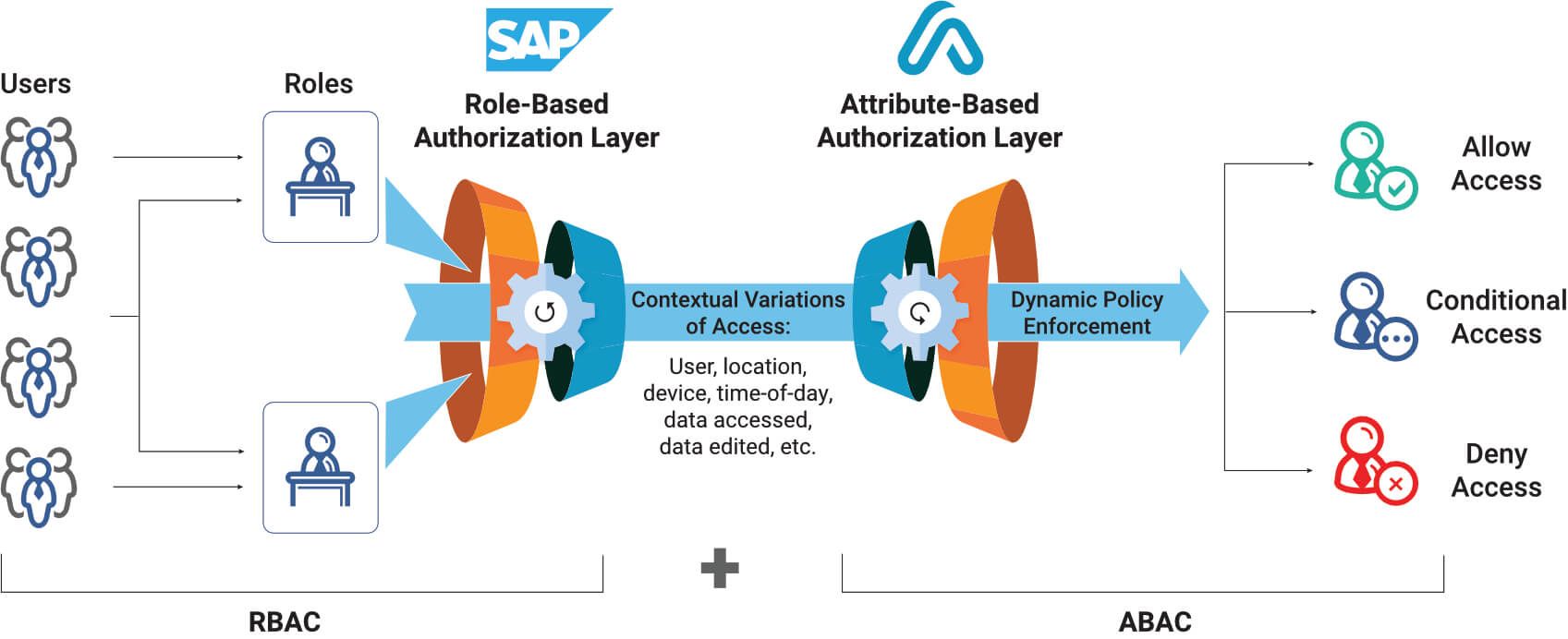
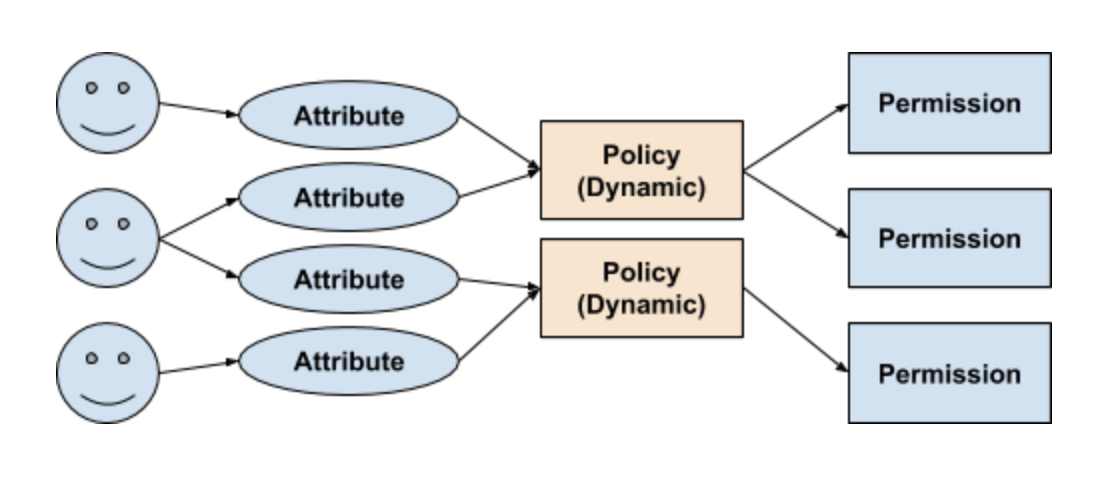
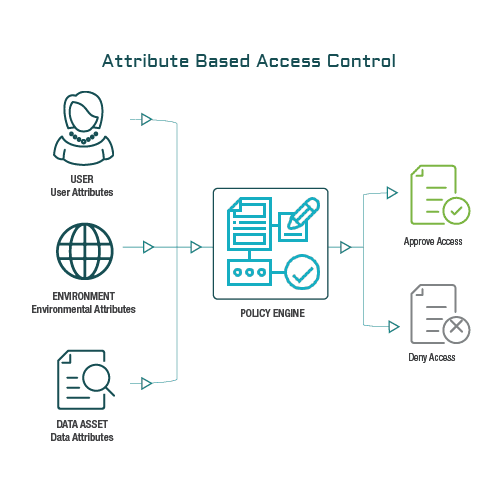
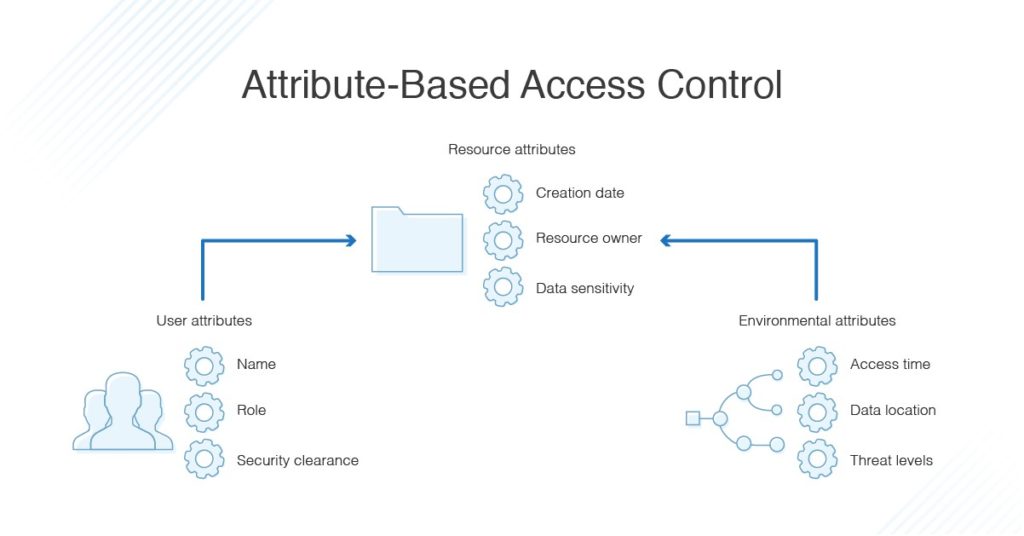
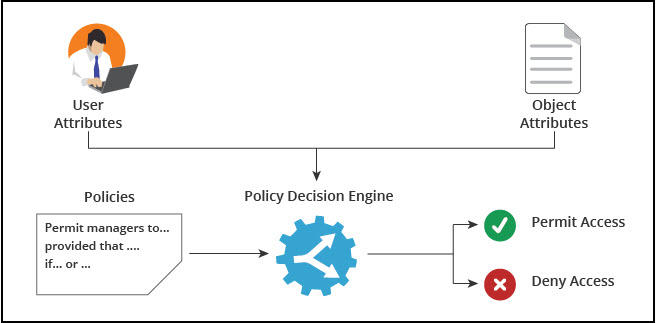
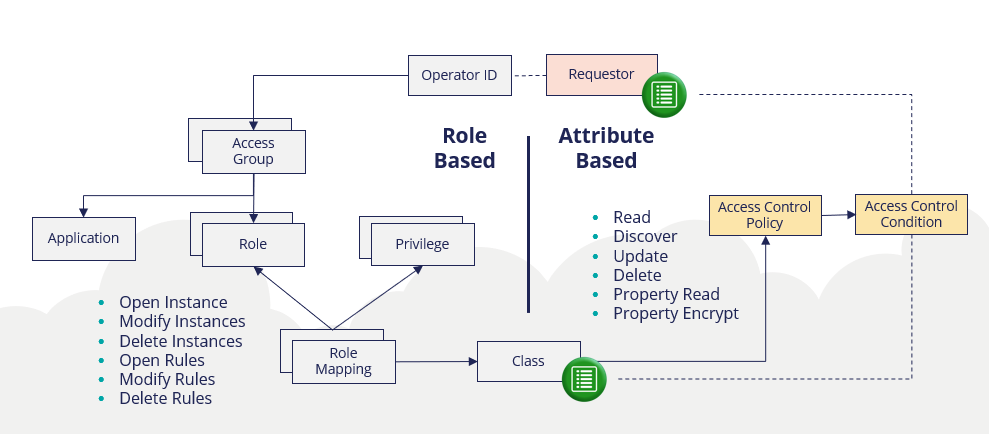
permissions - What is a suggested roadmap towards implementation of a simple Attribute-based access control (ABAC)? - Software Engineering Stack Exchange
ATTRIBUTE-BASED ACCESS AND COMMUNICATION CONTROL MODELS FOR CLOUD AND CLOUD-ENABLED INTERNET OF THINGS

Managing attribute-based access control policies in a unified framework using data warehousing and in-memory database - ScienceDirect