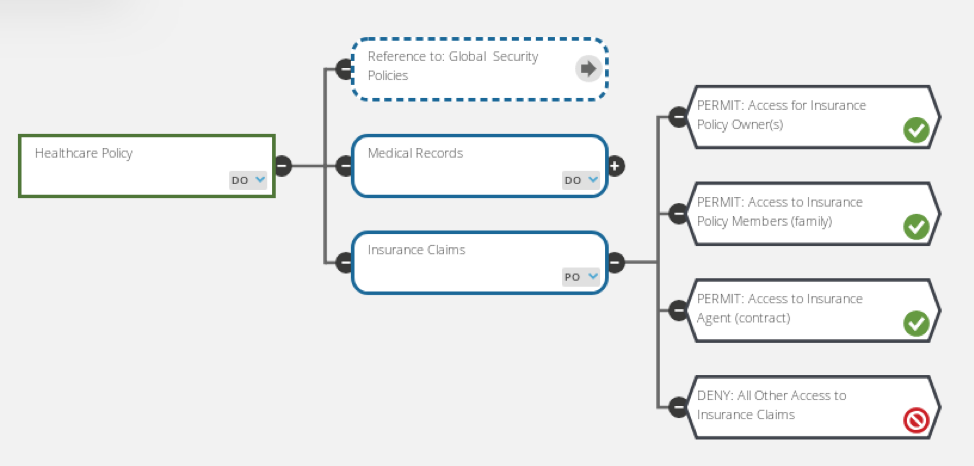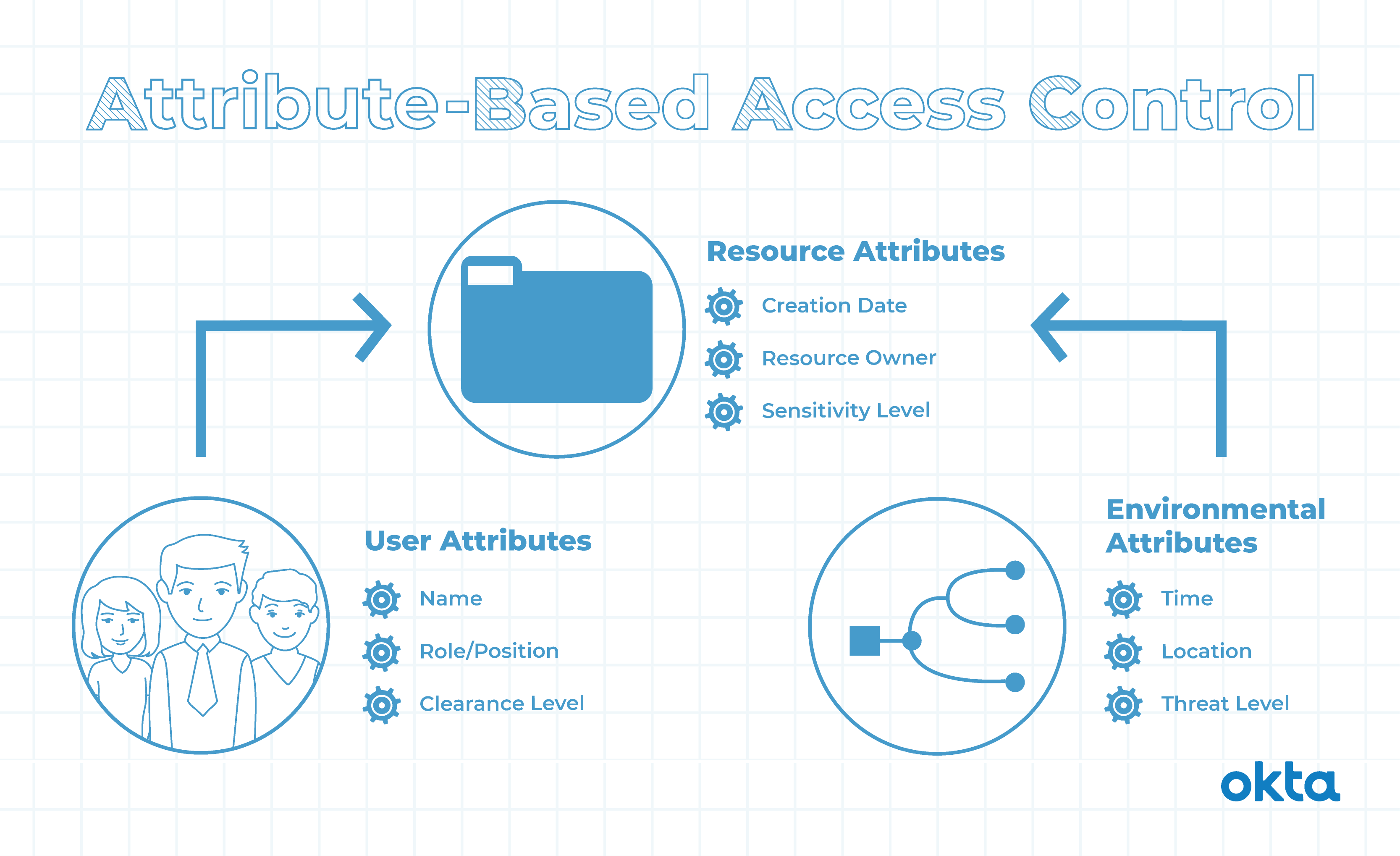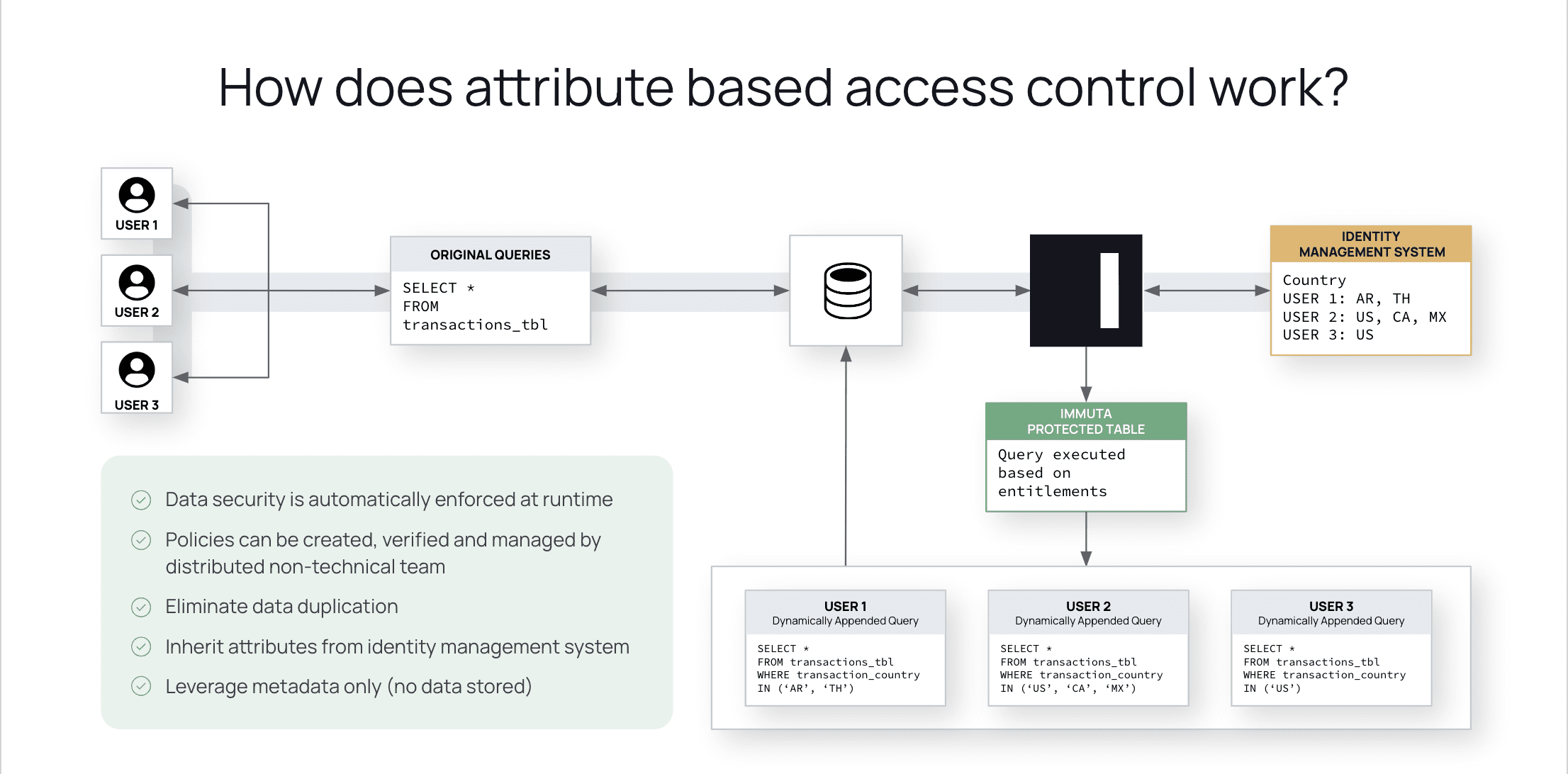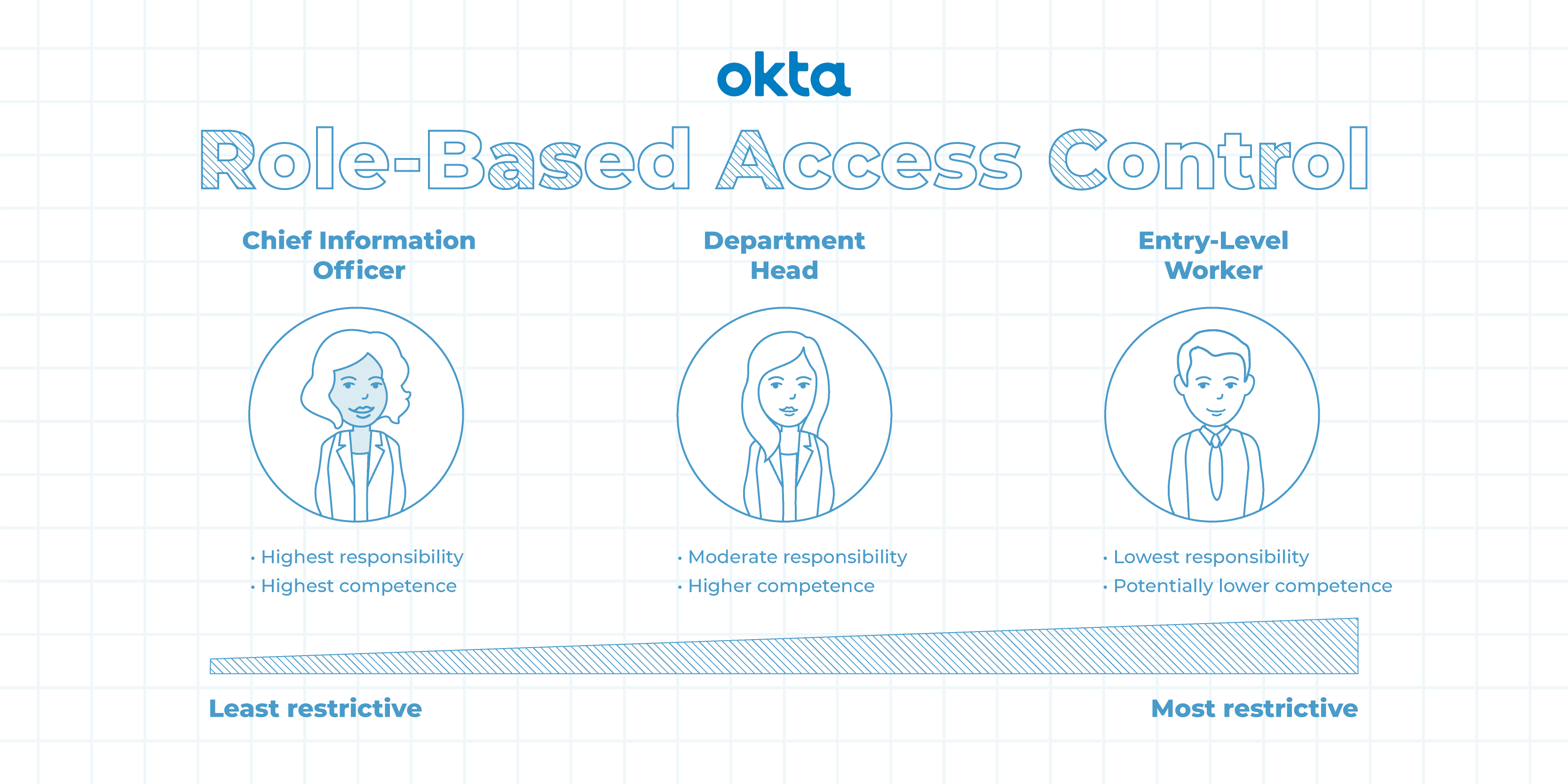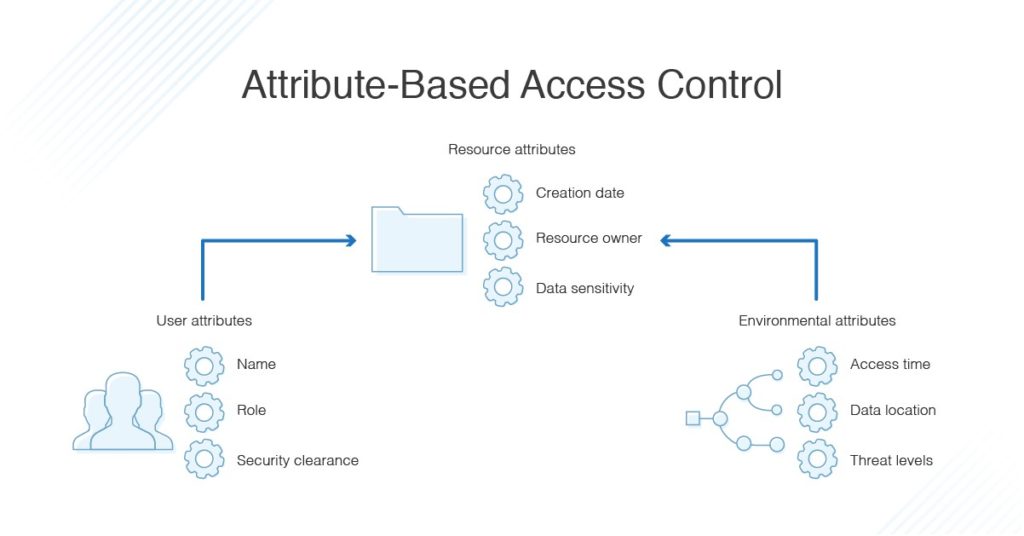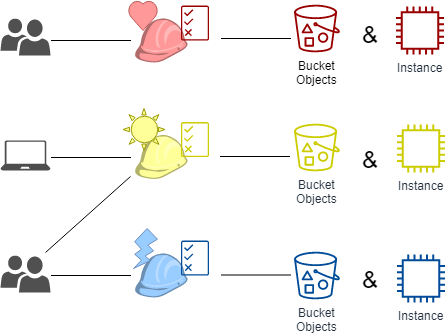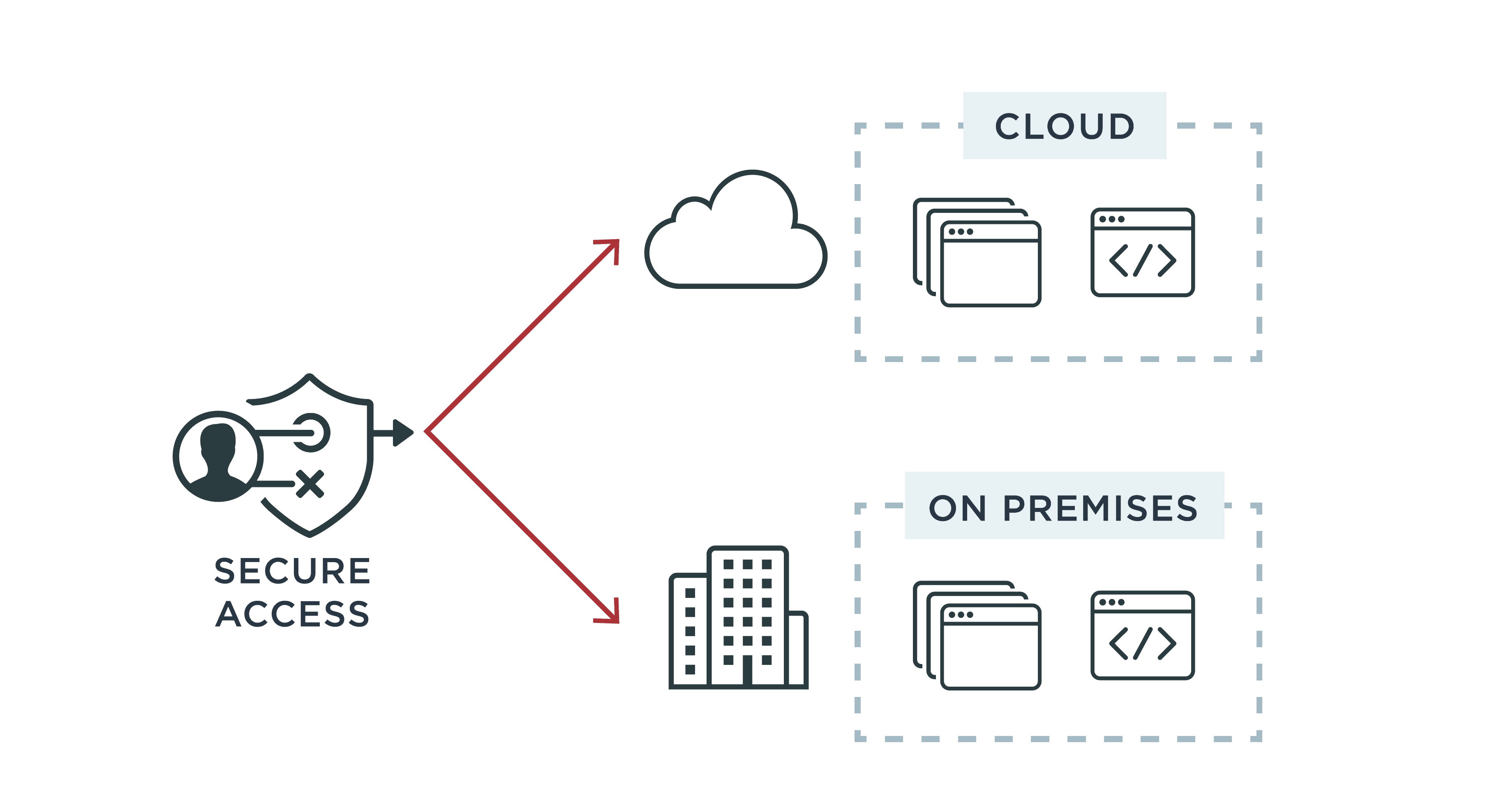
Rollenbasierte Zugriffskontrolle (RBAC) vs. Attributbasierte Zugriffskontrolle (ABAC): Was ist der Unterschied? | Ping Identity
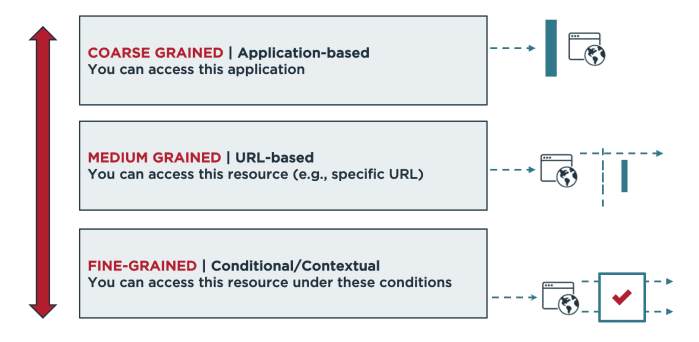
Rollenbasierte Zugriffskontrolle (RBAC) vs. Attributbasierte Zugriffskontrolle (ABAC): Was ist der Unterschied? | Ping Identity