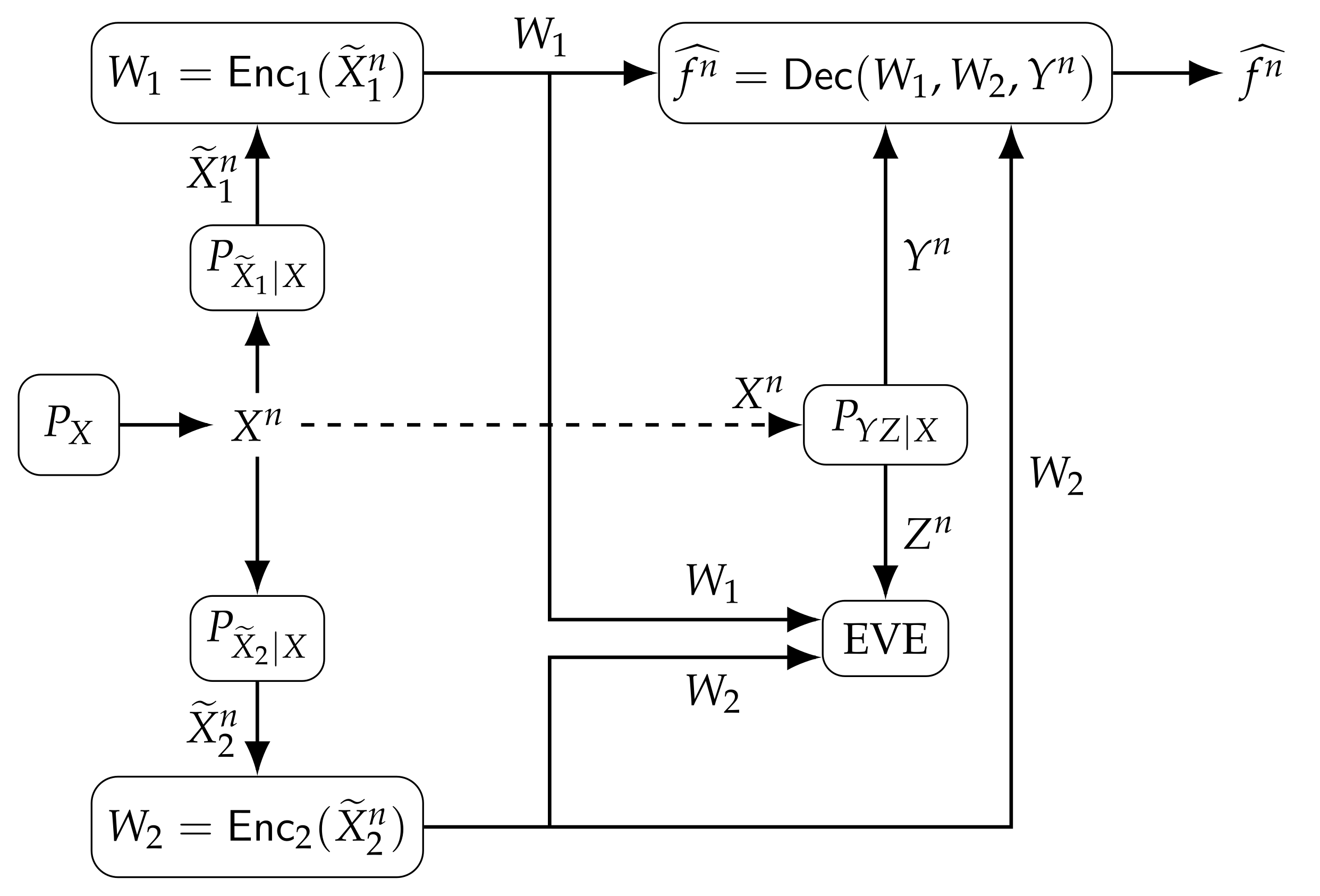
Entropy | Free Full-Text | Function Computation under Privacy, Secrecy, Distortion, and Communication Constraints
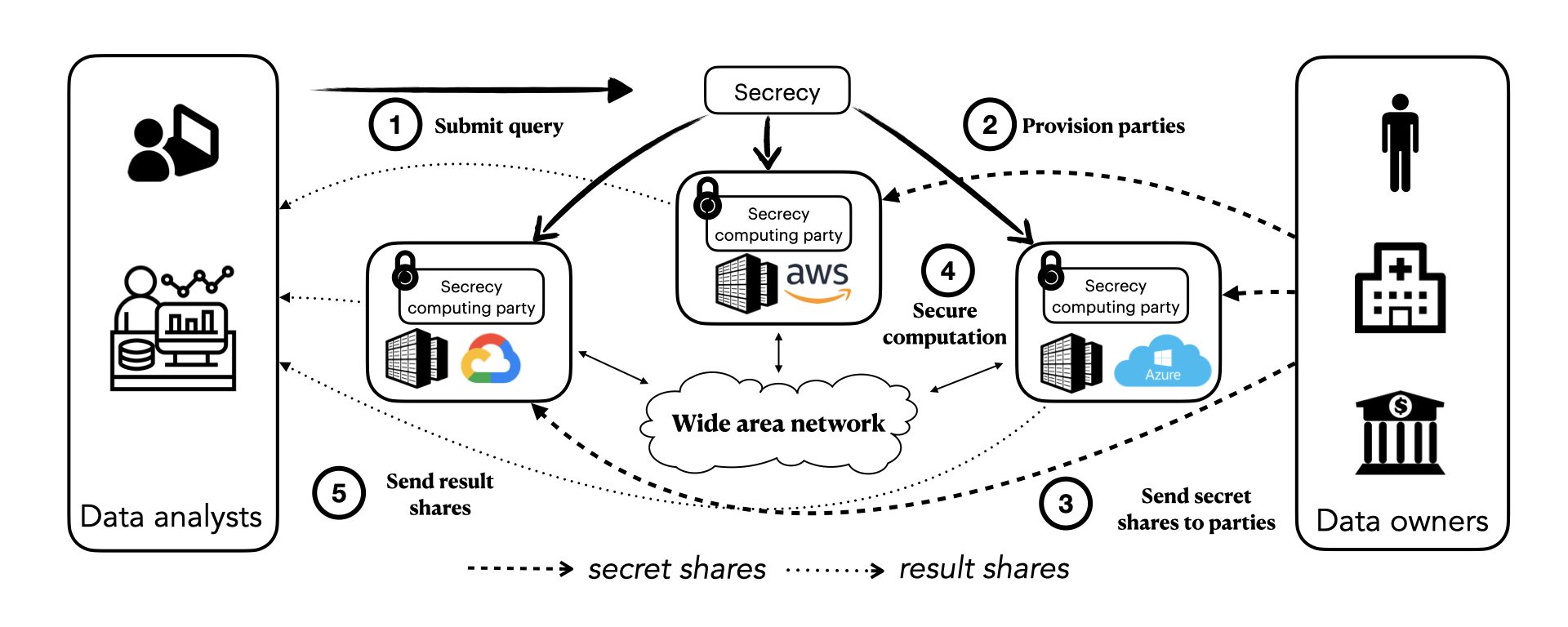
![PDF] Conditionally Secure Secrecy Computation using Secret Sharing Scheme for n<2k-1 (full paper) | Semantic Scholar PDF] Conditionally Secure Secrecy Computation using Secret Sharing Scheme for n<2k-1 (full paper) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/913dc7d927a9b3ac9734b5a4ca7fd69291f145b7/18-Table1-1.png)
PDF] Conditionally Secure Secrecy Computation using Secret Sharing Scheme for n<2k-1 (full paper) | Semantic Scholar

CryptographyPerfect secrecySlide 1 Today What does it mean for a cipher to be: –Computational secure? Unconditionally secure? Perfect secrecy –Conditional. - ppt download
![PDF] Conditionally Secure Secrecy Computation using Secret Sharing Scheme for n<2k-1 (full paper) | Semantic Scholar PDF] Conditionally Secure Secrecy Computation using Secret Sharing Scheme for n<2k-1 (full paper) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/913dc7d927a9b3ac9734b5a4ca7fd69291f145b7/10-Figure2-1.png)
PDF] Conditionally Secure Secrecy Computation using Secret Sharing Scheme for n<2k-1 (full paper) | Semantic Scholar

PDF) Logic of Perfect Secrecy in Àrokò Computational Cryptography | Longe I Oluwaseun - Academia.edu





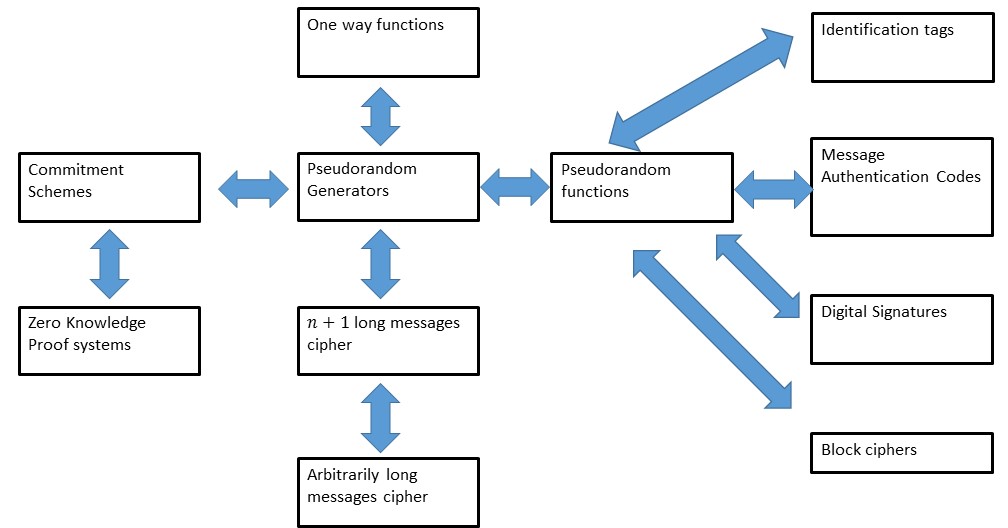


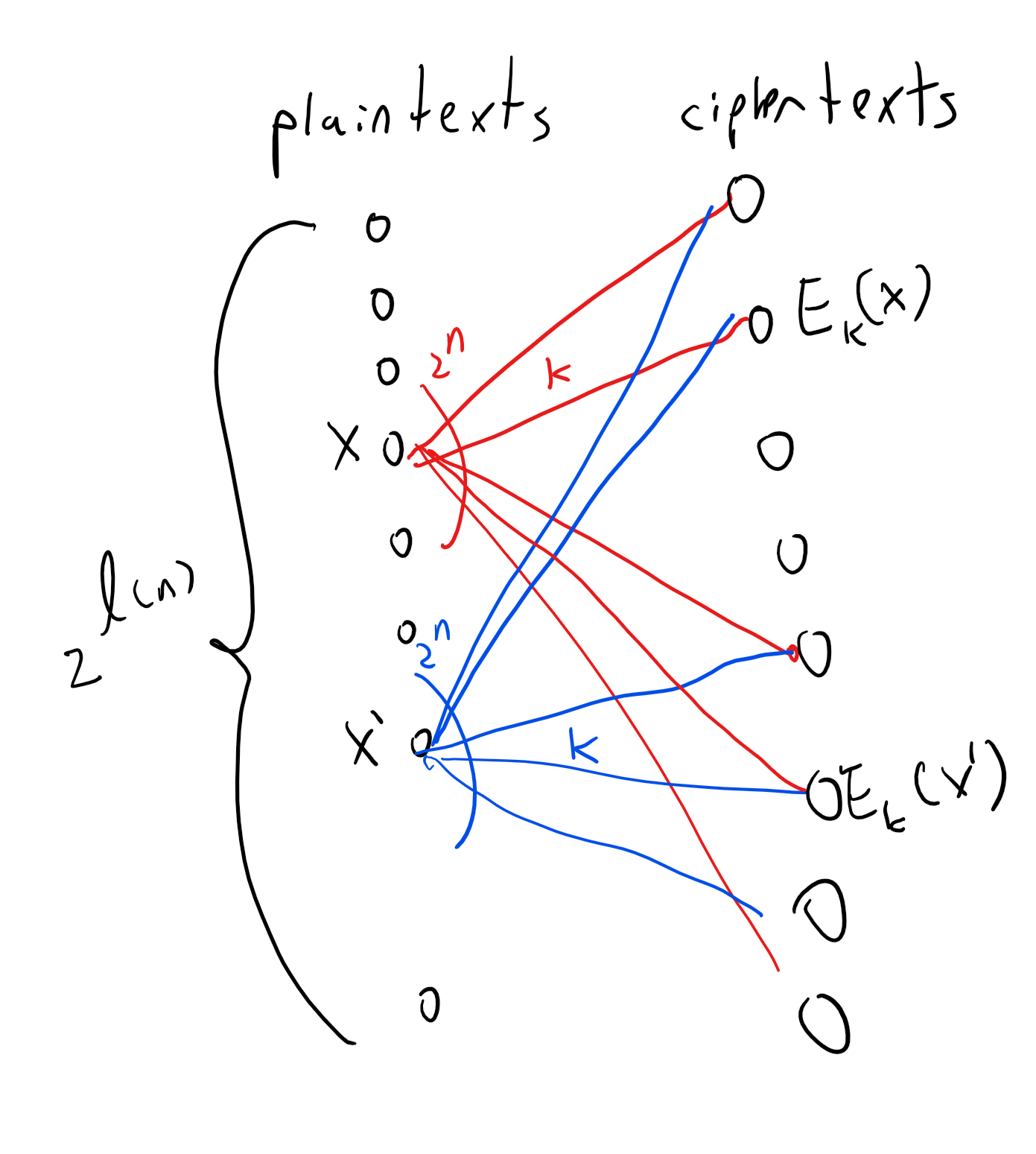

![Cryptography(암호학)] 2주차-Computational Secrecy and Principles of Modern Cryptography Cryptography(암호학)] 2주차-Computational Secrecy and Principles of Modern Cryptography](https://velog.velcdn.com/images/y3yun/post/3fa9abc1-5209-480a-8436-4200740437bb/image.jpeg)

