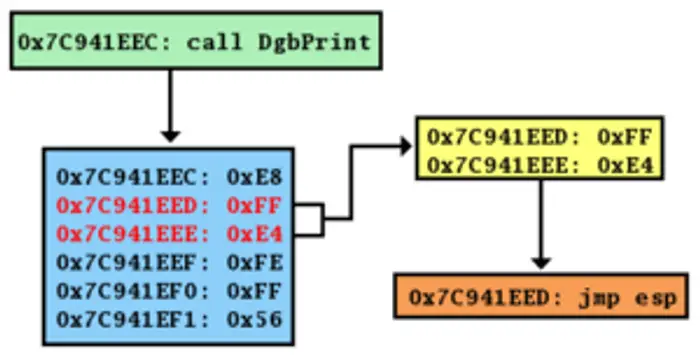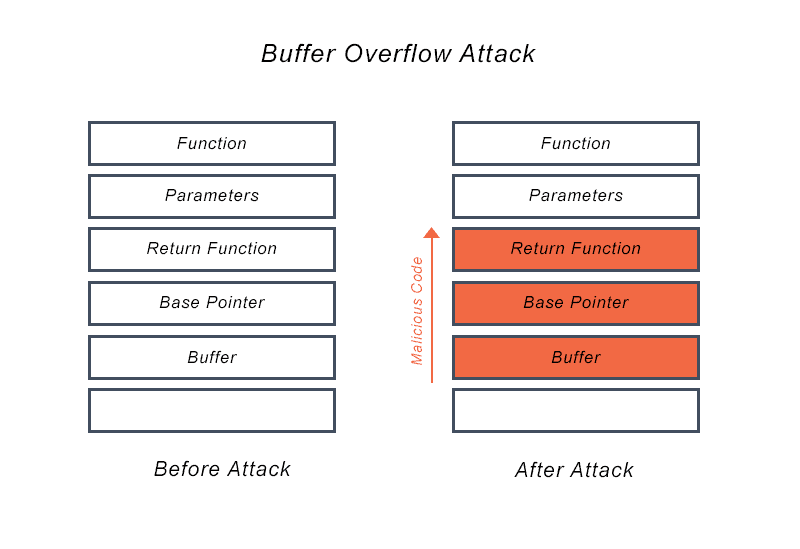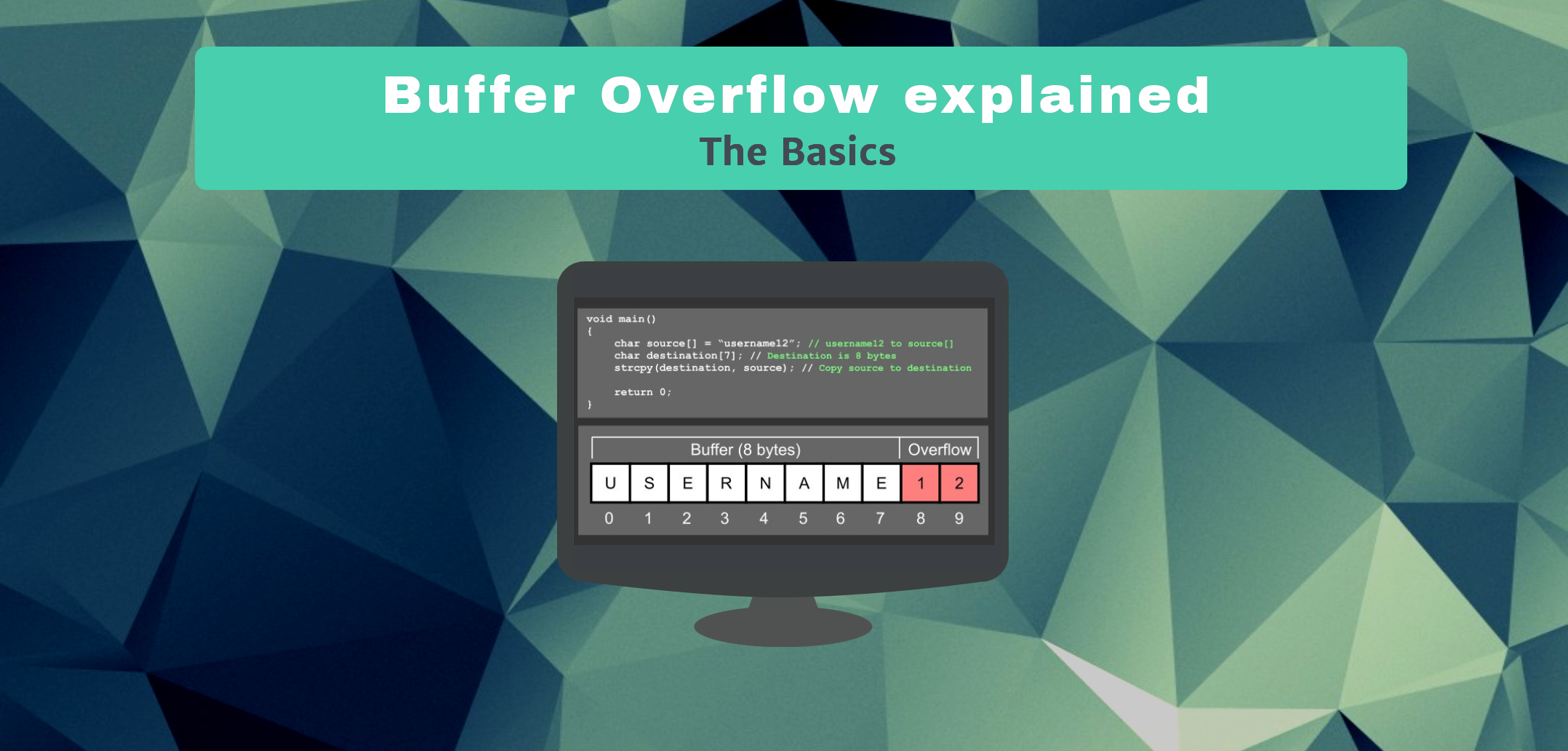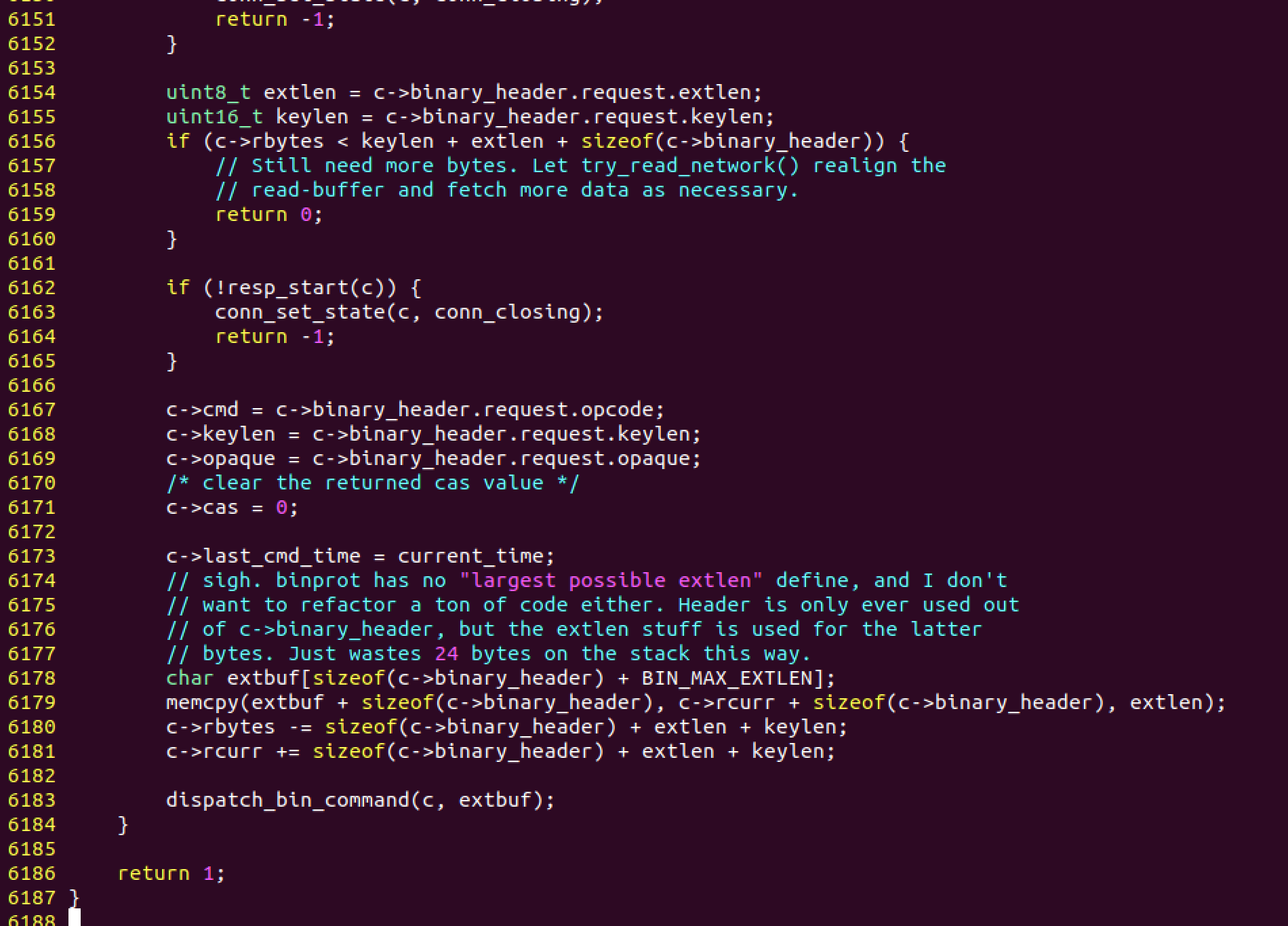
Remote DOS attack) 0day buffer overflow vulnerability reveal · Issue #629 · memcached/memcached · GitHub

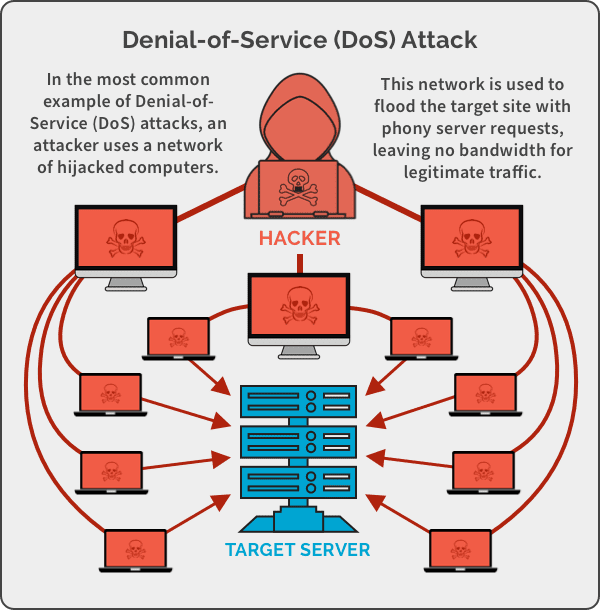
Different Types of Network Attacks And Security Threats and Counter Measures | Types of network, Denial of service attack, Attack
Remote DOS attack) 0day buffer overflow vulnerability reveal · Issue #629 · memcached/memcached · GitHub