SHA1 Using JAVA and Its Explanation | PDF | String (Computer Science) | Theoretical Computer Science
GitHub - peterqt95/sha1: Implementation of the SHA-1 (Secure Hash Algorithm): Given a message in external memory, compute a 160-bit hash value. Implementation done in verilog. Reference: http://cwcserv.ucsd.edu/~billlin/classes/ECE111/final_project.php
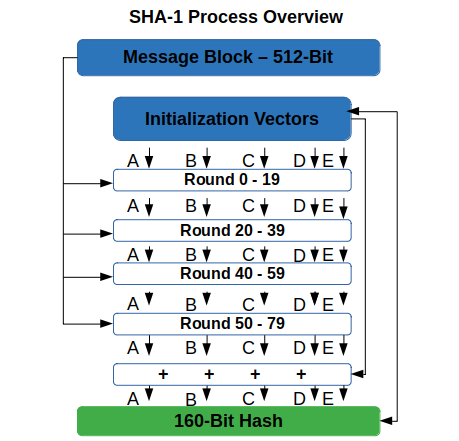
Steps of A PIN Generation. a) Secure Hash Function-1 SHA-1 is intricate... | Download Scientific Diagram

.jpg?1485252826)