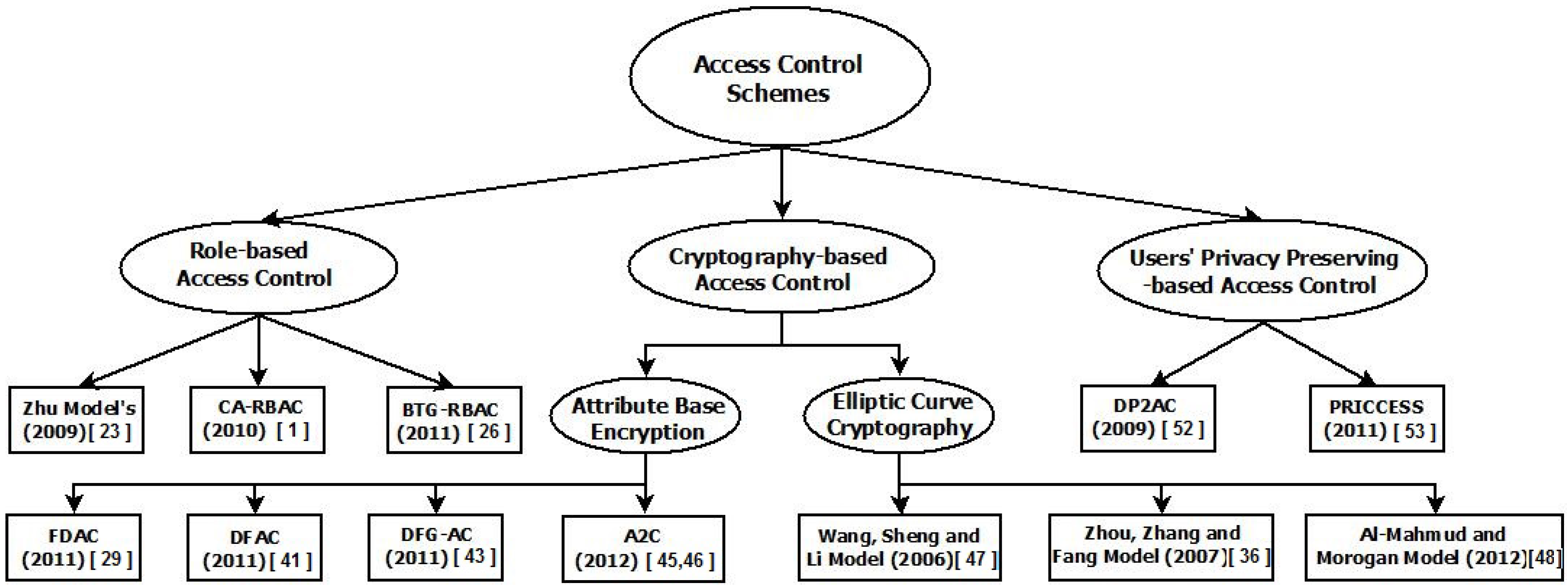
A survey on privacy and access control schemes in fog computing - Khalid - 2021 - International Journal of Communication Systems - Wiley Online Library

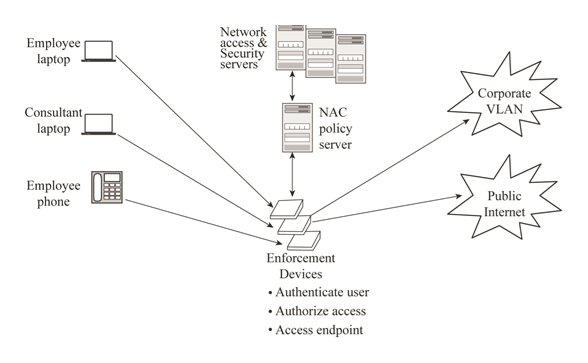
On medium access control schemes for wireless networks in the millimeter-wave and Terahertz bands - ScienceDirect

A novel and efficient user access control scheme for wireless body area sensor networks - ScienceDirect
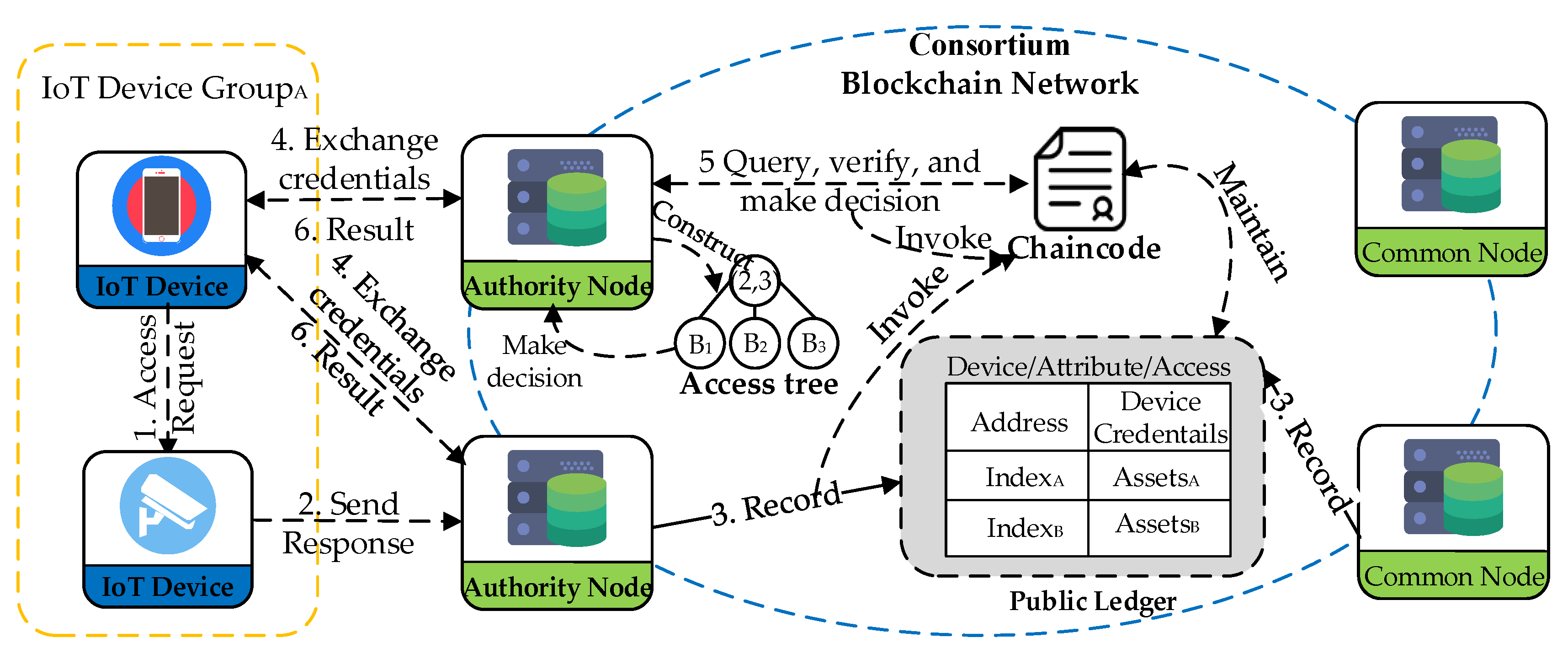
Electronics | Free Full-Text | An Attribute-Based Collaborative Access Control Scheme Using Blockchain for IoT Devices

Electronics | Free Full-Text | An Attribute-Based Collaborative Access Control Scheme Using Blockchain for IoT Devices
![PDF] A Secure and Verifiable Access Control Scheme for Big Data Storage in Clouds | Semantic Scholar PDF] A Secure and Verifiable Access Control Scheme for Big Data Storage in Clouds | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f89b6873e639eb4c316187ffeca8c5094c017eba/2-Figure1-1.png)
PDF] A Secure and Verifiable Access Control Scheme for Big Data Storage in Clouds | Semantic Scholar



![PDF] Privacy protection based access control scheme in cloud-based services | Semantic Scholar PDF] Privacy protection based access control scheme in cloud-based services | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4409cb0b18485f7935d8596aae542d6646e3f1e4/3-Figure3-1.png)

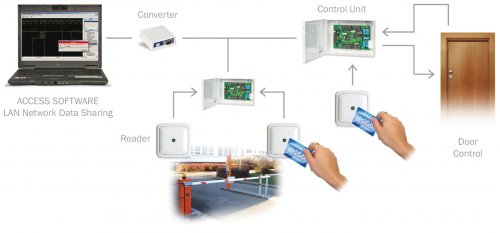

![PDF] Privacy protection based access control scheme in cloud-based services | Semantic Scholar PDF] Privacy protection based access control scheme in cloud-based services | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4409cb0b18485f7935d8596aae542d6646e3f1e4/2-Figure1-1.png)