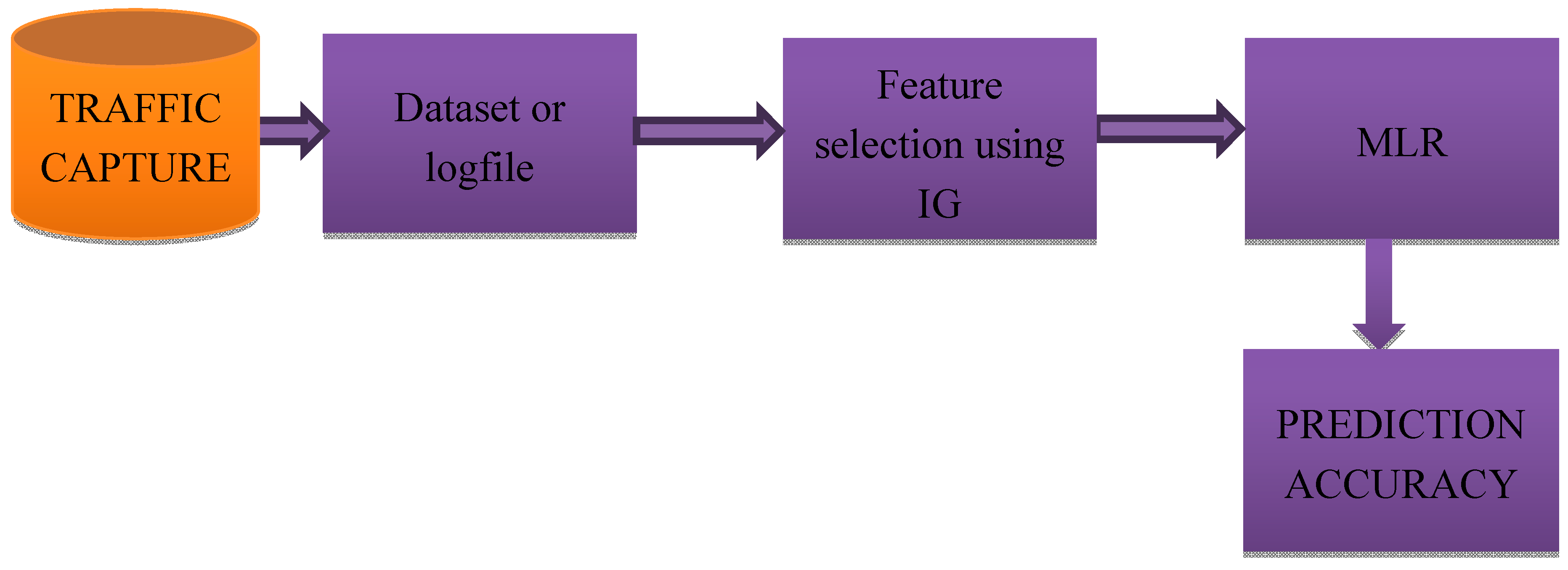
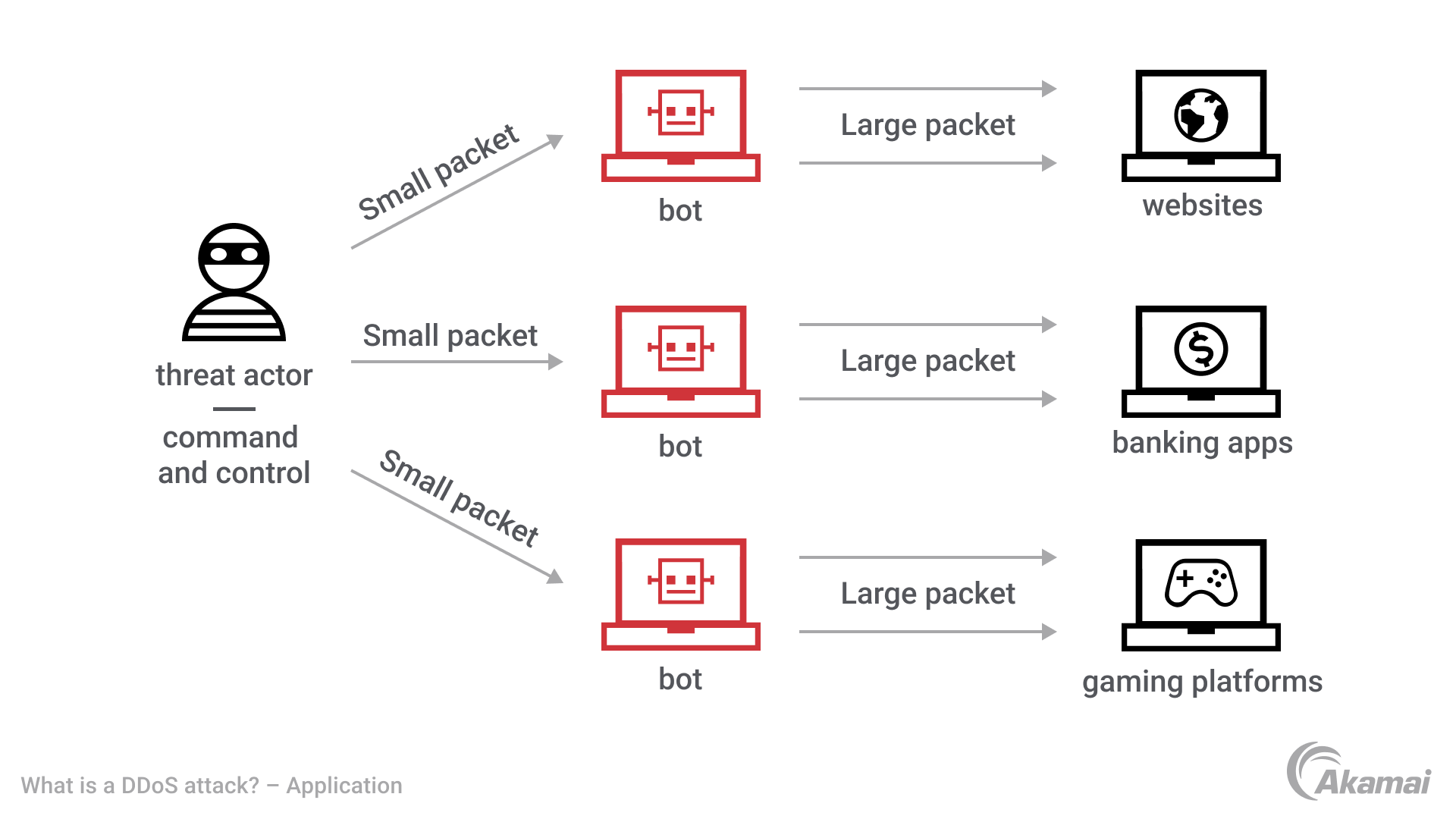
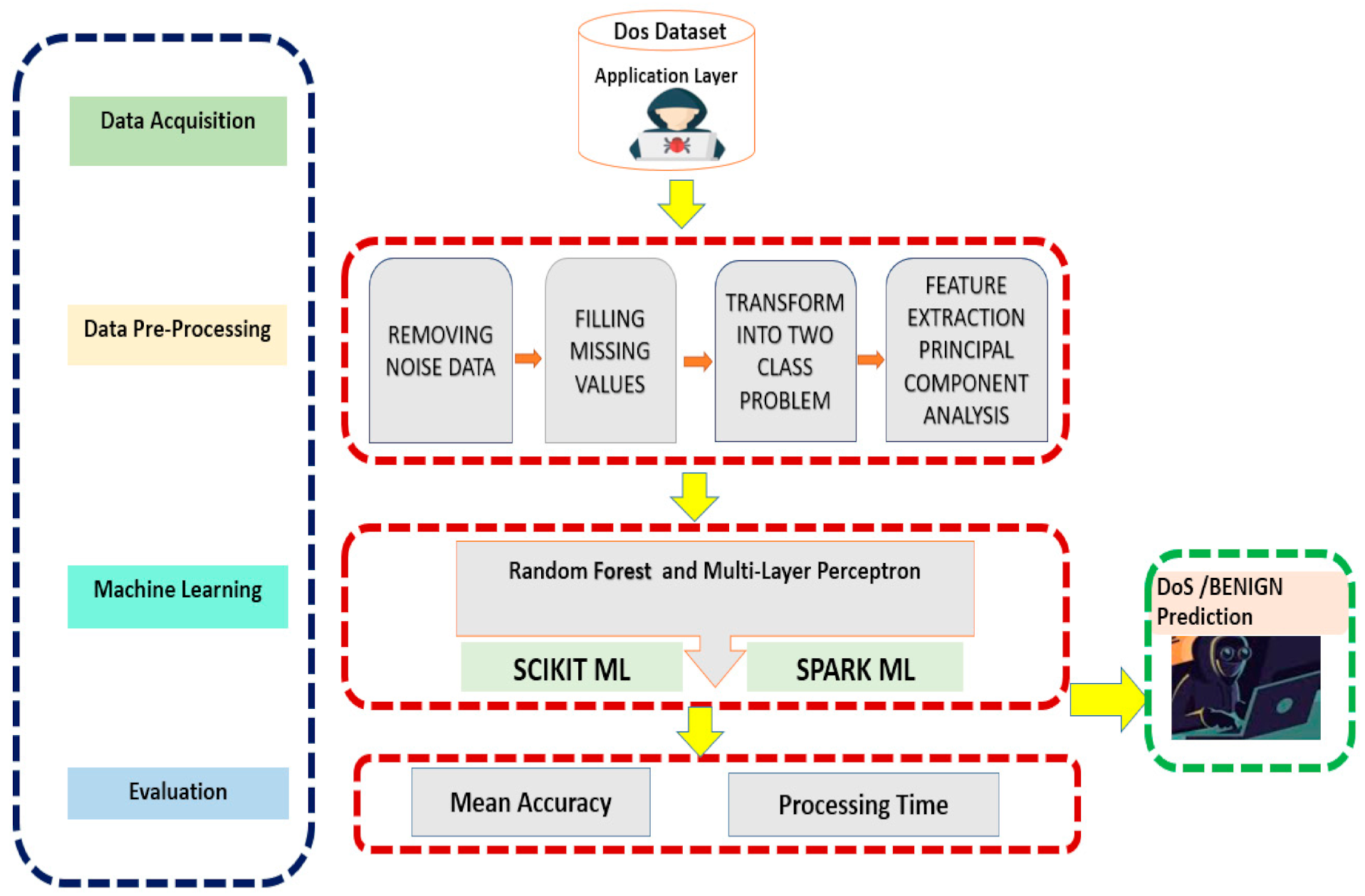
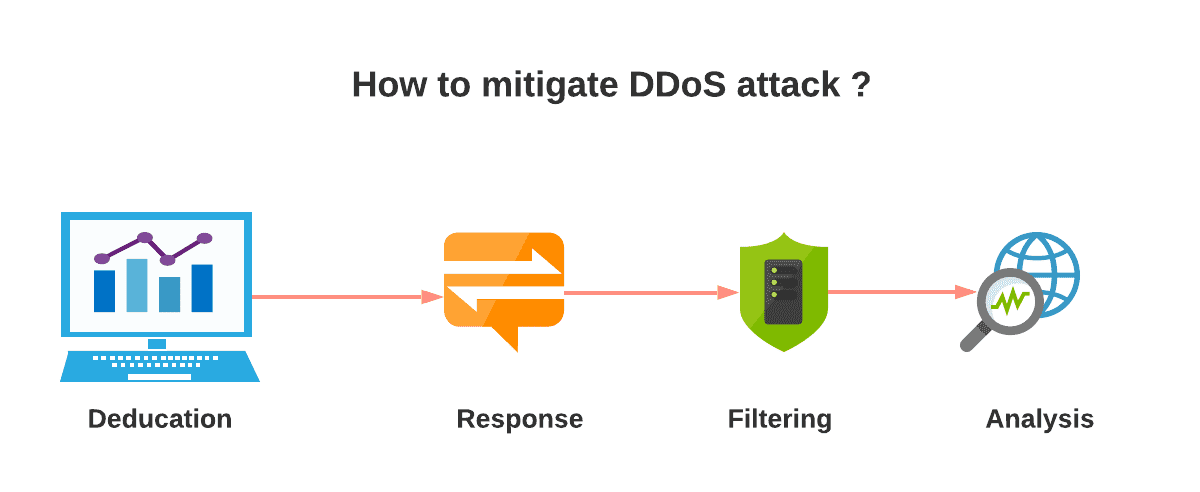
A Machine Learning Based Detection and Mitigation of the DDOS Attack by Using SDN Controller Framework | SpringerLink
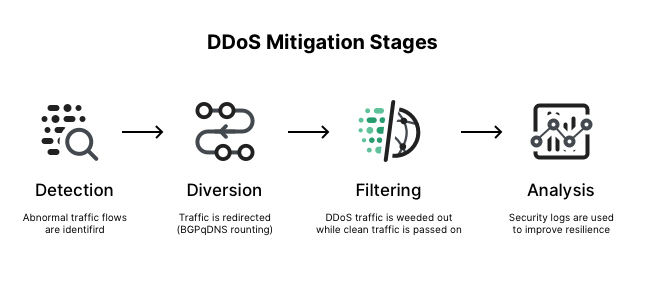
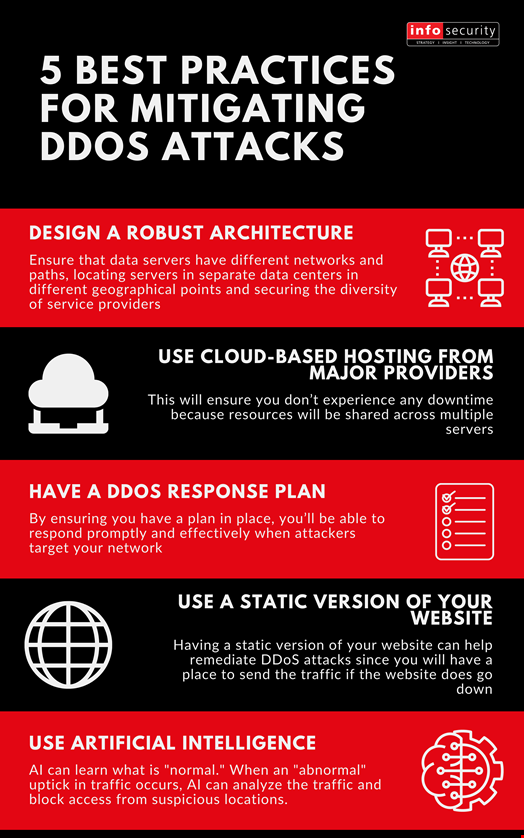
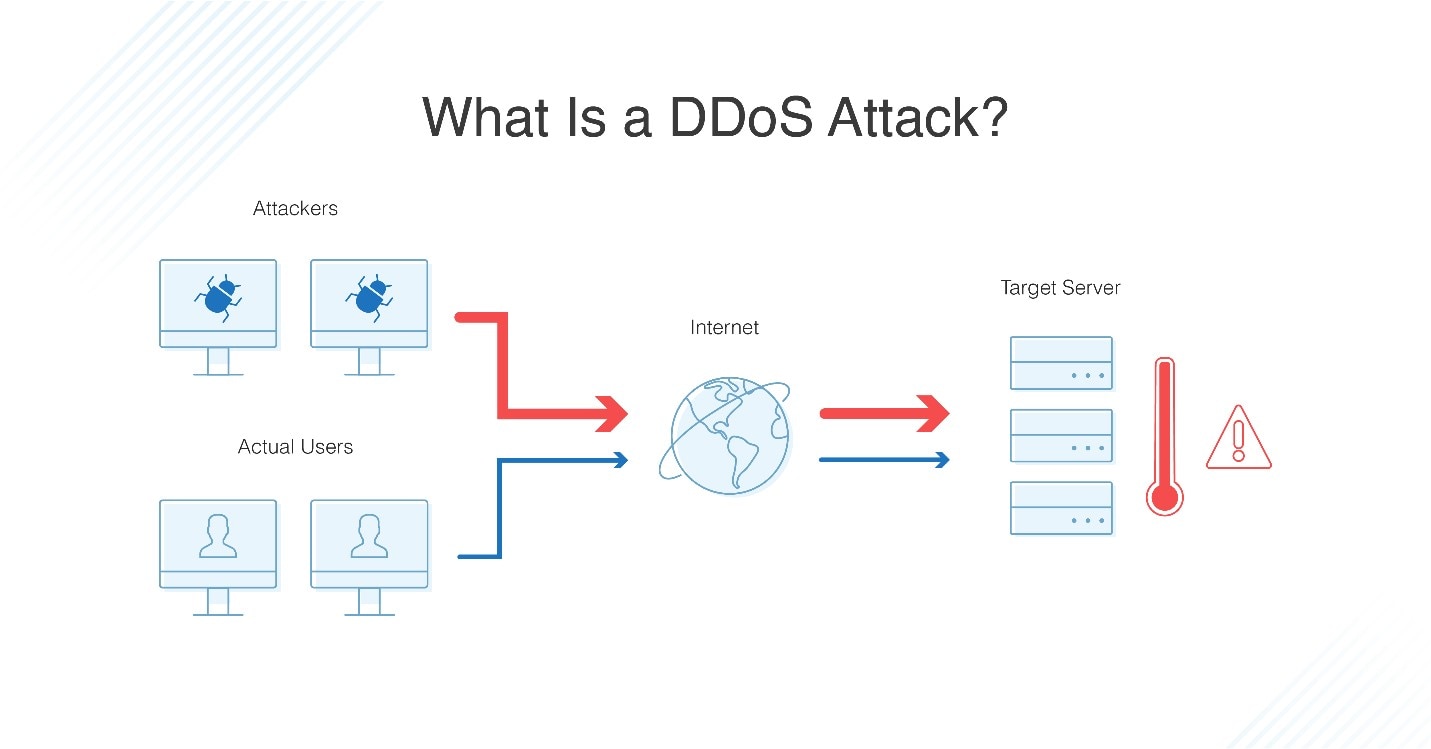
DDOS Attack Types and Mitigation Strategies | New Jersey Cybersecurity & Communications Integration Cell
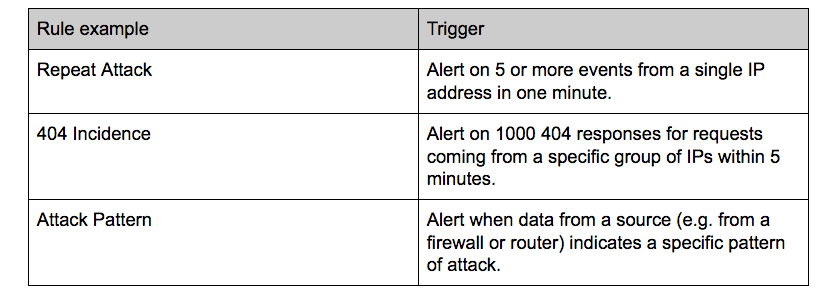
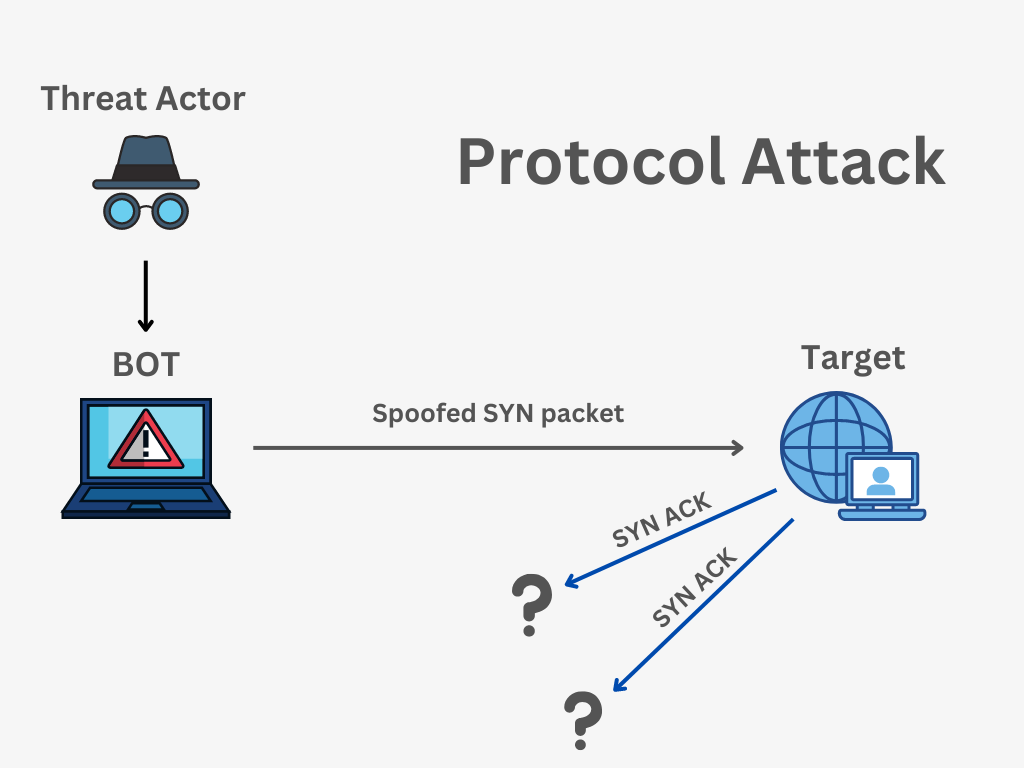
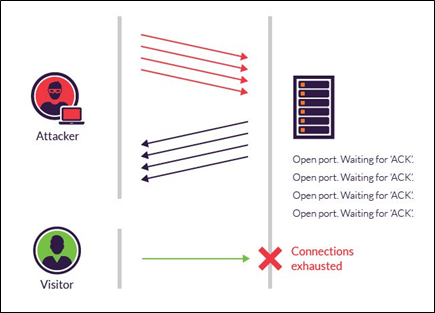
![PDF] Defense Against SYN Flood DoS Attacks Using Network-based Mitigation Techniques | Semantic Scholar PDF] Defense Against SYN Flood DoS Attacks Using Network-based Mitigation Techniques | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e773bf12d01cff5ff59ba77166a289c79ca74b3e/4-Figure3-1.png)
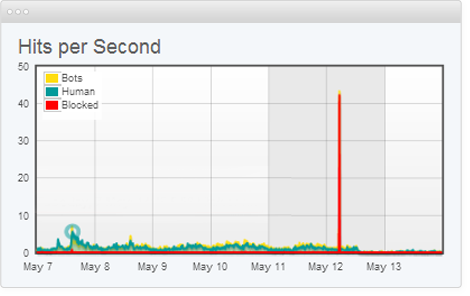
PDF] Defense Against SYN Flood DoS Attacks Using Network-based Mitigation Techniques | Semantic Scholar