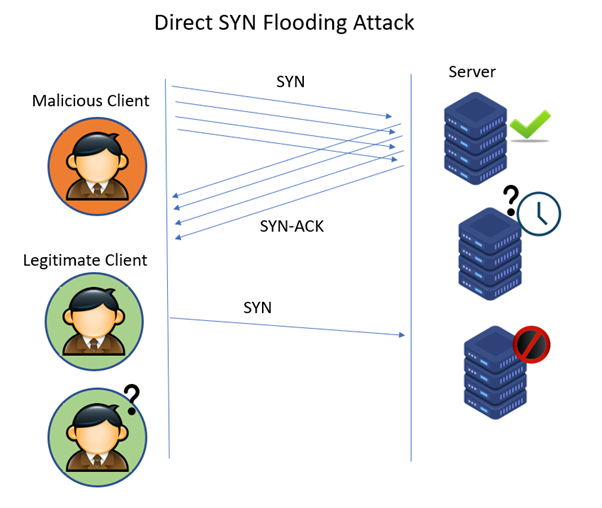
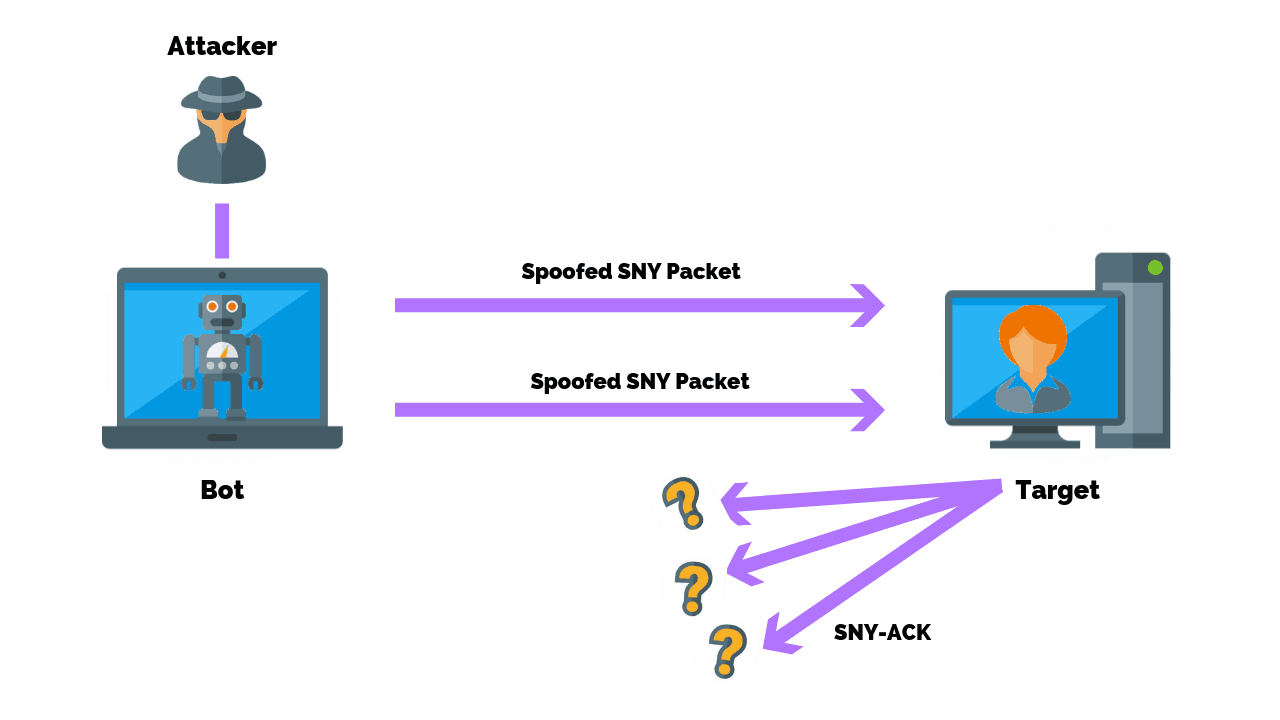
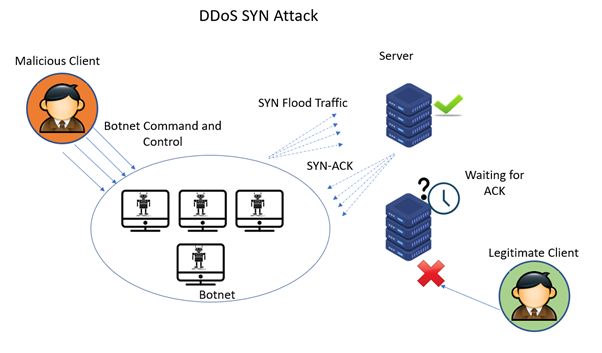
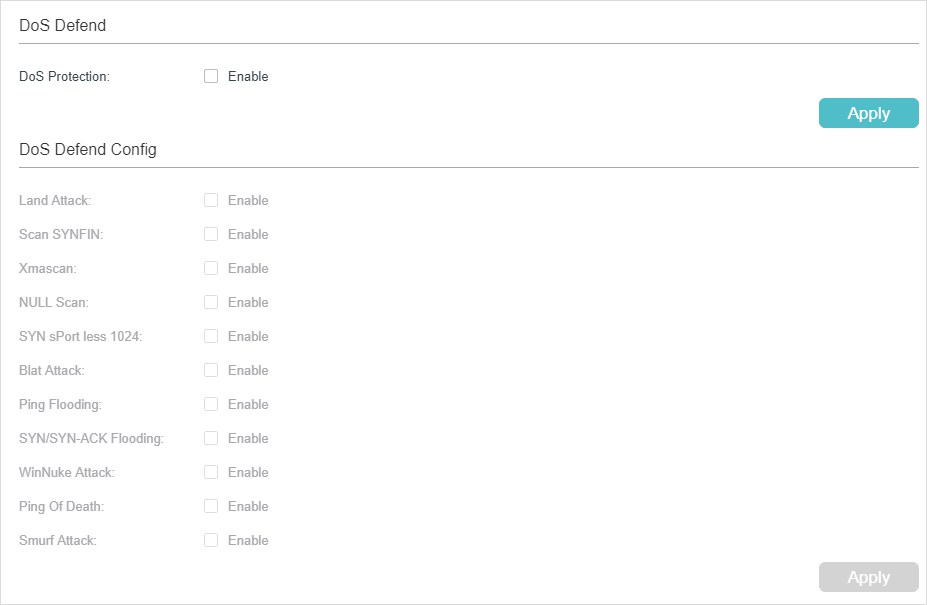
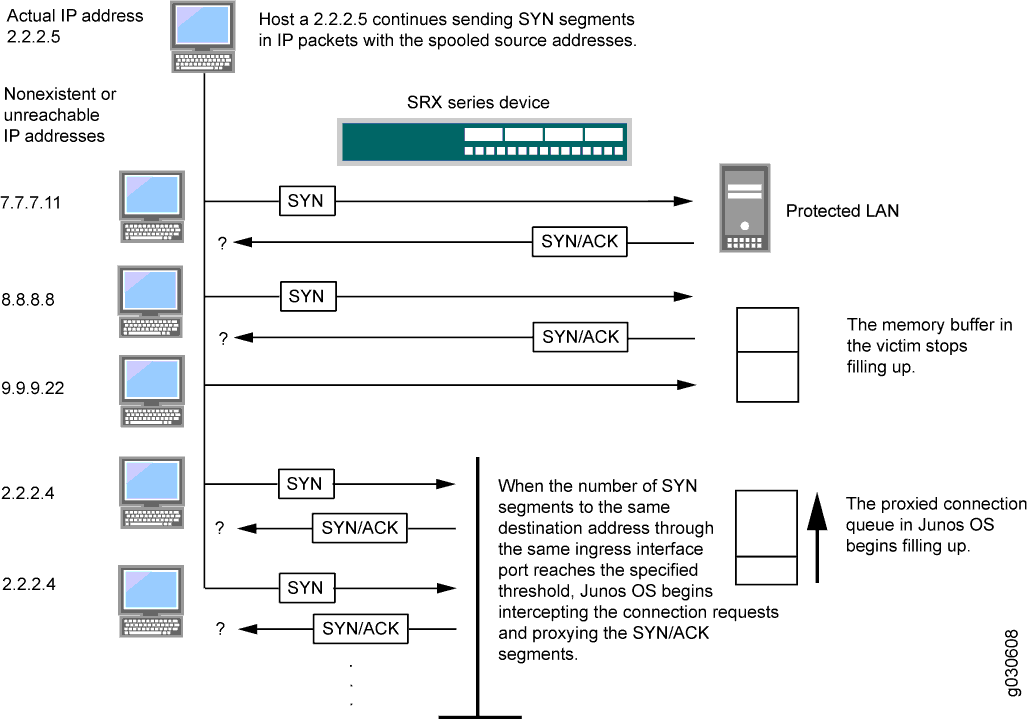
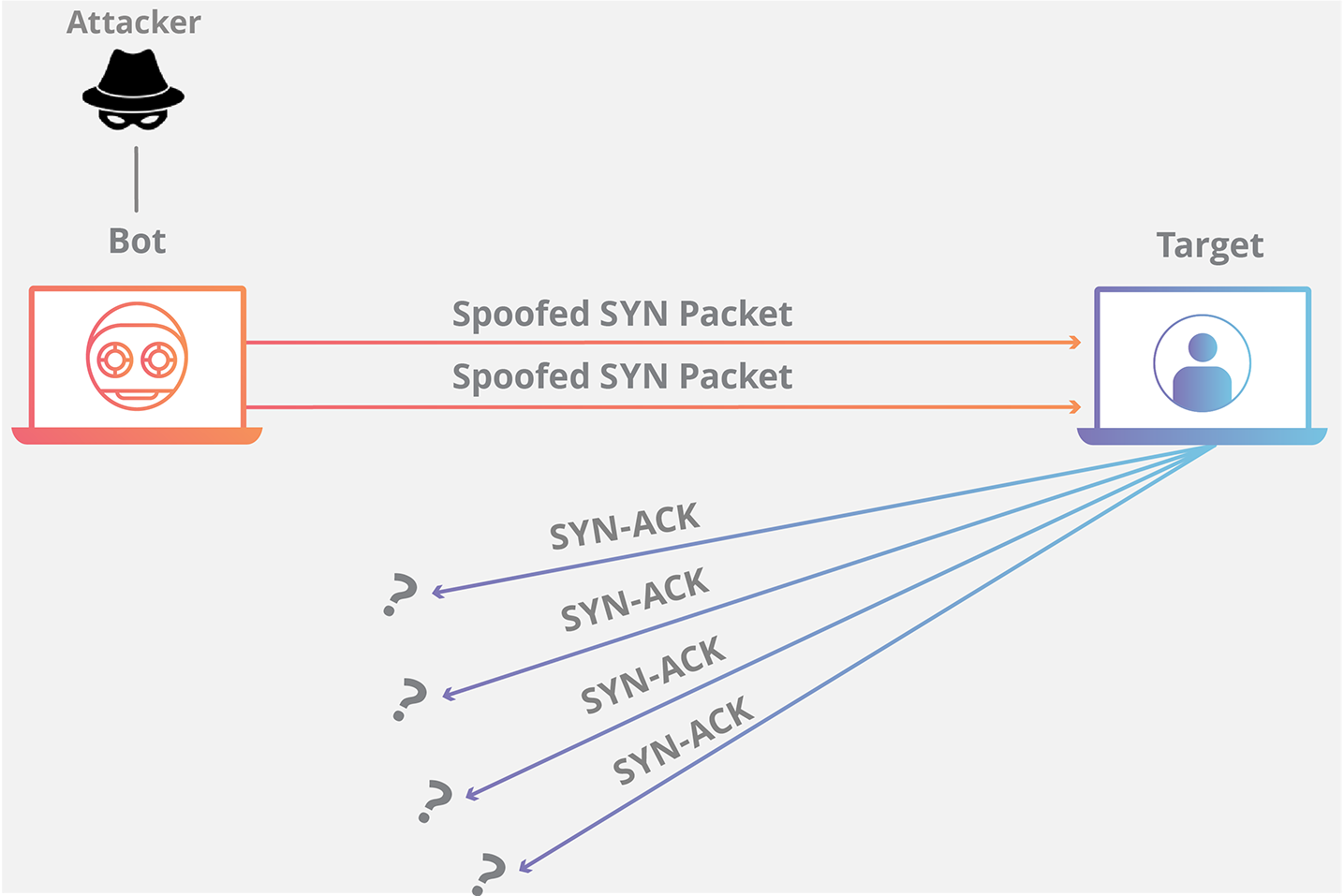
DOS Attack Ack Scan: What To Do When Your Router Logs It & How To Prevent One In The Future - One Computer Guy

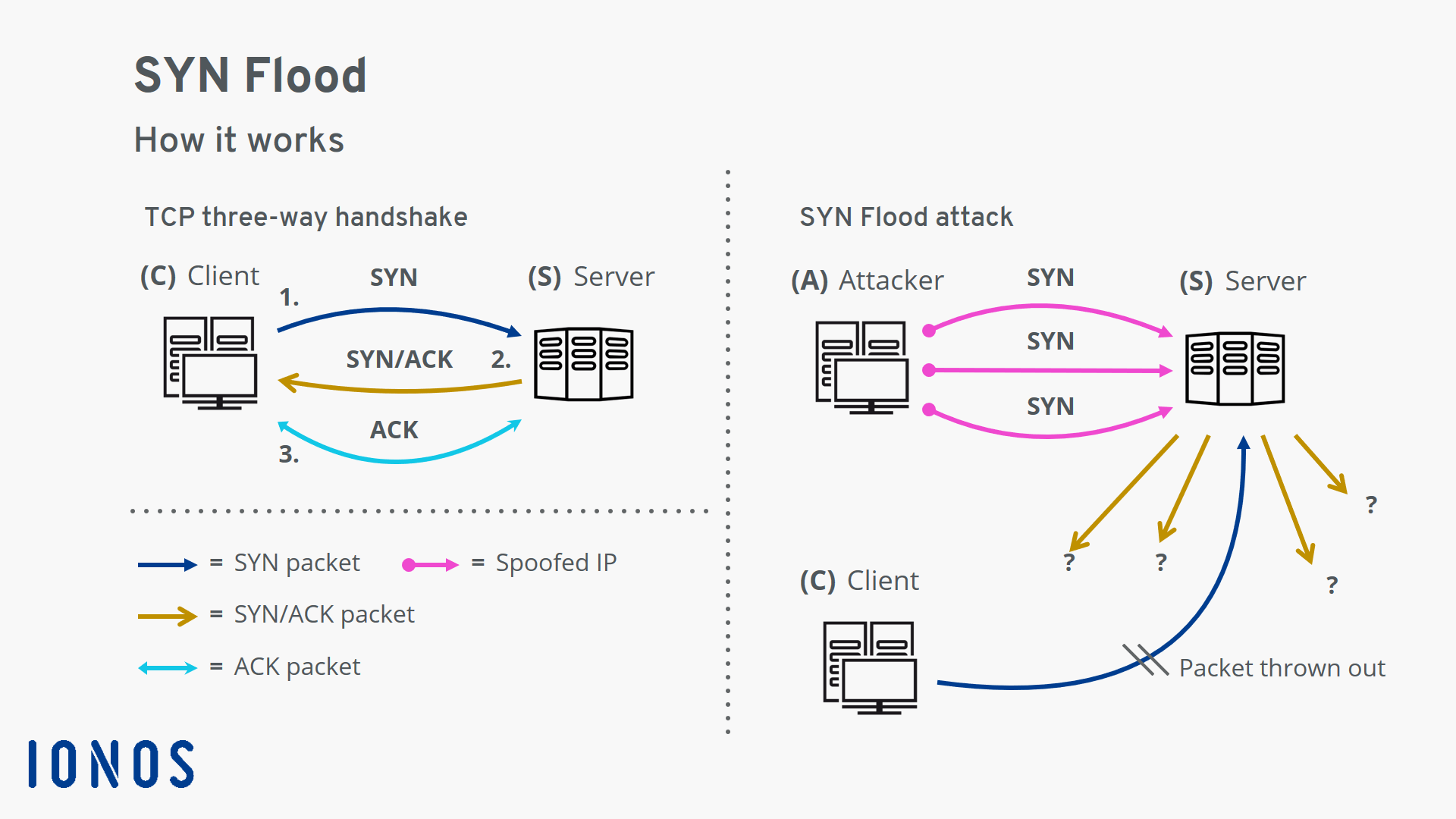
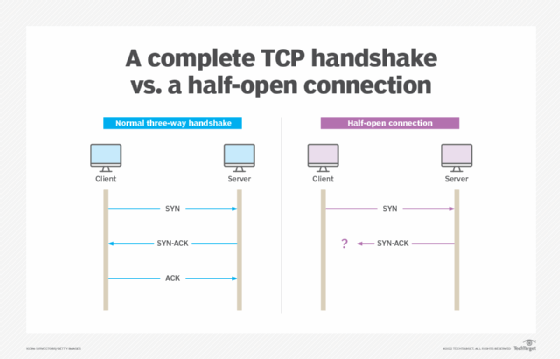
SYN flooding attack detection by TCP handshake anomalies - Bellaïche - 2012 - Security and Communication Networks - Wiley Online Library
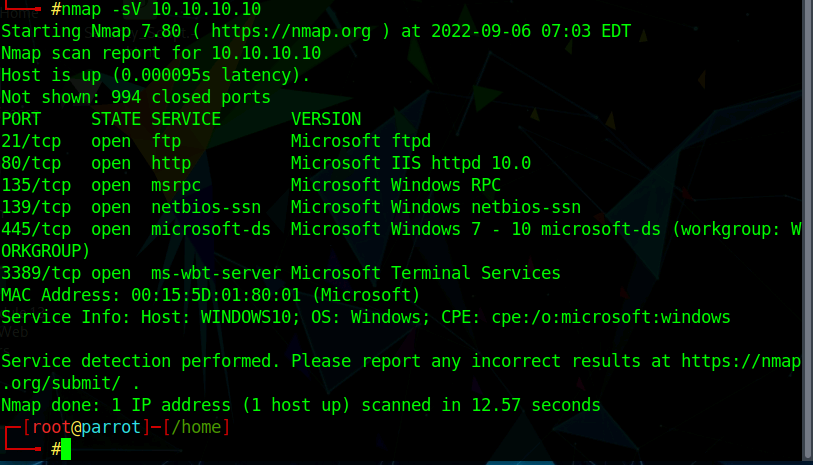
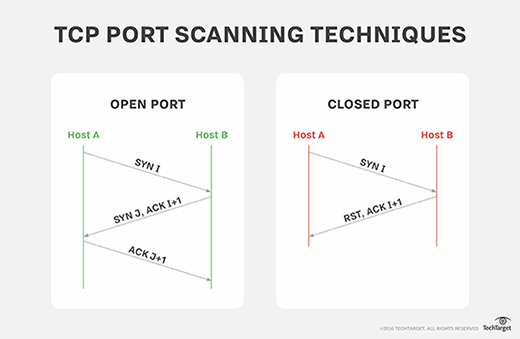
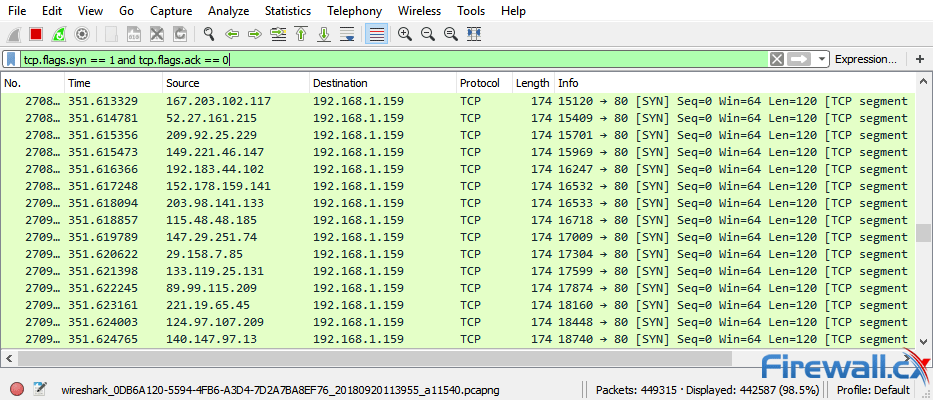
DoS Attack: SYN/ACK Scan] from source: 95.217.31.46, port 443, Friday, November 26, 2021 09:03:23 [DoS Attack: SYN/ACK Scan] fr