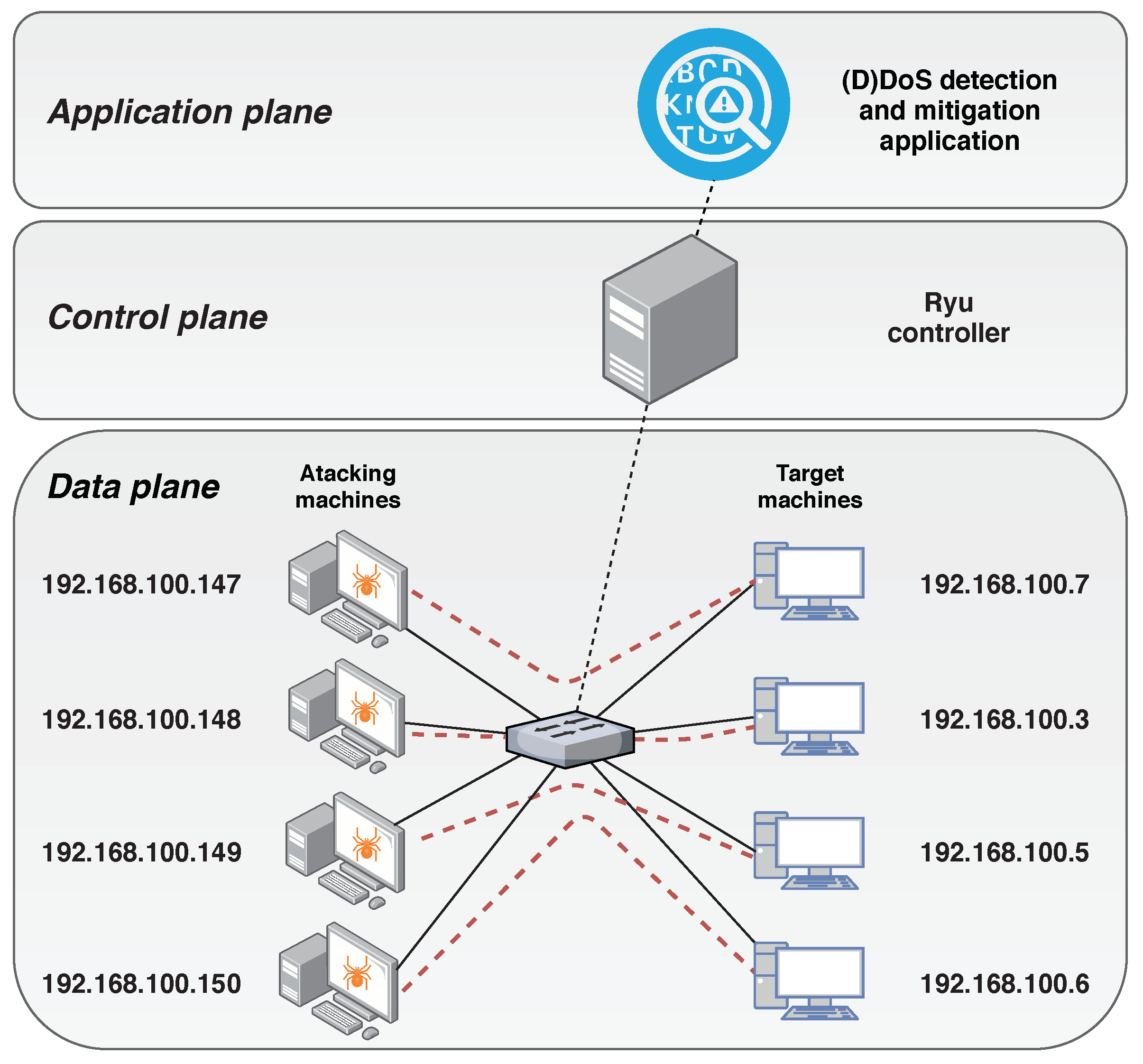
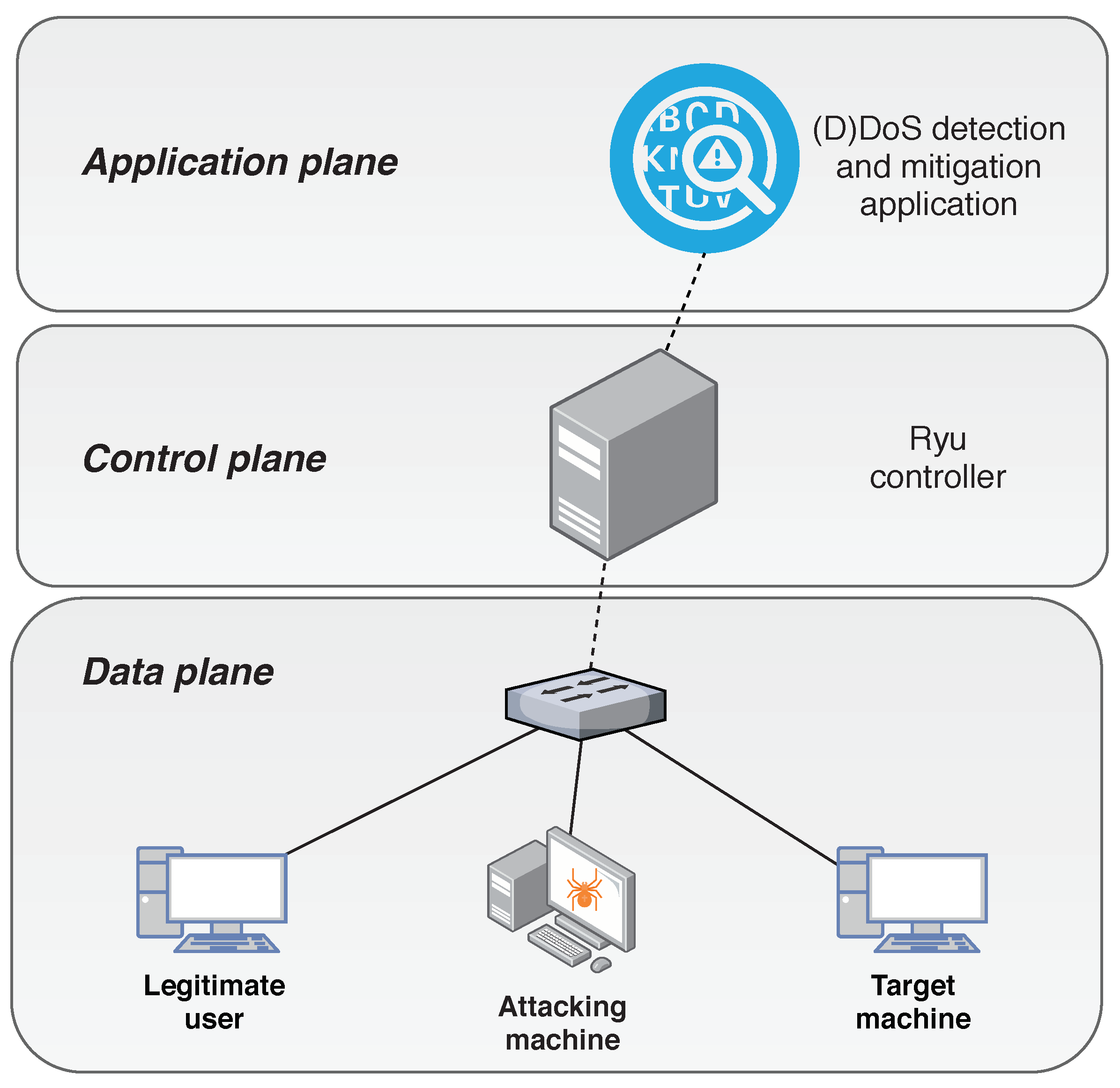
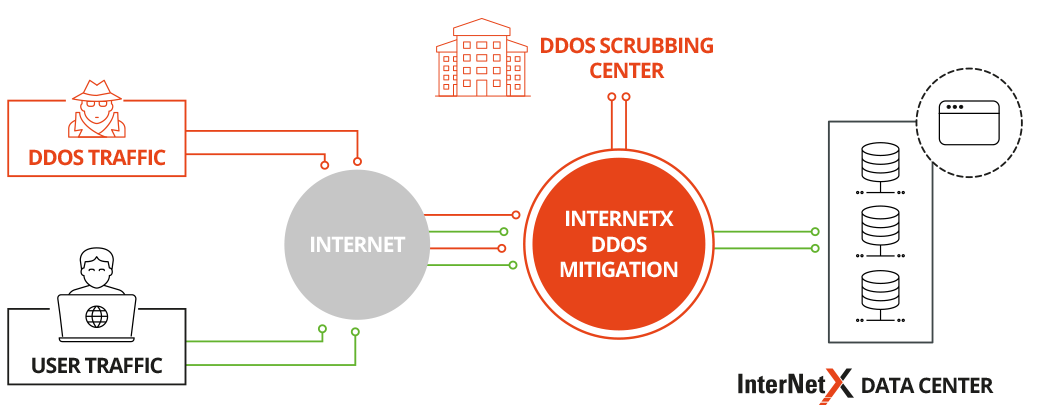
Sensors | Free Full-Text | Detection and Mitigation of DoS and DDoS Attacks in IoT-Based Stateful SDN: An Experimental Approach