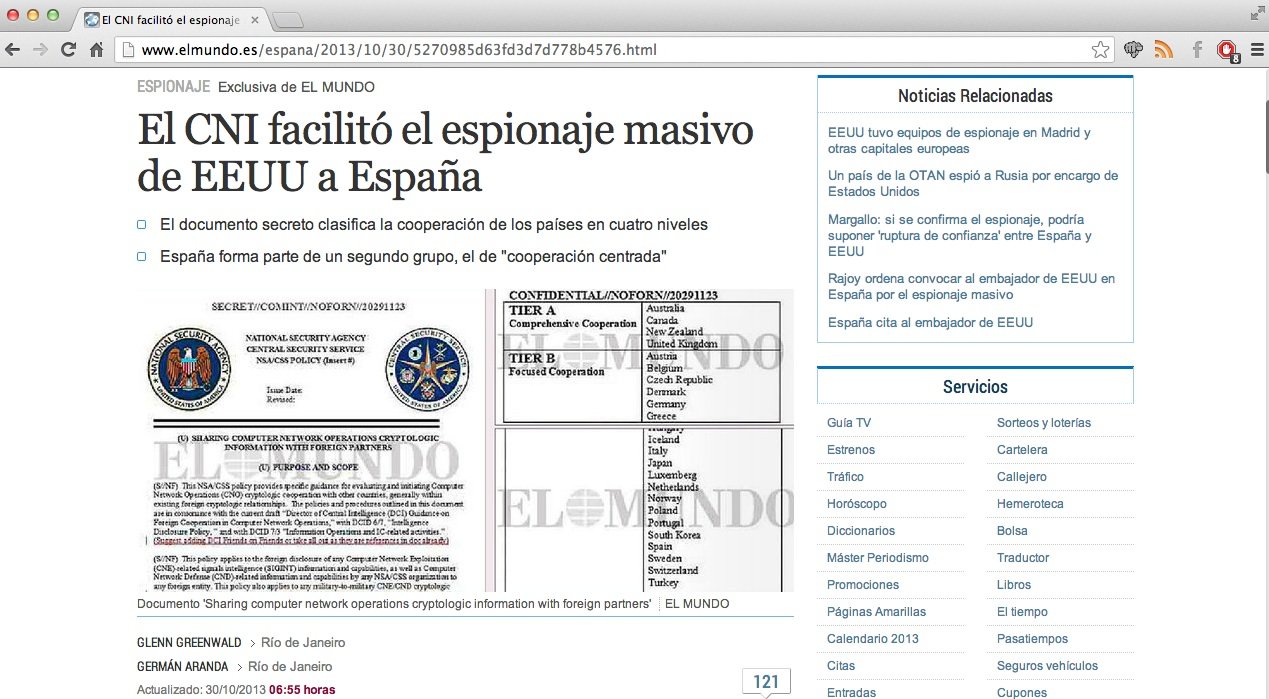
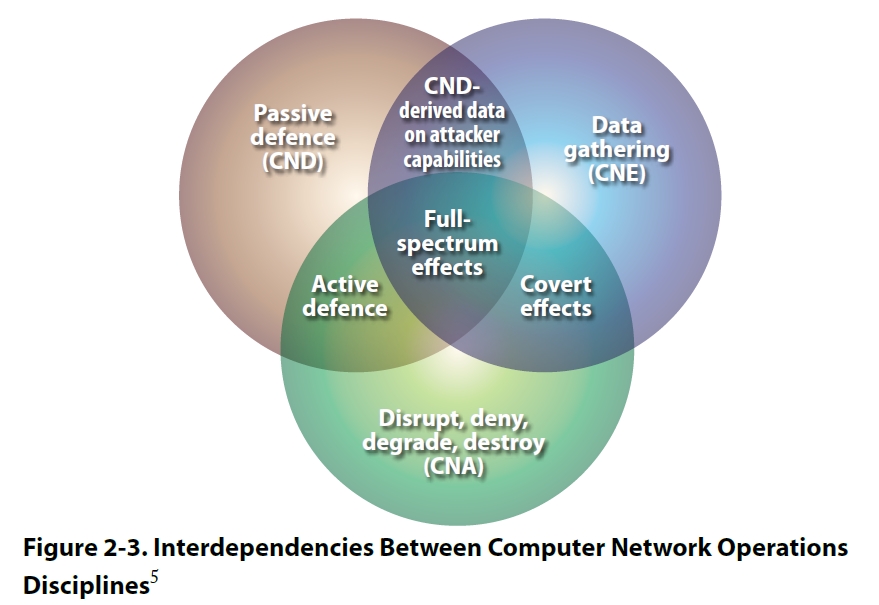
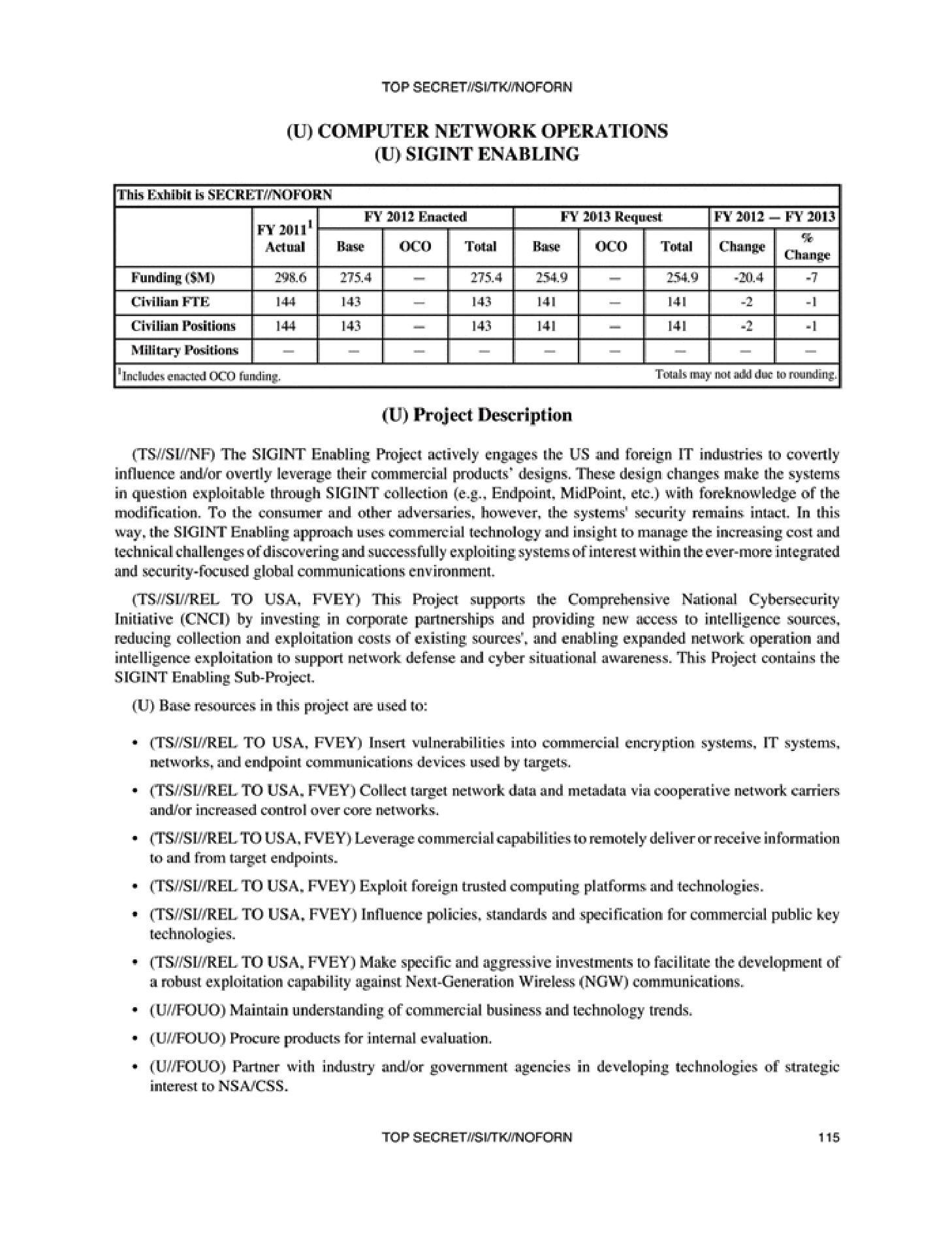
Preparing for Computer Network Operations: USCYBERCOM Documents Trace Path to Operational Cyber Force | National Security Archive

Air Force cadets take 2nd place in NSA cyber exercise > United States Air Force Academy > Air Force Academy News

China's computer network operations tasking to PLA unit structure (The... | Download Scientific Diagram

Christopher Moore - Computer Network Operations - Interactive Operator - National Security Agency | LinkedIn

Army looking for technically inclined Soldiers to apply for network operations program | Article | The United States Army