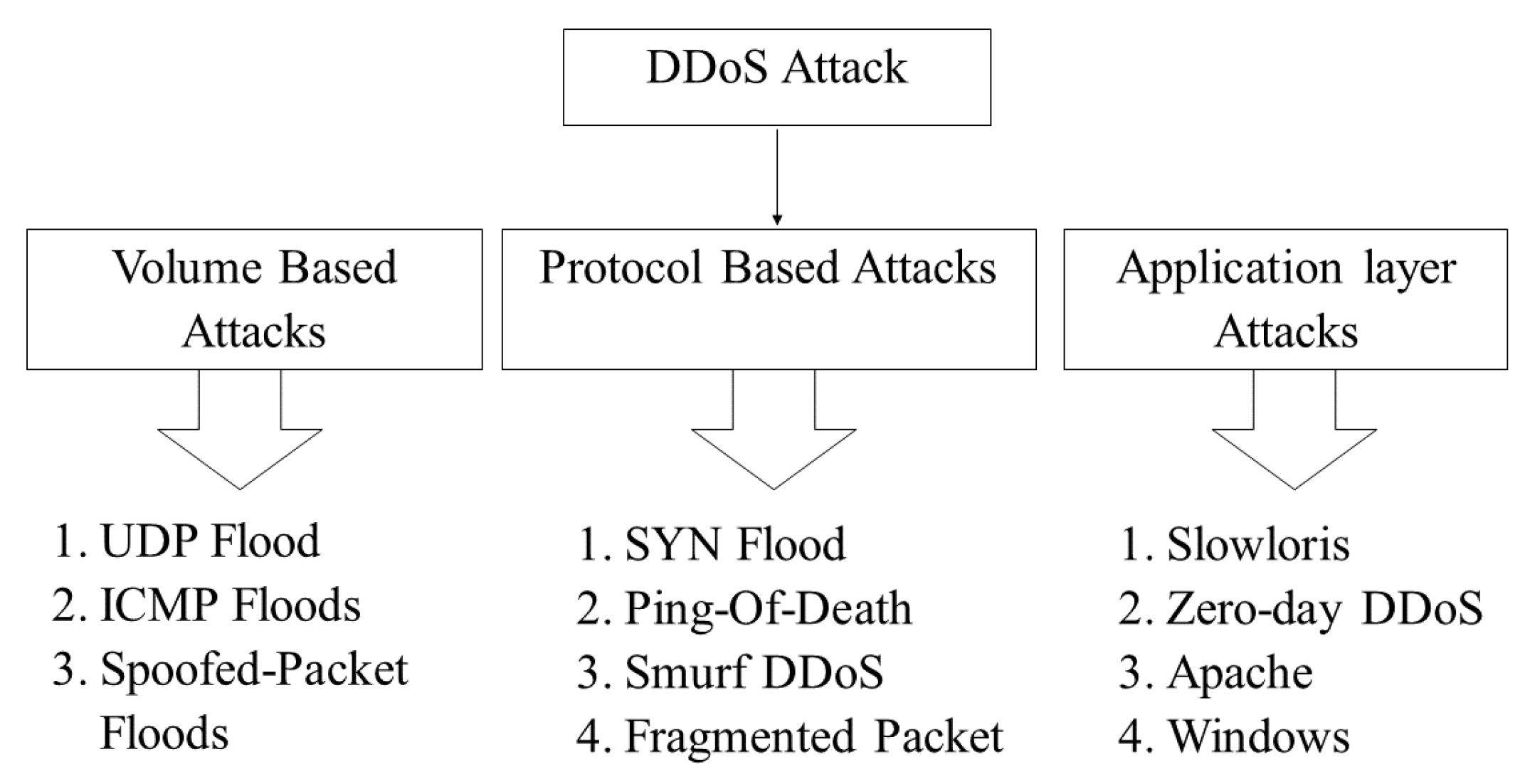
Electronics | Free Full-Text | A DDoS Attack Mitigation Scheme in ISP Networks Using Machine Learning Based on SDN
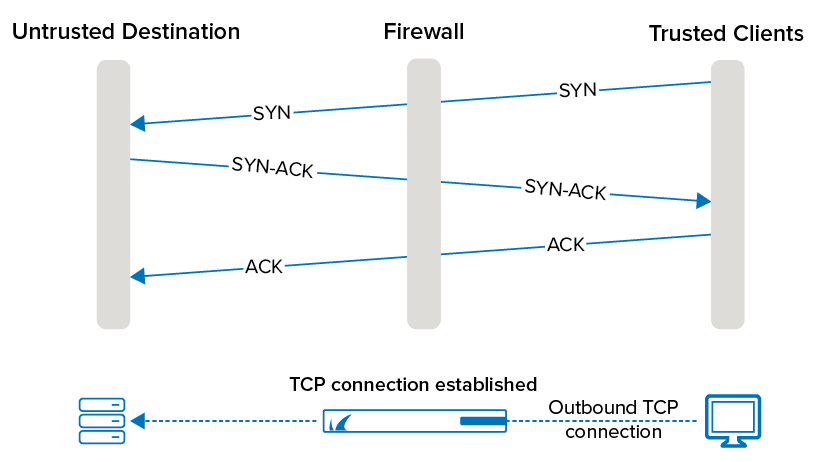
Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies | Barracuda Campus

Detecting SYN flooding attacks based on traffic prediction - Wang - 2012 - Security and Communication Networks - Wiley Online Library

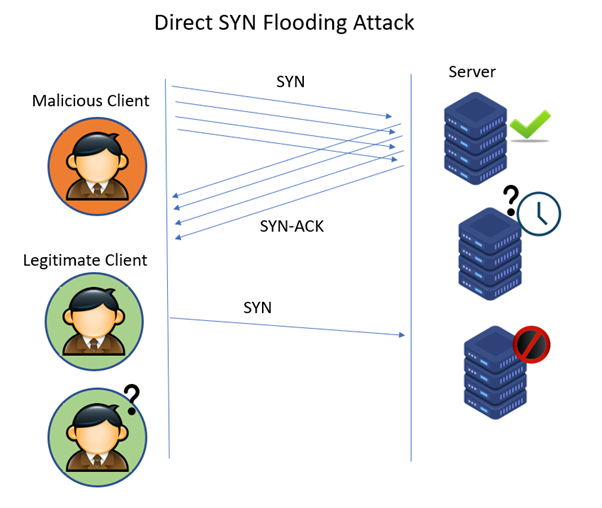
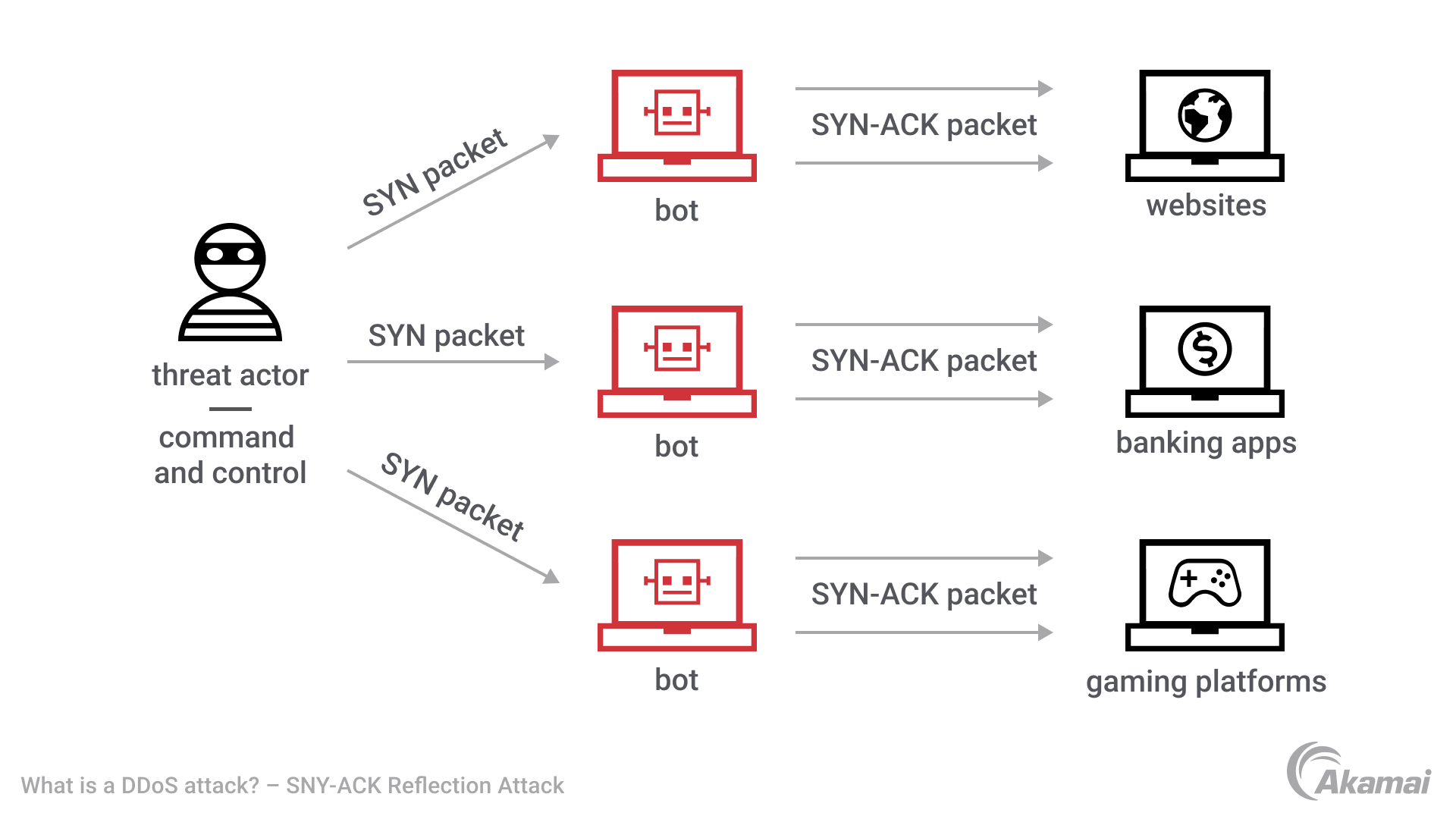
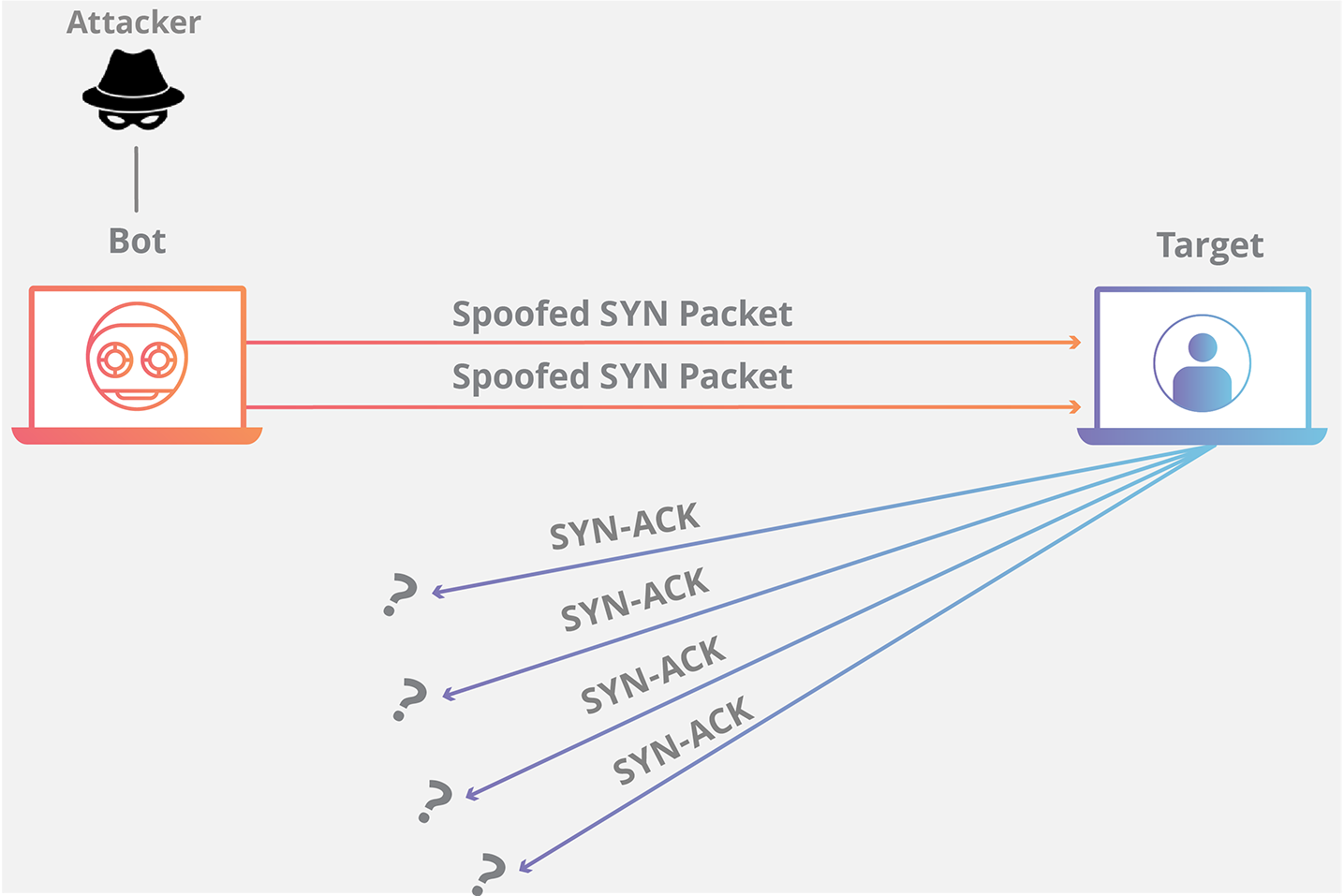

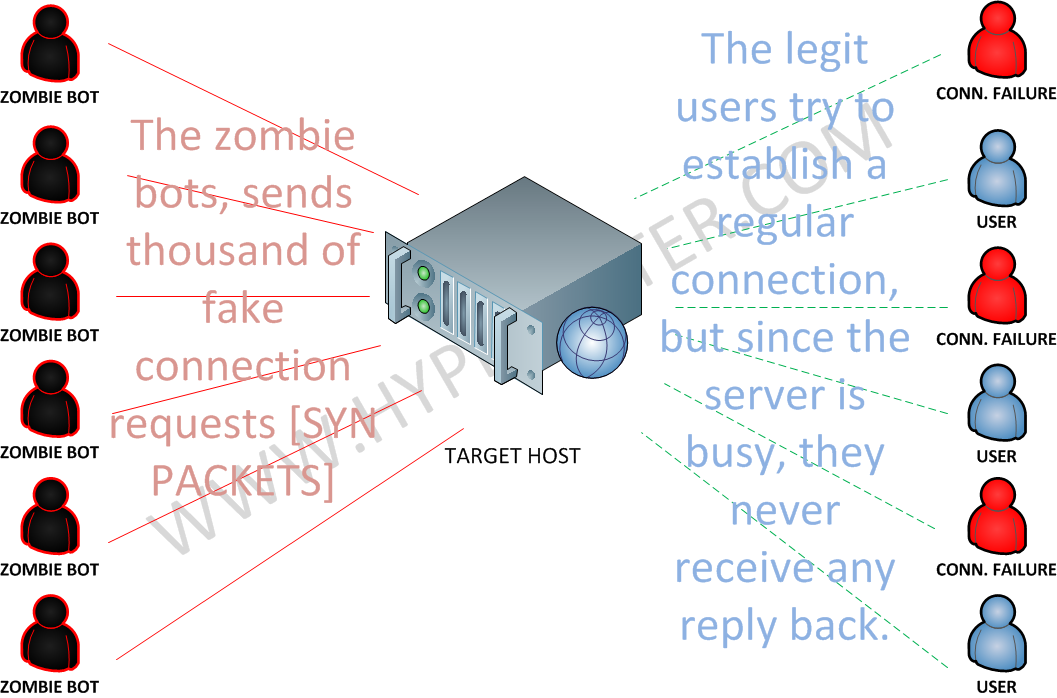
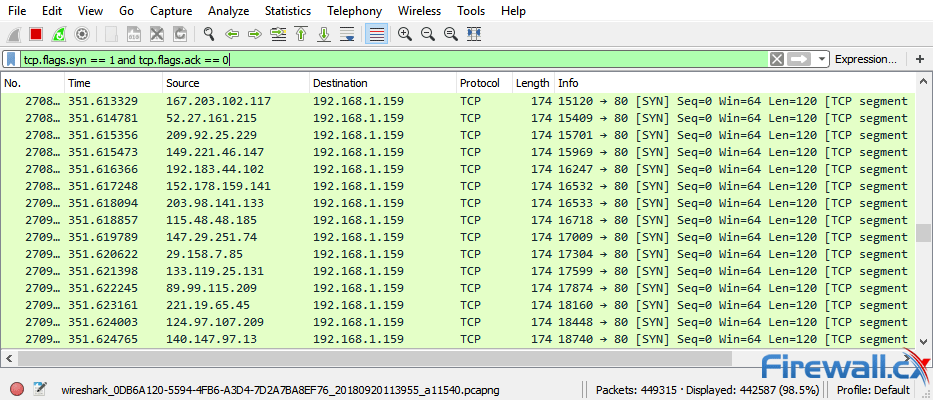

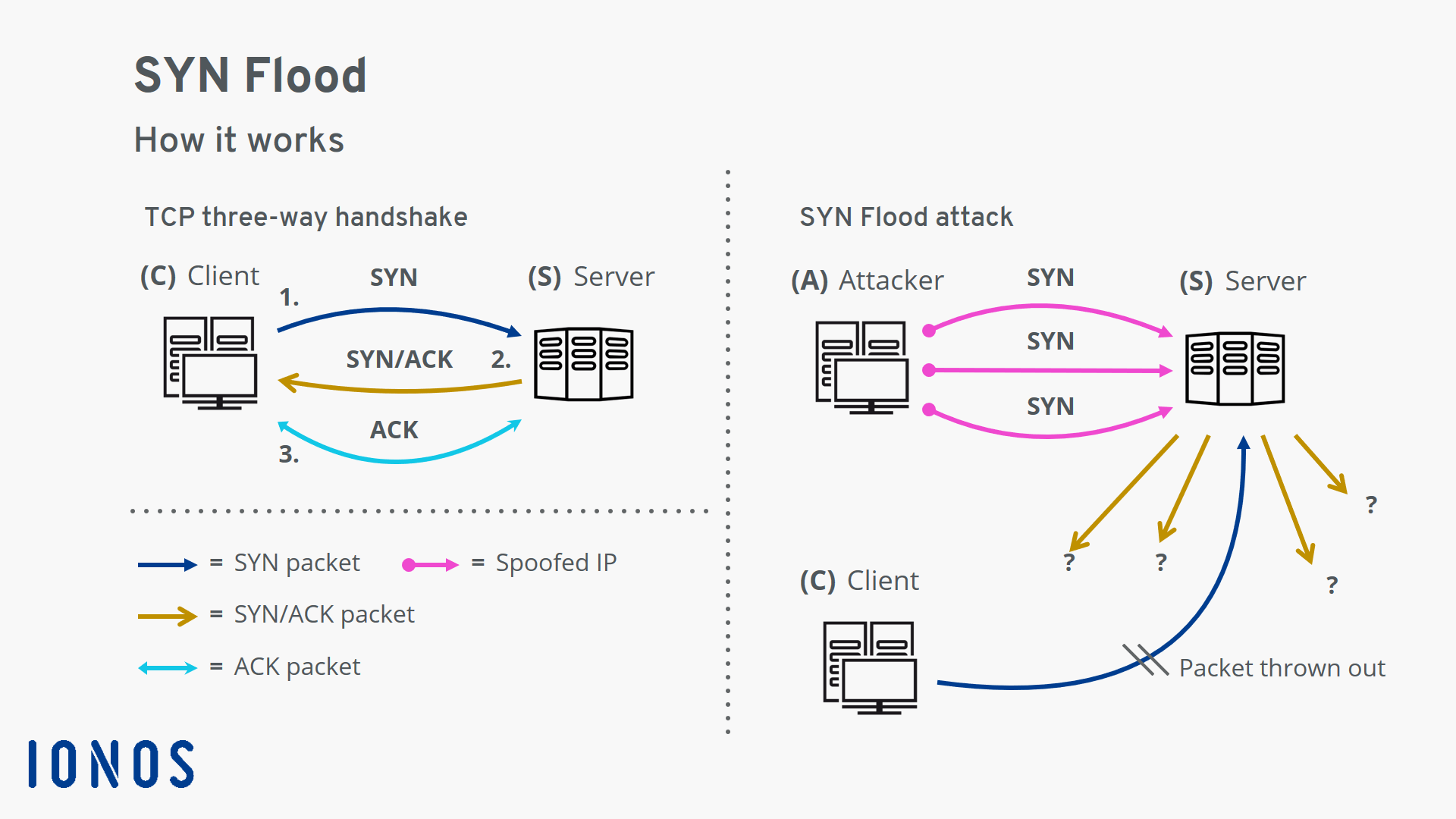


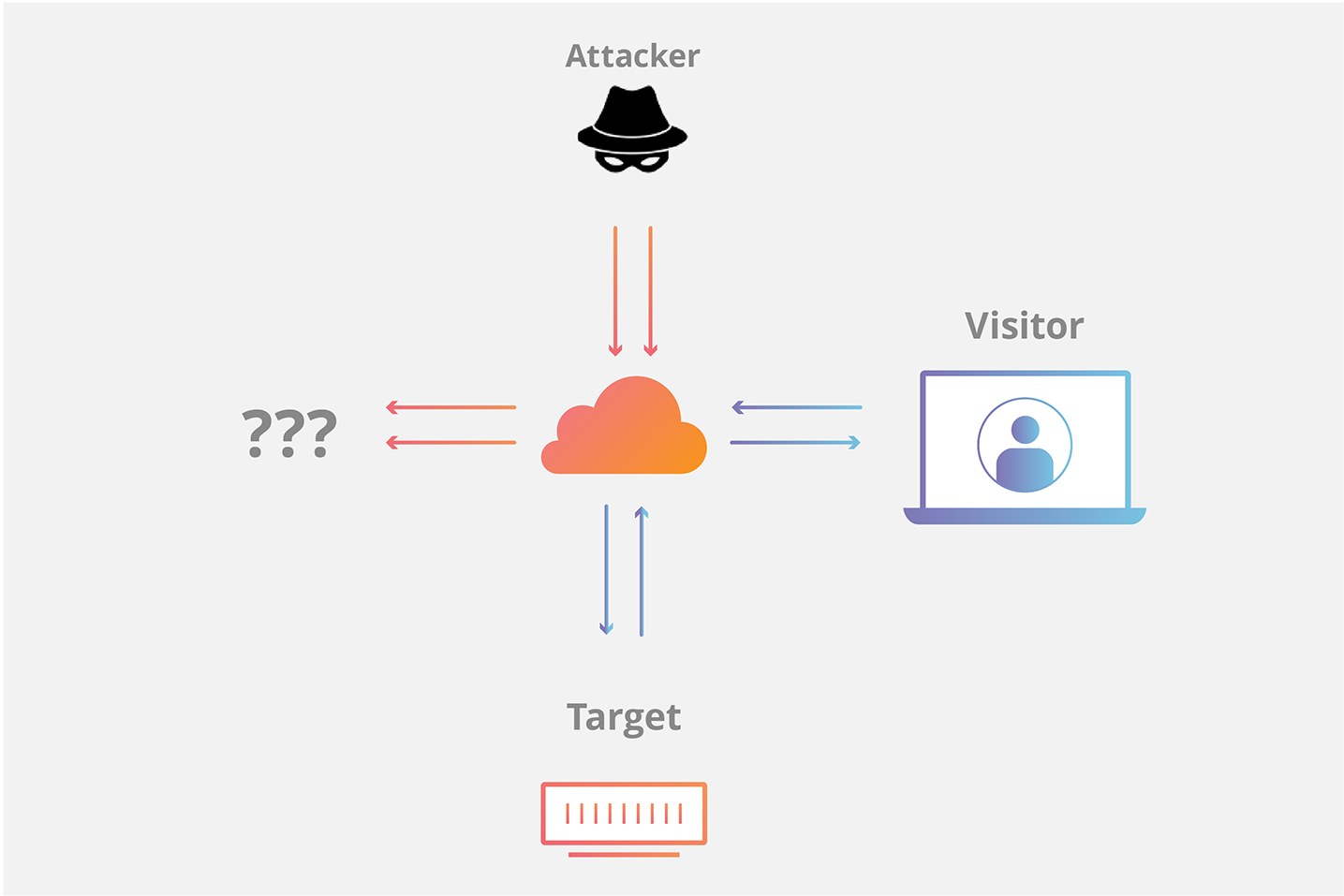
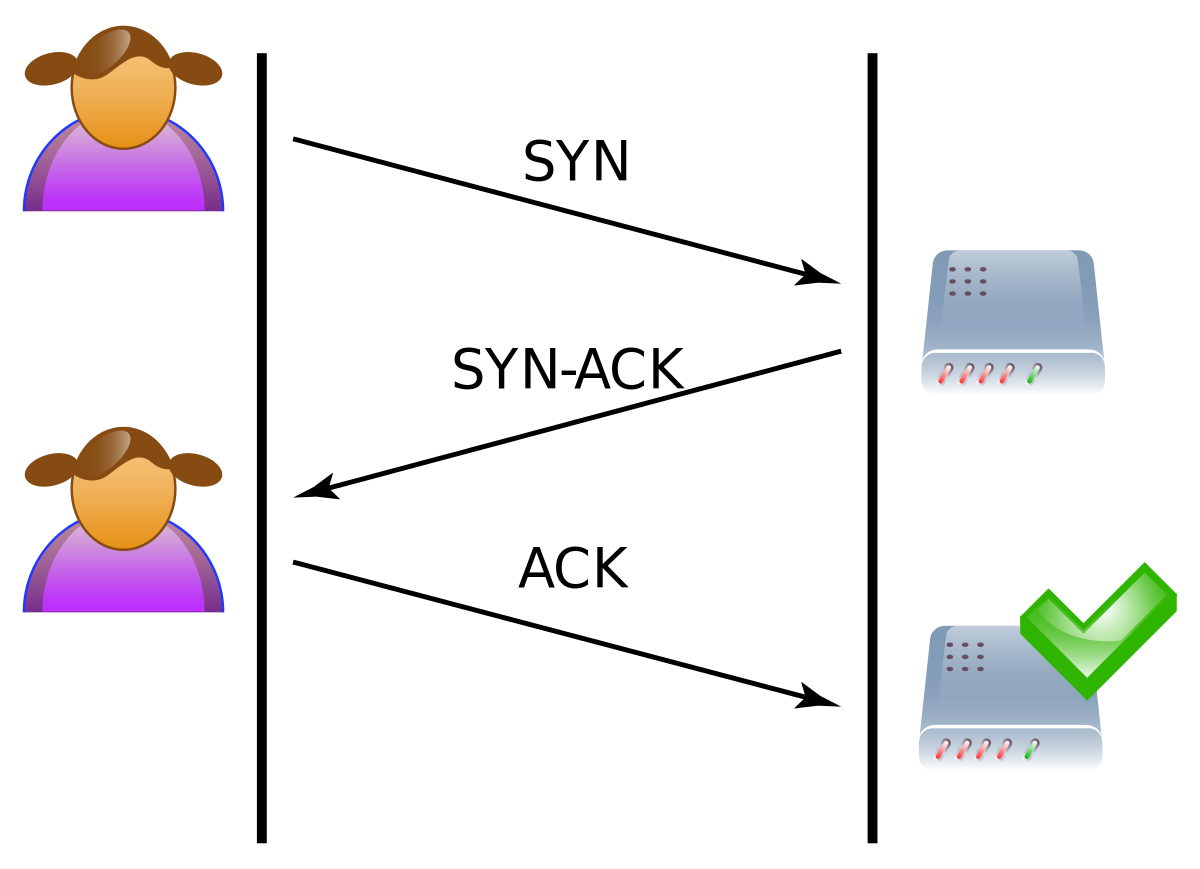
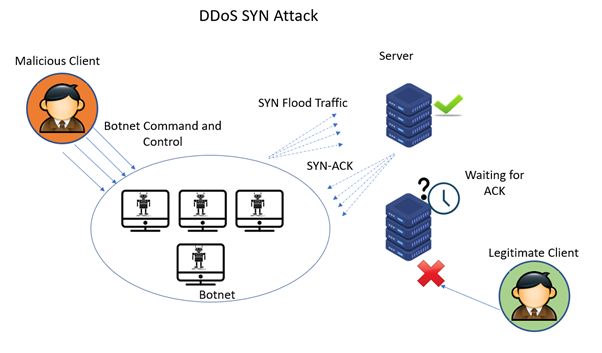

![PDF] TCP SYN Flood (DoS) Attack Prevention Using SPI Method on CSF: A PoC | Semantic Scholar PDF] TCP SYN Flood (DoS) Attack Prevention Using SPI Method on CSF: A PoC | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/21ae4e5d663ca7048d40c1e6dff82d118f7e3246/2-Figure1-1.png)



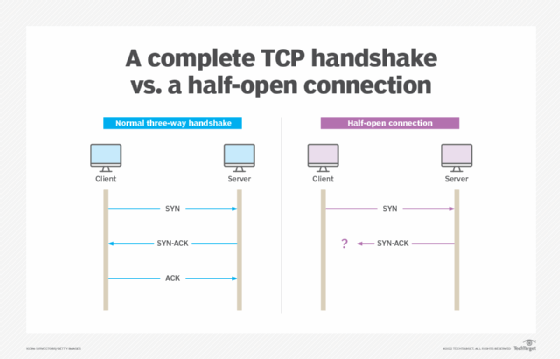
![PDF] TCP-SYN Flooding Attack in Wireless Networks | Semantic Scholar PDF] TCP-SYN Flooding Attack in Wireless Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/82dc0212fc9e66b2430715e6ae4b8210972f8420/2-Figure1-1.png)