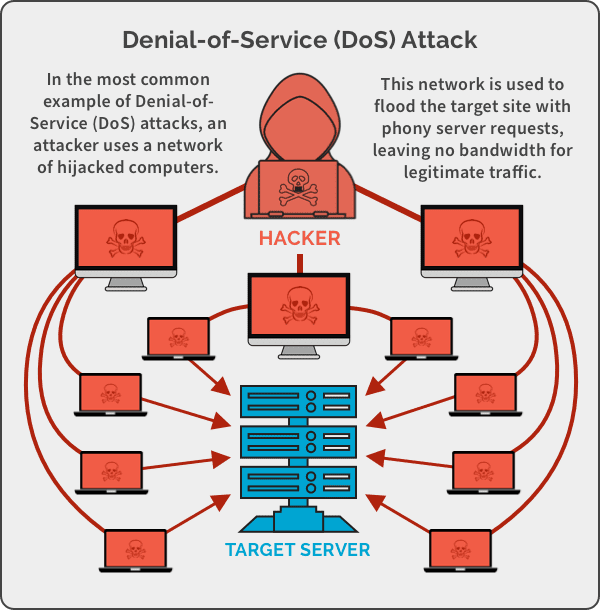
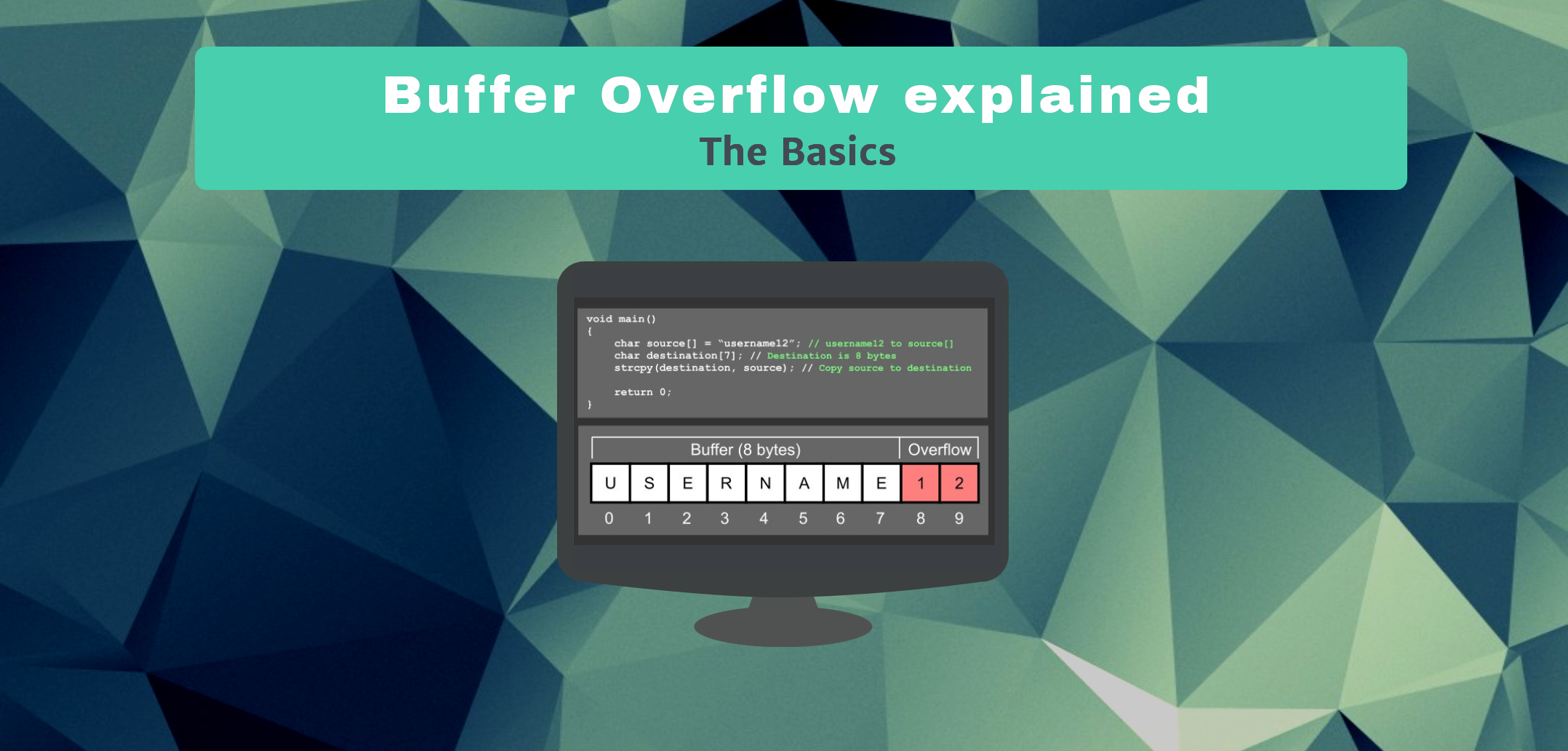
Security News on Twitter: "RT @tht_en: Buffer Overflow Attack❗ #cybersecurity #cyberattack #data #attack #attacker #system #machine #network #buffer #program #dos #d…" / Twitter
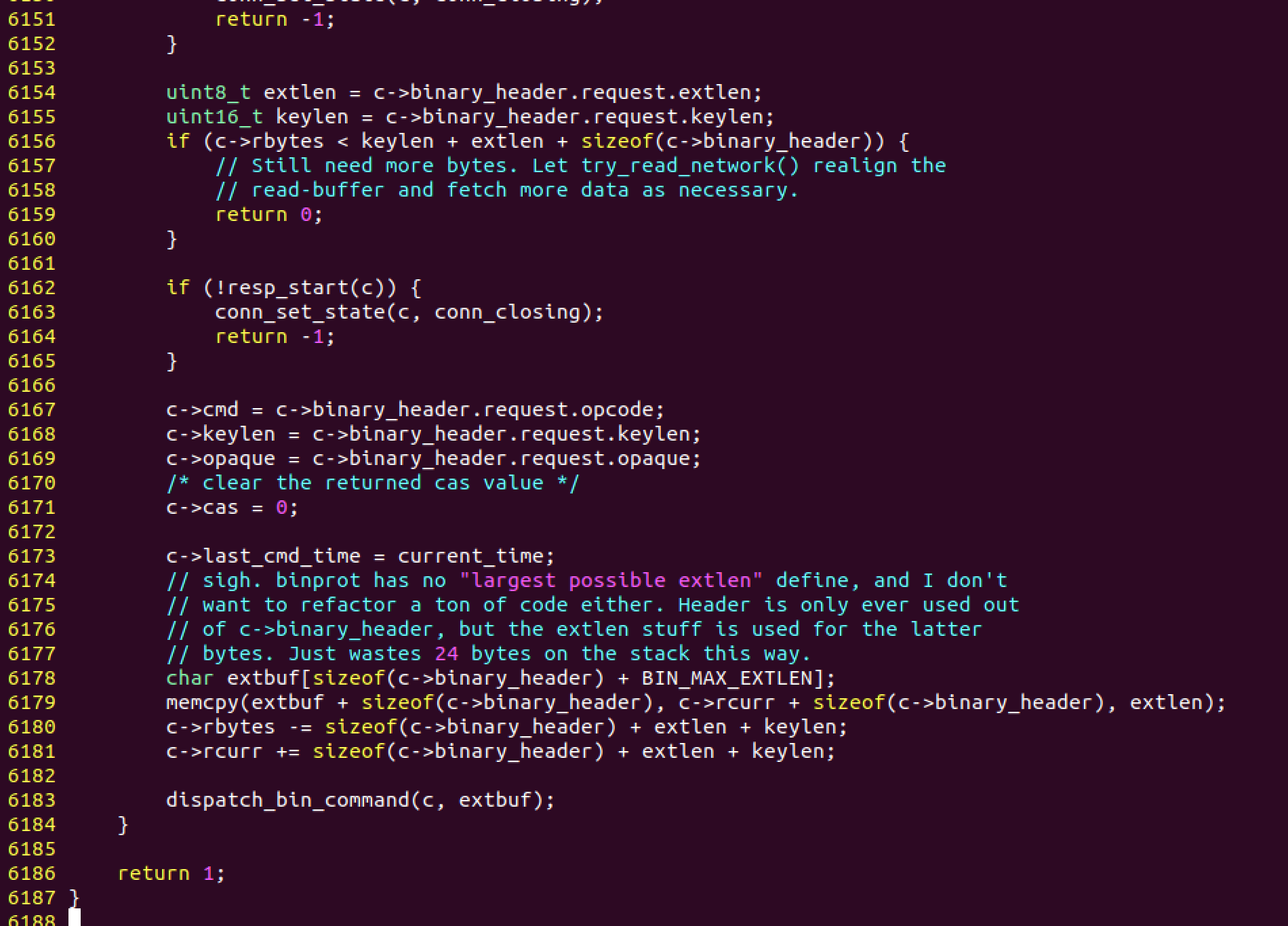
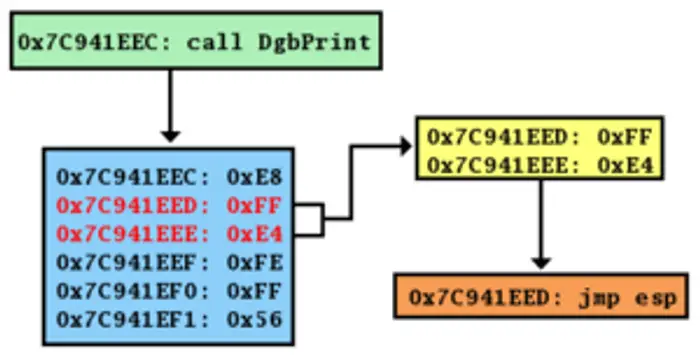
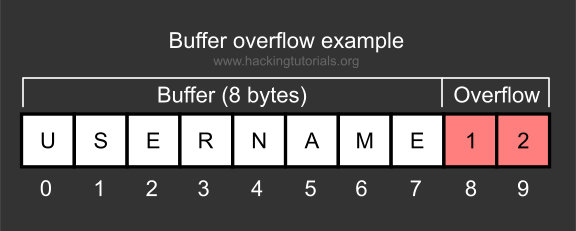
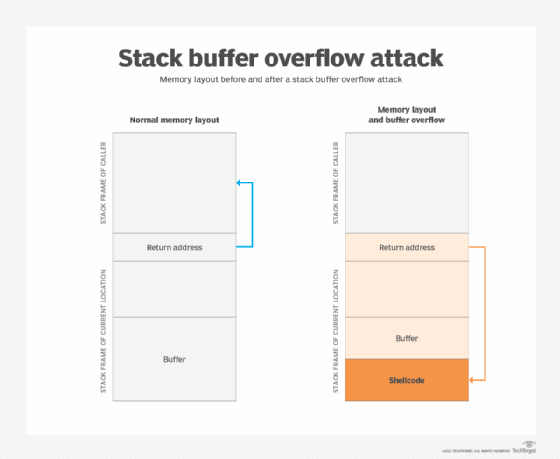
Remote DOS attack) 0day buffer overflow vulnerability reveal · Issue #629 · memcached/memcached · GitHub