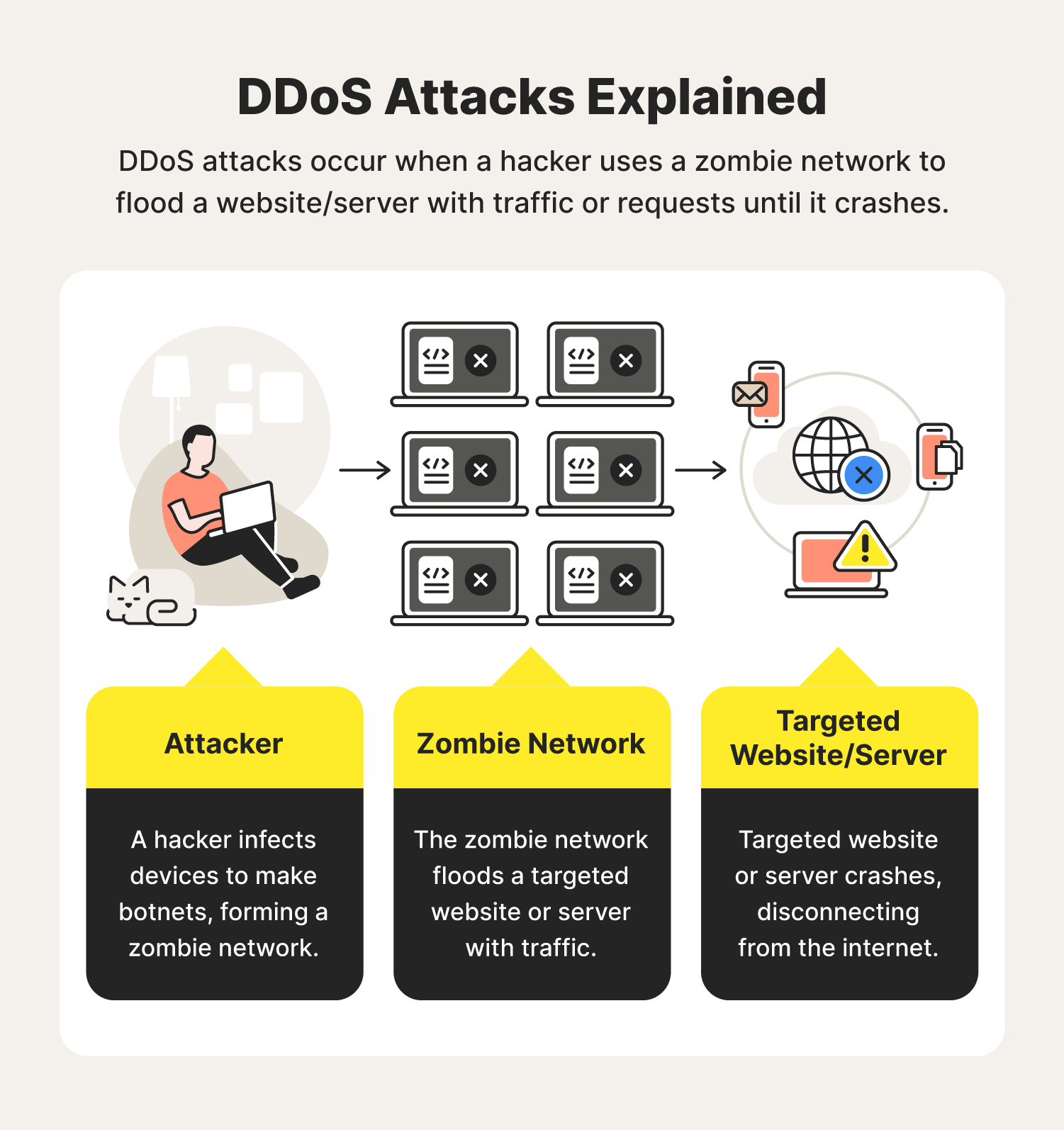
Denial of Service ATTACK | How Hackers Exploit Weakness | Types of DOS Attack | DOS Attack Examples - YouTube

Cybersecurity Guide For Beginners: Denial of Service (DoS) Vs. Distributed Denial of Service (DDoS) - Cyber Coastal
Cybercrime and its prevention linear icons set. Phishing and Dos attack. Cybersecurity methods. Customizable thin line contour symbols. Isolated vector outline illustrations. Editable stroke 6562975 Vector Art at Vecteezy

Oakford on Twitter: "For #CyberSecMonth we have put together a 'Dos and Don'ts of cyber security' guide. Follow these tips and tricks to ensure you are cyber safe. 👮♂️👩💻💻 #cybersecurity #guide #cybersafe