Center for Computational Security sCience – Network security, Big data analytics and Network science

Computational Intelligence for Privacy and Security (Studies in Computational Intelligence, 394): Elizondo, David A., Solanas, Agusti, Martinez-Balleste, Antoni: 9783642252365: Amazon.com: Books
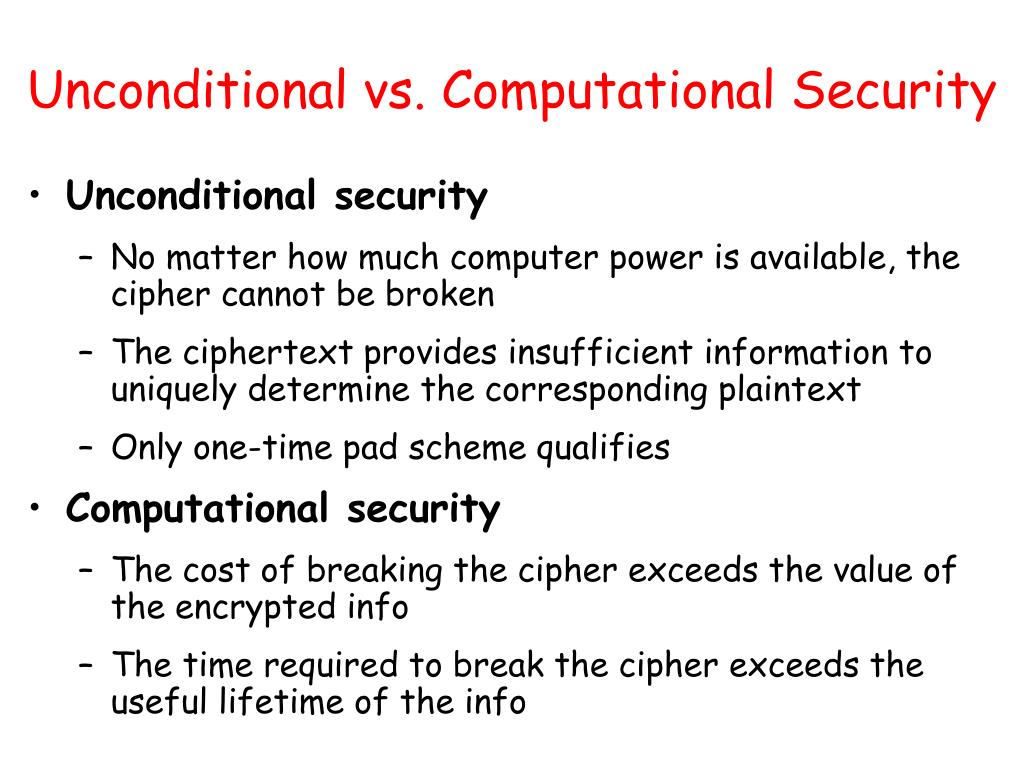
Computational Security against Eavesdropper • Constructing Secure Encryption Schemes against Eavesdropper

Computational Intelligence, Cyber Security and Computational Models. Recent Trends in Computational Models, Intelligent and Secure Systems eBook von – EPUB | Rakuten Kobo Österreich

Center for Computational Security sCience – Network security, Big data analytics and Network science

Impact of the depth parameter L on (a) computational time, (b) security... | Download Scientific Diagram

The Art of Modelling Computational Systems: A Journey from Logic and Concurrency to Security and Privacy - Alvim, Mário S.; Chatzikokolakis, Kostas; Olarte, Carlos;... - Dussmann - Das Kulturkaufhaus

International Joint Conference 15th International Conference on Computational Intelligence in Security for Information Systems (CISIS 2022) 13th International Conference on EUropean Transnational Education (ICEUTE 2022) (kartoniertes Buch ...

Computational Intelligence in Information Assurance and Security (Studies in Computational Intelligence, 57, Band 57) : Abraham, Ajith: Amazon.de: Bücher


![PDF] Computational Security for Cryptography | Semantic Scholar PDF] Computational Security for Cryptography | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1d7461754cd1359da51d3ce033ebddf02ed92c06/11-Figure2-1.png)